Though mobile applications and operating systems are more secure than their desktop counterparts, they too require regular testing plans and robust security features. This becomes all the more evident when we talk about the mobile app development phase. Multiple areas need protection – local data storage, sensitive information, endpoint communication, authentication & authorization, code quality, network connections, etc. This is where the owasp mobile security testing guide provides a guideline for developers to safeguard their applications.
OWASP Mobile Security Testing Guide
The OWASP mobile security testing guide is a comprehensive manual enlisting the guidelines for mobile application security development, testing, and reverse engineering for iOS and Android mobile security testers. Let us take a quick look at the important factors, concepts, and techniques of mobile security testing.
OWASP Mobile App Testing Guide Requirements and Verification
THE OWASP mobile application security verification standard (MASVS) is a standard that is followed by software architects, testers, and developers to create secure mobile applications. Various scenarios are covered by different team members during the different phases of a project. Developers follow the security requirements outlined for development, testers follow the best practices and test cases to perform mobile app penetration tests and the teams can also follow compliance and ensure strict adherence to guidelines while working with vendors.
Mobile App Taxonomy
The term “mobile app” stands for any program that runs on a mobile device. There are some specific types of mobile apps as follows:
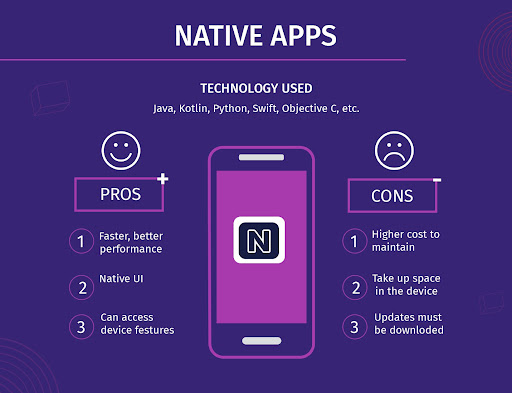
Native App
These apps are native to the system for which they are developed. They closely interact with the mobile device’s operating system. Hence, they can almost always directly access other components of a device like a camera, sensors, etc. They come with their own software development kit (SDK).
Source: CleverTap
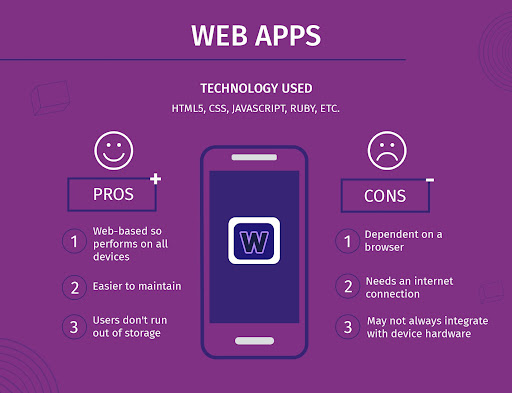
Web App
These are mobile web apps that run on top of a device’s browser and almost feel like a native app. They do not interact a lot with the device components and are in a way sandboxed in some sense.
Source: CleverTap
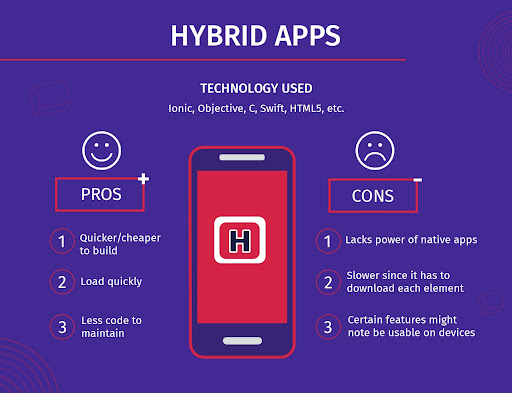
Hybrid App
These are a mix of native and web apps. They execute like a native app, but a portion of the app runs in an embedded web browser. Here, a web-to-native abstraction layer helps with relevant access controls.
Source: CleverTap
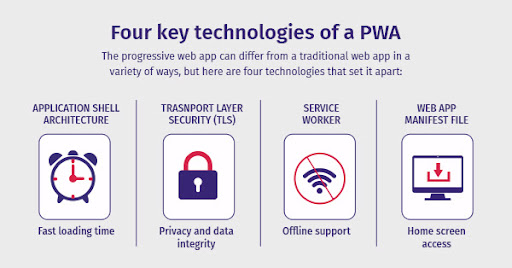
Progressive Web App
They look like regular web pages but come with the added advantage of allowing developers to work offline and gain access to the mobile device hardware. They combine different open standards available on the web to provide a better user experience.
Source: DEV
Mobile App Security Testing
Security testing of mobile applications has to be done throughout the phase of its development, right up until its release. Different types of tests are conducted. Let us take a look at them:
Black-box Testing
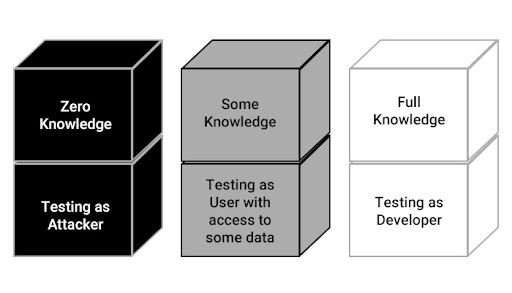
The tester behaves like a real attacker and explores all the possible combinations and use cases for publicly available and discoverable information. It is also called “zero-knowledge testing”
White-box Testing
The exact opposite of the above, here the tester conducts more sophisticated tests with knowledge about the vulnerabilities, fixes, source code, documentation, and diagrams. It is also called “full knowledge testing”
Gray-box Testing
Sandwiched between the two types mentioned above, here the tester is given some information (like credentials) while the other areas are usually hidden.
Vulnerability Analysis
Here, testers look for vulnerabilities in an app. Static analysis involves a detailed analysis of source code. It can be done manually or automatically. Dynamic analysis is more sophisticated since it is done during runtime. It helps testers look at specifics like vulnerable entry points, weak features, loopholes, etc.
Source: Zero2Infynite
Penetration Testing
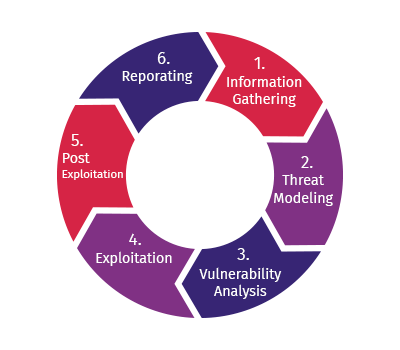
This testing is done at the final or near-final stages. It involves a thorough plan starting right from preparation, information gathering, and application mapping to the actual testing and reporting.
Mobile App Authentication Architectures
Authentication for mobile applications is important and comes into play when we speak about scenarios like user credentials (password, PIN), sensitive information (SIM, password generator, hardware token), biometrics (fingerprint, voice, retina), etc. Some specific authentication requirements are as follows:
- Username/password authentication is to be performed at the remote endpoint
- A password policy is to be enforced
- The second factor of authentication is to be enforced for sensitive apps
- User needs to be informed of recent account activities
When it comes to authentication architectures, two prominent methods are seen:
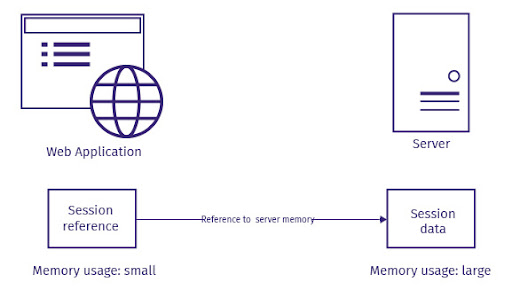
Stateful Authentication
A unique session id is generated for every session. For any new requests that come in, that session ID is used as a reference. Here, random session ids are created.
Source: Kenenth Choi – Medium.com
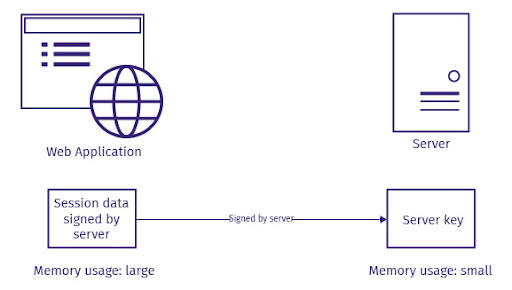
Stateless Authentication
All the information about a user is stored in a client-side token that is passed to a server. There is thus no need to maintain any session state on the server-side. These improve scalability and performance.
Source: Kenenth Choi – Medium.com
Testing Network Communication
All network-connected mobile apps use Hypertext Transfer Protocol (HTTP) or HTTP over Transport Layer Security (TLS) or HTTPS, to transmit data between remote endpoints. This is where network-based attacks could come up. One important strategy is to intercept HTTP(S) traffic by configuring a system proxy on the mobile device.
Cryptography in Mobile Apps
Cryptography helps secure the data of mobile applications by focusing on confidentiality, data integrity, and authenticity. Confidentiality takes the help of encryption and decryption to secure data. Data integrity ensures data consistency and identification of misuse or tampering of data. Authenticity focuses on validating sources and users. The major methods used to ensure data security are symmetric key encryption algorithms, public-key encryption algorithms, hashing technology, message authentication codes, signatures, and key derivation functions.
Testing Code Quality
Since different programming languages and frameworks are used by developers, the code’s quality is important. With multiple versions and upgrades coming up in the market, testing the quality of code helps ensure security right from the word go. Common vulnerabilities that can be looked at are SQL injection, XML injection, injection attack vectors, XSS flaws, buffer overflows amongst a host of others.
Tampering and Reverse Engineering
With attackers becoming smarter by the day, mobile app testing has also become more sophisticated. Disassembling compiled apps, applying regular security patches, and tampering with live processes and codes have become commonplace. Tampering is the process of changing a mobile application’s environment or behavior to test certain breakpoints and security loopholes. Reverse engineering focuses on extracting specific information about a source code and thereby undertaking a deep analysis of compiled apps. These two methods are important for black-box testing and enhanced security.
Android and iOS Testing Guides
A testing guide for Android and iOS covers major components like mobile platform details, details around different development stages of the application lifecycle, static & dynamic testing, reverse engineering & tampering, software protection guides, and detailed test cases. Developers and testers can refer to this guide to develop robust applications, test them thoroughly and also check for any attacks like reverse engineering. Since multiple developmental stages are covered, issues can be checked for and fixed more proactively to ensure better coverage. The detailed test cases provided also help replicate real-life scenarios and think like a hacker.
Approaches and Best Practices
Mobile application security is important but loads of options are available to move to a higher security posture. Some of the best practices are:
- Thorough assessment: Any testing starts with a good understanding of the environment
- Analysis of code quality/security: This helps start focusing on security by looking at the root of the issues
- Penetration testing: Here, test cases are run to depict real-life vulnerabilities which can be tapped into by attackers to gain access to data
- End-to-end device testing: All major devices and operating systems are covered here
- Complete planning and execution: All the steps right from preparation and execution to reporting, resolution, and retesting are taken into account
Being Prepared for the Future
Emerging technologies like IoT and AI have expanded the scope of cyber attackers. As more businesses get connected over the Internet, the scope is further widened. Automation means that new systems will interact with each other and access information on the go. Such complexity and connectivity can impact the vulnerability levels further. Bots have also been introduced to the mix now which means that attacks will be faster, more sophisticated, and much more difficult to detect and control. Malware sites have recently been found to be disguised with SSL certificates. These can easily fool users to think they are browsing safely. In the name of personalization, companies have been collecting user data. This is especially true for mobile users who are always on the move conversing and transacting. Companies need to up their security game to keep their customers happy yet safe while providing a personalized shopping experience. Phishing attacks are also on the rise.
But technology has also been keeping pace to deal with emerging issues. Machine learning-based mobile app security is likely to be a savior during such times. It could help monitor all activities in real-time and analyze enterprise data with much more efficiency, accuracy, and speed.
Runtime Application Self-Protection (RASP) also helps here by undertaking a real-time analysis of applications. Improved threat analytics of a good solution like AppSealing can ensure better coverage of attack vectors, so relevant actions can be taken swiftly. This means companies can now have an upper hand over the attackers.