The increasing focus on mobile devices in the workplace, aiming to achieve seamless connectivity and operational efficiency, necessitates the implementation of robust security measures to safeguard sensitive information against unauthorized access. The rise in work-from-home (WFH) and bring-your-own-device (BYOD) policies following the COVID-19 pandemic has undoubtedly enhanced productivity and flexibility, albeit at the expense of heightened security vulnerabilities.
According to the Verizon 2022 Mobile Security Index, a considerable surge has been observed in the number of organizations, with 45% experiencing security breaches associated with mobile devices. This marks a significant increase compared to the findings of the previous year. In the early part of 2022, AppSealing conducted a thorough analysis and assessment of a well-known vulnerability named StrandHogg. This vulnerability exploits the ‘taskAffinity’ attribute of Android applications, enabling malicious apps to assume any desired identity within the multitasking system.
The growing reliance on mobile devices amplifies the vulnerability to cyber attacks, as personal devices may lack the same level of security as those provided by companies. Consequently, these devices become susceptible to a range of security threats. It is crucial to comprehend and address critical vulnerabilities to bolster the security stance of mobile applications. This approach safeguards both user data and the overall integrity of the application.
The significance of implementing Mobile Threat Defense becomes increasingly apparent in this context. MTD solutions have been specifically developed to offer extensive security measures for mobile devices, safeguarding them against a wide range of potential threats. In the following sections, we will explore the importance of swift threat response, the enforcement of robust and standardized security protocols, and the essentiality of ensuring consistent protection, all of which are inherent components of MTD.
MTD is not just another security add-on. It’s required as a proactive and adaptive security layer, meticulously working to protect your mobile devices at various levels. Before that, let’s touch the basics first.
What is Mobile Threat Defense (MTD) or Mobile App Defense?
Mobile Threat Defense (MTD) is an advanced security solution meticulously crafted to deliver comprehensive protection against an array of threat vectors specifically aimed at mobile devices. MTD ensures continuous and on-device monitoring for both iOS and Android devices, enabling swift detection and mitigation of potential threats.
Mobile Threat Defense (MTD) utilizes advanced mechanisms to analyze the behavior of mobile apps and evaluate their risk levels. This rigorous assessment process guarantees that only secure and trustworthy apps are granted access to sensitive data. By doing so, MTD effectively safeguards mobile devices and their users from the constantly evolving landscape of both known and unknown threats.
Moreover, MTD goes beyond comprehensive protection against malware, spyware, and other malicious software. It also prioritizes secure network connections, ensuring the integrity and privacy of data transmission by preventing interception or tampering.
Why do you need Mobile Threat Defense (MTD)?
Mobile Threat Defense (MTD) is a comprehensive security solution that has a three-tier defense mechanism and offers a strong security shield, creating a safe environment for data and devices in the business ecosystem. In the subsequent sections, we will explore how MTD operates meticulously at three essential levels: device, applications, and network. Each level plays a critical role by offering a unique set of security features and functions, strengthening the defense against potential mobile threats.
Let’s delve into the intricate workings of Mobile Threat Defense, gaining a deeper understanding of its need, importance, and operation at each of these crucial levels.
Device-Level Security
At the device level, MTD is like a vigilant guardian, ensuring that applications on your device play by the rules and respect your privacy.
Data Leakage Detection: Mobile Threat Defense is always on the lookout for potential data leaks between apps. It understands that some apps might try to access data they shouldn’t, leading to unintentional data leakage. For example, a gaming app might try to access your contact list, which is unnecessary and risky. MTD identifies such attempts and blocks unauthorized access to safeguard your data.
Privacy Protection: Privacy is paramount, and Mobile Threat Defense takes it seriously. It monitors apps to ensure they don’t engage in activities that might compromise your privacy. If an app tries to access sensitive information without proper authorization, MTD steps in to prevent any potential privacy breaches.
Boundary Between Personal and Business Apps: Mixing personal and business data can be messy and risky. MTD ensures a clear distinction between personal apps and business-approved apps on a device. This way, your photos or messages won’t accidentally end up in your business emails or documents, and vice versa.
Controlled App Installation: Not all apps are created equal, and some might pose security risks. Mobile Threat Defense empowers IT departments by allowing them to control which apps can be installed on devices. If it doesn’t approve an app, it won’t make it through MTD’s strict screening process, ensuring that only safe and approved apps are installed.
An example: Consider a scenario where an employee attempts to download an unauthorized note-taking application that lacks approval from the IT department. While the app may appear harmless on the surface, it could harbor hidden security vulnerabilities or compromise privacy. By leveraging Mobile Threat Defense, the installation of such applications would be intercepted and prevented, thereby ensuring the protection of the device and any sensitive corporate data stored within it.
Application-Level Security
MTD at the application level provides a secure environment, ensuring that apps function as they should without jeopardizing the device’s security or the user’s privacy. At the application level, MTD takes on the role of a vigilant sentinel, meticulously monitoring applications to ensure they behave as expected and don’t pose any security risks.
Monitoring Unusual Activity: MTD keeps an eagle eye on all application activities, especially focusing on spotting anything unusual. For instance, if an app suddenly starts leaking data, Mobile Threat Defense is there to detect and stop it in its tracks.
Code Analysis: Think of MTD as a skilled detective who scrutinizes every line of code within an app. It’s on the lookout for grayware (software that behaves unethically but not maliciously) and malware (malicious software designed to harm devices). By analyzing the code, MTD ensures that the apps are clean and won’t harm the device or data.
Data Leakage Prevention: Data leakage is a serious concern, especially when apps start sharing data they shouldn’t. MTD steps in to prevent this unauthorized data access and sharing between apps. For example, it ensures that your photo app doesn’t share data with your business email app, maintaining a clear boundary between personal and business data.
Privacy Protection: Privacy is non-negotiable, and MTD works tirelessly to detect and prevent any privacy issues arising from app behaviors. It ensures that apps respect user privacy and don’t engage in activities that might compromise sensitive information.
Controlled App Installation: Some apps are like trojan horses, appearing harmless but causing chaos once installed. MTD tools empower IT departments by allowing them to control which apps can be installed on devices. If an app isn’t on the IT-approved list, it won’t make it onto the device, simple as that.
Example: In a hypothetical situation, consider an instance where an employee installs a calendar application that lacks business approval. It is worth noting that this application attempts to gain unauthorized access to the employee’s business emails. By deploying Mobile Threat Defense (MTD), this unapproved endeavor would be promptly detected, thereby thwarting any data breach. Additionally, MTD may even proactively impede the installation of the calendar app altogether, ensuring the utmost security for the employee’s device and preserving the integrity of business data.
Network Level Security
MTD at the network level ensures a secure and resilient connectivity environment, safeguarding data from the device to the cloud and everywhere in between. At the network level, MTD acts like a vigilant security guard, constantly monitoring and protecting data as it travels across networks.
Monitoring Known Threats: MTD is always on alert for known threats that might compromise network security. It actively scans network traffic, identifying and neutralizing threats before they can inflict damage.
Suspicious Activity Detection: If there’s any suspicious activity, like a sudden surge in data requests or unusual login attempts, MTD is on it. For example, in the case of man-in-the-middle (MitM) attacks, where a cybercriminal tries to intercept and possibly alter the communication between two parties without them knowing, MTD detects and thwarts these attempts to keep the data transmission secure.
Network Packet Analysis: MTD delves deep into network packets, scrutinizing each one for signs of malicious activity or anomalies. It’s like checking every car that enters a parking lot to ensure they have proper authorization and aren’t posing a threat.
SSL Stripping Detection: SSL stripping is a sneaky technique where a secure connection is downgraded to an insecure one, making it easier for attackers to snatch sensitive data. MTD is well-versed in identifying and preventing these attempts, ensuring that your data remains encrypted and secure during transmission.
Automatic Encryption on Open Wi-Fi: Open Wi-Fi networks are like open doors for cybercriminals. MTD automatically encrypts traffic on these networks, creating a secure tunnel for data transmission even in an open environment. So, if employees connect to a coffee shop’s Wi-Fi, MTD ensures their data is scrambled and unreadable to prying eyes.
Example: Imagine an employee accessing a corporate file through public Wi-Fi. Without protection, this connection could be susceptible to MitM attacks. However, with MTD in place, not only is the connection monitored for suspicious activity, but the data is also encrypted, safeguarding the information from potential eavesdroppers and attackers.
How to ensure Mobile Threat Defense (MTD)?
Securing the source code is fundamental in safeguarding mobile applications from potential threats. Here’s a brief overview of its significance:
Secure Coding
- Adopting Secure Coding Techniques: Engage both SAST and DAST tools. While SAST tools scrutinize the code for early detection of vulnerabilities and ensure it aligns with the set coding standards, DAST tools focus on identifying external security threats, providing a broad security net.
- Establishing a Code Protection Framework: Having a structured and clear code protection policy is crucial. This framework should encompass rules and procedures that underline the secure handling and protection of the code, reducing the likelihood of security breaches at various stages of development.
- Implementing Encryption and Continuous Monitoring: Encryption is vital for protecting data, and when combined with continuous monitoring, it significantly enhances the security of the source code. This duo acts as a deterrent for hackers, creating areas within the code that are inaccessible or invisible to them.
- Enhancing Code Through Obfuscation: Incorporate different obfuscation techniques to bolster code security. Techniques include translating sections of code into alternate forms that are difficult to interpret, thereby preventing unauthorized and malicious use of the code.
- Incorporating In-App Protection: Tools like AppSealing’s Runtime Application Self-Protection (RASP) offer invaluable insights into the precise sections of code that are vulnerable, allowing for timely modifications to rectify and enhance the security of the application.
- Utilizing Shielding Techniques: Shielding techniques modify the application code to make it tamper-proof, protecting intellectual property and ensuring compliance with various licensing and regulatory standards.
Integrity Protection
Integrity Protection is a crucial security feature that ensures that the components and modules within an application remain unaltered and authentic, safeguarding the app from malicious tampering and unauthorized modifications. The validation works as follows:
- Integrity Protection employs hash validation techniques for all app components and modules. Hash validation involves generating a unique hash value for each component and module during the app’s development phase.
- When the application runs, the generated hash values are compared with the current hash values of the components and modules. If there’s a mismatch, it indicates that the component or module has been altered, triggering protective measures.
Anti-Debugging And Anti-Decompile
Anti-debugging techniques are crucial for protecting applications from hackers who attempt to debug and reverse engineer the code. These techniques are designed to detect and prevent debugging attempts, making it challenging for attackers to understand and manipulate the application’s internal workings.
Three Key Techniques That You Should Know:
- Code Modification Detection: Debugging often involves altering the original code. Anti-debugging techniques can detect these modifications, providing an alert or activating defenses when debugging is identified.
- Exception Handling: If certain exceptions in the code are not executed as expected, it might indicate the presence of a debugger. Proper management of these exceptions is essential for effective anti-debugging.
- Self-Debugging: Applications can initiate a self-debugging process, creating a new process attached to the original debugger. If another debugger is detected, an alert is generated, providing an additional layer of protection.
Anti Memory Dump
A memory dump is a snapshot of what’s stored in a system’s memory, typically taken when there’s a system or application crash. This snapshot serves as a valuable tool for software developers and IT professionals, allowing them to delve deep into the issue and figure out what went wrong.
The memory dump is like a snapshot, providing insights into the operating system, applications, and various programs the moment right before they cease functioning or crash. This snapshot includes details like the data in memory locations, the status of various programs, program counters, and other relevant data.
This information is not only presented on the display but is also logged into a system file for future reference and analysis. Following a memory dump, the computer usually becomes unusable and needs to be restarted. Memory dumps might also occur when the system runs out of memory due to a memory leak, preventing it from continuing its operations.
Rooting Detection
From a Mobile Threat Defense (MTD) perspective, rooting is viewed critically due to the security risks it poses. Device manufacturers discourage rooting as it can lead to irreversible damage if not done correctly. Despite the risks, some Android users opt for rooting to unlock additional functionalities, such as enhanced customization options, improved battery life, better device performance, and the ability to update to the latest Android version.
Rooting essentially reinstates a standard Linux function that is usually removed from the device. The process of rooting involves incorporating a small file named ‘su’ into the device’s system. This file plays a pivotal role as it is designed to grant permissions, allowing a different user to execute commands. The acronym ‘su’ stands for ‘switch user’.
When this file is run without specifying additional parameters, it facilitates the transition of your user credentials from those of a regular user to those of a superuser. Being a superuser means having unrestricted access and control over the device, enabling you to add, remove, or modify any element and access functions that were previously inaccessible to a standard user.
However, from a security standpoint, rooting exposes the device to various threats. With root access, malicious actors can also gain elevated privileges, leading to the potential compromise of the device’s security and data integrity. Hence, rooting detection is a crucial aspect of MTD, ensuring that devices operating in a secure network environment are not rooted, maintaining the network’s overall security and integrity.
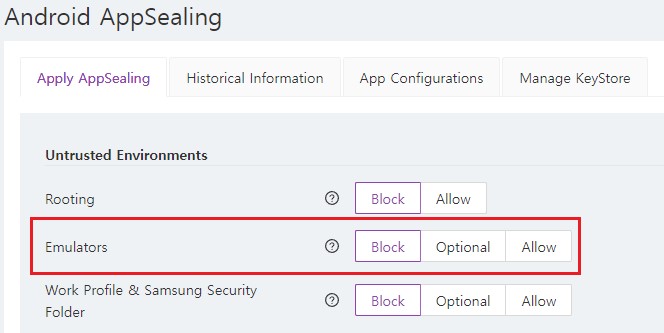
Android Emulator
Security is paramount, especially for apps handling sensitive data like those in fintech. While emulators are essential tools for developers, they are also exploited by attackers to find vulnerabilities. Regularly conducting emulator detection tests is crucial for mitigating threats and ensuring app and user security.
Some key Android Emulator Detection Techniques are explained as follows:
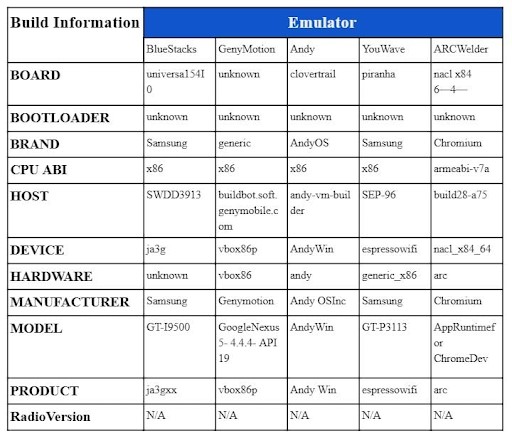
- Build Parameters: Emulators possess unique build properties distinguishable from actual devices. Parameters like Build.MANUFACTURER, Build.MODEL, and Build.HARDWARE are pivotal for detection.
- IMEI and IMSI Check: Emulators typically have hardcoded IMEI and IMSI values, which can be used for detection, though these can be altered with effort.
- Hardware-Based Detection: Emulators have different hardware configurations compared to real devices. Examining hardware specs can reveal inconsistencies indicative of emulator use.
- Networking Environment Detection: Emulators exhibit different network parameters due to running on computers, providing clues about the running environment. For instance, TTL values in emulators are often longer than in real devices.
Cheat Tools Detection
Cheat tools often attempt to modify application data and memory, which can lead to unauthorized and harmful alterations to the app’s functionality and user data. These malicious tools include macros, packet attacks, keyloggers, speed hacks, and memory attacks, which attackers use to modify apps or alter memory data.When an application is launched in an environment where cheat tools are installed, it is susceptible to various forms of manipulation and attacks, which might lead to unauthorized access, fraudulent transactions, and data breaches.
Proactive monitoring, blacklist management, and behavior analysis fortify mobile threat defense, further strengthened by integrating advanced technologies like Machine Learning and AI. This holistic approach not only ensures a secure transaction environment but also instills user confidence, safeguarding both data and financial assets against the ever-evolving threats of payment fraud. Some key approaches are:
Preventing Unauthorized Modification:
- Active Monitoring: The environment in which the application runs is continuously monitored for the presence of any cheat tools.
- Blacklist Utilization: A maintained blacklist of recognized cheat tools is utilized. If an installed tool from this list is detected, the application will promptly display a notification and terminate itself to prevent any compromise.
- Behavioral Analysis: The system also scrutinizes the behaviors and characteristics of crucial cheat tools. Upon identifying any malicious activity, it alerts the user and swiftly exits to prevent potential damage.
Network Packet Sniffing
Data transmitted over networks is divided into smaller units known as data packets at the sender’s end and reassembled at the receiver’s end. These packets are the smallest units of communication within a network. Packet sniffing is the practice of capturing these data packets as they travel across the network.
While this technique can be used legitimately to monitor network performance and troubleshoot issues, it’s also exploited by malicious actors to gather information about networks they plan to infiltrate.
3 Key Preventing Measures
- Data Encryption: Encrypting data transmitted over the network safeguards it from being intercepted and understood, even if captured.
- Secure Wi-Fi Use: Only connect to trusted and secure Wi-Fi networks to minimize the risk of packet sniffing.
- Regular Network Scans: Conducting regular scans helps identify and mitigate potential network threats and vulnerabilities.
Which Type of Business must have Mobile Threat Defense (MTD)?
In an era dominated by digital transformation, industries across the board are integrating mobile technologies into their operations. With this surge in mobile device usage, the need for robust Mobile Threat Defense (MTD) is paramount in some important sectors, each with distinct needs for mobile security.
Let’s look at them briefly.
- IT and Telecom: Holding the largest market share (20.92% in 2022), this sector is highly reliant on mobile devices and applications, making it imperative to secure sensitive data and communications from various mobile threats.
- Retail: Expected to expand at a significant CAGR of 29.4%, the retail industry uses mobile devices for various transactions and customer services, necessitating robust security measures to protect financial and personal data.
- Healthcare: With the increasing use of mobile devices for patient records and communication, healthcare providers need MTD to safeguard patient data and comply with privacy regulations.
- Banking, Financial Services, and Insurance (BFSI): Given the sensitive financial data handled, this sector requires stringent mobile security to prevent data breaches and fraud.
- Government: As governments promote digital platforms and smartphones, there’s a growing need for secure mobile solutions to protect citizen data and government communications.
- Manufacturing: With the integration of mobile devices in various manufacturing processes, securing these devices is crucial to protect intellectual property and operational data.
- Others (including Education, Energy, and Utilities): Other sectors also benefit from MTD due to the general increase in mobile device usage for various applications, each with specific security requirements.
Conclusion
Mobile Threat Defense (MTD) is indispensable in today’s digitally driven environment, where mobile devices are integral to various business operations. From safeguarding sensitive source code files to providing a secure environment free from malicious activities, MTD offers comprehensive protection at device, application, and network levels.
It actively monitors for anomalies, prevents data leakage, and secures data packets, crucial for industries like IT, Telecom, Retail, Healthcare, BFSI, Government, and Manufacturing. With the global MTD market poised for significant growth, adopting these robust security measures is imperative for businesses of all sizes to mitigate mobile-related threats and ensure data integrity and security in the evolving digital landscape.
Frequently Asked Questions
1. What is Mobile Threat Defense (MTD)?
MTD is a security solution designed to protect mobile devices from various threats. It offers dynamic protection against malicious apps, network attacks, and other threat vectors, providing continuous monitoring and security protocols for both iOS and Android devices.
2. Why is MTD crucial for businesses?
With the rise of mobile device usage in business operations, MTD is essential to secure sensitive data and applications. It provides holistic protection at the device, application, and network levels, safeguarding against data leaks, malware, and other threats, which is vital for business continuity and reputation.
3. How does MTD work at the application level?
At the application level, MTD monitors for unusual activities, such as data leaks, and analyzes code to check for malware and grayware. It aims to prevent data leakage between personal and business apps on a device and can restrict the installation of non-approved apps, enhancing data privacy and security.
4. Which industries benefit most from MTD?
Industries like IT and Telecom, Retail, Healthcare, BFSI, Government, and Manufacturing significantly benefit from MTD. These sectors often handle sensitive data and require secure mobile solutions to protect against data breaches and ensure secure and seamless operations.
5. How can businesses implement MTD?
Businesses can implement MTD by integrating MTD solutions into their security infrastructure. These solutions offer features like code protection, integrity protection, anti-debugging, rooting detection, and network packet sniffing protection. Adopting MTD tools and following best practices for mobile security can provide robust protection against mobile threats.
6. What is the difference between mobile threat defense and MDM?
Mobile threat defense (MTD) focuses on protecting mobile devices from cyber threats through prevention, detection, and response, while Mobile Device Management (MDM) primarily involves managing and securing mobile devices, including configuration, app management, and device monitoring. MTD is specifically designed to detect and combat mobile-specific threats, while MDM is more focused on overall device management.
7. What is threat protection on a phone?
Threat protection on a phone involves taking precautionary measures to safeguard the device from cyber threats. This includes installing security software to prevent malware and viruses, activating two-factor authentication, and being cautious with electronic messages, social media posts, and emails to avoid potential threats. If a threat is received, it’s important to save the information, record the message if possible, and report it to law enforcement.
8. What is the MTD app?
The MTD app is a mobile threat defense application that detects and alerts users and system administrators to potential security threats on mobile devices. It uses the device’s APIs to gather information about threats like suspicious apps or networks. MTD protects against attacks made specifically for mobile devices and operating systems, such as Apple iOS and Google Android, including malware, phishing, and network attacks.
9. What is MDM used for?
Mobile device management (MDM) is a type of security software that enables organizations to secure, monitor, manage, and enforce policies on employees’ mobile devices. Its core purpose is to protect the corporate network by securing and optimizing mobile devices, including laptops, smartphones, tablets, and Internet-of-Things (IoT) devices.
10. What are two main mobile threats?
The two main mobile threats are data leakage via malicious apps and man-in-the-middle (MitM) attacks. Data leakage occurs when unsecured apps on employees’ devices compromise enterprise security, while MitM attacks involve intercepting and possibly modifying network communications, with mobile devices being particularly vulnerable to this type of attack.