As of 2022, Android remained the leading mobile operating system in the world, with around 71% of users. Add to that the fact that over 3 million apps are on the Google Play Store, and around 82% of Android devices are susceptible to at least one out of 25 vulnerabilities in the Android OS. And how do attackers go about finding vulnerabilities in an Android app? Using emulators.
Developers often use emulators to test and improve apps. However, a hacker can understand, analyze, and reverse engineer the application by installing and running an Android app on the Android emulator. This enables them to decode the app’s file structure, working procedure, and codebase and eventually identify vulnerabilities they can exploit. In some cases, developers allow their apps to run on emulators so that they can be tested, and attackers exploit this fact.
And that brings us to the crux of this article – Android emulator detection. There are ways to identify if your app is being run on an emulator, and this article will cover these different techniques.
Android Emulator Detection
Here are some popular Android emulators:
- Android Studio’s emulator
- Andy
- ARChon
- ArcWelder
- Bouncer
- BareDroid
- Bluestacks
- Droid4X
- DroidDolphin
- Genymotion
- KoPlayer
- MEmu
- Nox
- PrimeOS
- Remix OS Player
- Xamarin
- YouWave
Your app could be running on any of these emulators. There are a couple of signs that you can look for that indicate your app is running on an emulator. Emulators have specific files, parameters, and characteristics that are constant and always located in the exact location.
Looking for these properties is generally the best way to detect Android emulators. Here are a few ways to detect if your Android app is being run on an emulator:
Using Build Parameters
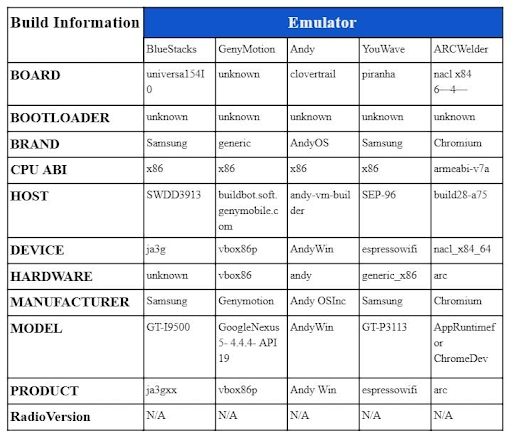
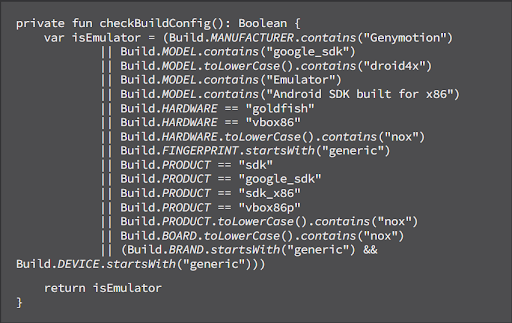
The quickest way for Android emulator detection is by analyzing build values under BuildConfig. Emulators have unique build properties that are different from a smartphone and can be identified:
For example, you can use parameters like Build.MANUFACTURER, Build.MODEL, Build.HARDWARE, and so on for emulator detection:
Since the build values for an emulator are different from that of an actual Android device, it is often the first technique used to detect if an app is being run on an emulator.
IMEI and IMSI Check
The values of IMEI and IMSI in an emulator are hard coded to “000000000000000”, NULL. This is another way of Android emulator detection.
Bear in mind there are ways to change an emulator’s IMEI and IMSI values (although the methods are highly complicated, and attackers don’t generally go through this much effort), so don’t let this be the only test you perform.
If the output of an IMEI and IMSI is null (the values listed above), you can be sure the app is running on an emulator.
Hardware-Based Detection
Similar to having different build parameters, emulators also have different hardware configurations (as compared to an actual Android device). Here are the default hardware values for some common emulators:
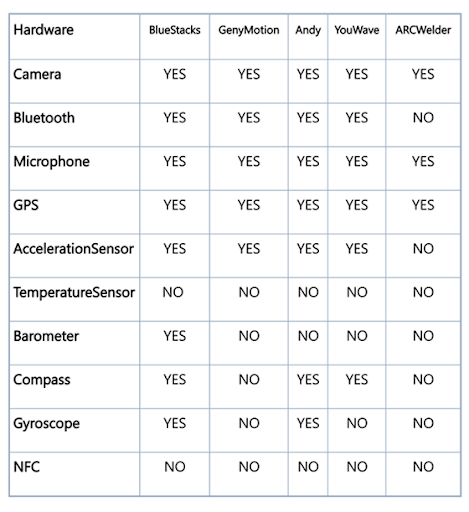
You can query the hardware specs during the emulator detection test and look for these inconsistencies. This is an excellent test to run alongside the BuildConfig test since these two parameters give you the most insight into the app’s environment.
Networking Environment Detection
Lastly, you can get clues about the environment (Android device or emulator) an app is running in by analyzing specific network values, like the MAC address. Since emulators run on a computer, they will have different network parameters (some, if not all). For example, the PC can connect to the internet via LAN (something a smartphone cannot do), whereas mobile devices use a radio interface to connect to the internet. Identifying network parameters can give clues as to which environment the app is running on.
You can also analyze the TTL (time-to-live) value to detect an emulator. Emulators have longer TTL values than actual devices, often a clear telltale sign you can use in Android emulator detection.
Final Thoughts
Ensuring an app is secure and its users are safe is an enterprise’s first and utmost priority. Security becomes especially critical when sensitive data is involved, for example, in the case of fintech apps.
The security checks for emulator detection listed in this article are not the only ones, but they are an excellent place to start. Remember, emulators are not inherently wrong; they are a perfect tool for testing Android apps and detecting and fixing bugs. Using emulators by hackers to find vulnerabilities to exploit is the issue, and running Android emulator detection drills regularly is a way to mitigate this threat.