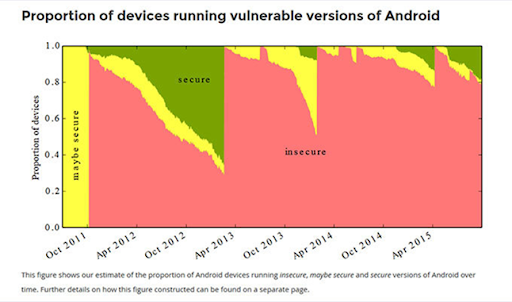
Nearly four out of five Android devices are susceptible to at least one of 25 vulnerabilities in the Android operating system, according to a new study. With mobile application security assessments (MASA), you could secure your enterprise by identifying potential vulnerabilities in your publicly available apps. These assessments test for various security risks, including data leakage, unauthorized access, and malicious code injection.
Mobile Application Security Assessments
From data breaches and loss of control to Legal and regulatory compliance issues, unsecured mobile apps keep challenging the baseline security criteria for developers. Mobile app vulnerabilities, be they Android or iOS, can be exploited by attackers to gain unauthorized access to sensitive data, steal personal information, or perform other malicious actions.
Result? Ask T Mobile. It cost $350 million. The recent T-Mobile data breach came to mind when hackers exploited a vulnerability in an API (Application Programming Interface) connected to T-Mobile’s third-party vendor.
By conducting regular security assessments, you can ensure that your mobile apps are safe and secure for your users. A mobile application security assessment aims to analyze the application’s code, architecture, and configuration to identify vulnerabilities and prioritize mitigation from potential attack vectors.
- Code review: Examining the application’s source code for known vulnerabilities, insecure coding practices, and other security issues.
- Static analysis: Analyzing the application’s binary code (i.e., the compiled version of the source code) without executing it to identify potential vulnerabilities.
- Dynamic analysis: Running the application on a mobile device or emulator and interacting with it to identify vulnerabilities. This can include manual testing and automated tools that simulate various types of attacks.
- Penetration testing: Attempting to exploit vulnerabilities in the application using manual and automated techniques to determine the potential impact of a successful attack.
- Configuration review: Examining the application’s settings and configuration files to ensure they are secure.
- Code-level vulnerabilities: These include insecure coding practices, such as the use of hard-coded credentials or the failure to validate user input.
- Configuration vulnerabilities: These include misconfigured settings or the use of default configurations that could lead to security weaknesses.
- Data storage vulnerabilities: These include the failure to encrypt sensitive data or the storage of sensitive data in an insecure location.
- Permission vulnerabilities: These include excessive or unnecessary permissions that could lead to the app having access to sensitive data or functionality it does not need.
- Network vulnerabilities: These include the failure to secure network connections or the use of weak encryption properly.
Mobile application security assessment also gains more importance for client-side security and effective and strong authentication systems on the Cloud to mitigate future liability.
By identifying and addressing these vulnerabilities, organizations can improve the security of their mobile apps and protect sensitive data.
Source: Kaspersky
Google Play Data Safety Requirements
Google has a set of data safety requirements for apps distributed through the Google Play Store. These requirements are designed to protect users’ data and ensure that apps on the store do not compromise users’ security.
The Google Play Developer Policy Center states that all apps must follow the data safety requirements, which include:
- Protecting user data: Developers must protect user data by properly securing any data collected and stored and disclose what data is collected and how it is used.
- Handling personal and sensitive information: Developers must not collect or share personal or sensitive information unless it is essential for their app’s functionality. Personal information includes things like name, email address, or phone number. Sensitive information includes things like financial information or location data.
- Using Google Play Services and APIs: Developers must use Google Play Services and APIs in compliance with their policies and guidelines.
- Handling payments and transactions: Developers must use Google Play’s in-app billing service for in-app purchases and comply with all relevant laws and regulations for handling payments and transactions.
- Handling user-generated content: Developers must have a policy in place for moderating user-generated content and promptly remove content that violates the developer’s policy or is illegal.
- Keeping apps up-to-date: Developers must keep their apps up-to-date to address security issues and other vulnerabilities.
- Transparency: Developers must be transparent in their data collection and usage practices and provide a privacy policy that clearly explains what data is collected, how it is used, and who it is shared with.
Google’s requirements also include the handling of users’ location data. App developers must follow the guidelines of the Google location services policy, which states that apps should not request location data unless necessary for the app’s functionality. Apps must also provide clear and conspicuous disclosure of their data collection practices and obtain user’s explicit consent before collecting location data.
Mobile Application Security Assessment (MASA) Validation
There is a context of The App Defense Alliance (ADA), which was formed by Google in partnership with several mobile app security vendors in February 2019. The App Defense Alliance (ADA) is a coalition of mobile app security vendors, formed by Google in partnership with several mobile app security vendors in February 2019. The goal of the ADA is to improve the security of the Google Play Store by working together to identify and remove malicious apps. Members of the ADA use their respective technologies and expertise to identify potentially harmful apps, and then work together to remove them from the Google Play Store.
On the other hand, Mobile Application Security Assessment (MASA) validation is a process used to assess the security of mobile applications. The goal of MASA validation is to identify vulnerabilities and security risks in mobile apps, and to provide recommendations for addressing those risks before the app is made available to the public in the Google Play Store or any other app stores.
MASA validation, or Mobile Application Security Assessment validation, is a process used to assess the security of Android apps submitted to the Google Play Store.The goal of MASA validation is to identify vulnerabilities and security risks in an Android app and to provide recommendations for addressing those risks before the app is made available to the public in the Google Play Store.
With the OWASP MASVS (Mobile App Security Verification Standards) guideline, mobile app developers build security into their apps from the design stage and make sure that security professionals test for a wide range of potential threats.
Riding high on the OWASP Mobile Application Security Verification Standard (MASVS) L1 Mobile Application Security Assessment (MASA) Validation, thrives on a set of security requirements that are intended to be used as a guideline for mobile app developers and security professionals to ensure that mobile apps are built with a strong security foundation.
MASVS L1 covers a wide range of security topics, and it is divided into six categories with 32 requirements in total:
Data Storage and Protection:
This category covers the secure storage of sensitive data on the device and the server, such as user credentials, financial information, and other personal data. Requirements in this category include encrypting sensitive data, protecting data in transit, and securely managing keys.
Network Communication:
This category covers secure data communication between the mobile device and the server, including secure protocols and encryption. Requirements in this category include verifying SSL/TLS certificates, using certificate pinning, and encrypting data in transit.
Authentication and Session Management:
This category covers users’ secure authentication and authorization, including multi-factor authentication and the protection of session data. Requirements in this category include implementing strong authentication, protecting session data, and using a secure session management scheme.
Cryptography:
This category covers using cryptography to protect data and communications. Requirements in this category include using a suitable cryptographic algorithm, securely managing keys, and using a secure key generation process.
Code Quality and Build Settings:
This category covers secure coding practices and the protection of app binaries and resources to prevent tampering. Requirements in this category include using secure libraries, preventing common vulnerabilities, and using code obfuscation and hardening techniques.
Resilience against Reverse Engineering and Tampering:
This category covers the app’s techniques for resilience against reverse engineering, tampering, and debugging. Requirements in this category include protecting against debugging and reverse engineering, using anti-tampering techniques, and using runtime application self-protection (RASP).
Mobile Application Security Testing
Mobile Application Security Testing (MAST) identifies vulnerabilities and security risks in mobile applications. The goal of MAST is to identify any potential security weaknesses in the app that cybercriminals could exploit and provide recommendations for addressing those risks.
There are several different types of mobile application security testing, including:
Unit Testing:
This testing focuses on individual units or components of the mobile app. The goal of unit testing is to ensure that each unit or component of the app is functioning correctly and that there are no security vulnerabilities.
Factory Testing:
This testing is performed on the entire mobile application in a controlled environment. Factory testing aims to ensure that the app is functioning correctly and that there are no security vulnerabilities in the finished product.
Certification Testing:
This testing is performed to ensure that the mobile app meets specific security standards and regulations. Certification testing is often required for apps that handle sensitive information, such as financial or personal information.
Application Testing:
This type of testing evaluates the functionality and security of a mobile application by simulating real-world usage of the application. This includes testing the application on multiple devices, platforms, and network conditions.
Talking about the process of MAST, typically involves several steps, including:
- Planning and Preparation: The first step in MAST is to plan and prepare for the testing process. This includes identifying the scope of the testing, determining the goals and objectives, and identifying the mobile platforms and devices that will be tested.
- Analysis: The mobile application is analyzed to identify potential vulnerabilities and security risks in this step. This can include reviewing the app’s source code, analyzing its network traffic, and testing its functionality.
- Vulnerability Identification: During the analysis, vulnerabilities and security risks are identified, such as unsecured data storage, insecure communication, and lack of encryption.
- Risk Analysis: After the vulnerabilities have been identified, a risk analysis is performed to assess the likelihood and impact of each vulnerability.
- Exploitation: After identifying the vulnerabilities, the next step is to try to exploit them to determine their potential impact.
- Reporting: The final step in MAST is to document and report the findings of the testing process. This includes providing detailed information about the identified vulnerabilities and the recommended steps for addressing those vulnerabilities.
- Remediation: Based on the report, the developer will then work to implement the recommended changes and remediate the identified vulnerabilities.
- Re-testing: After the remediation, a re-testing process is performed to ensure that the vulnerabilities have been properly addressed and that the mobile application is now secure.
It’s important to note that mobile app security should be an ongoing process, not just a one-time assessment, as new vulnerabilities and threats may arise over time.
Top Mobile App Security Testing Tools
Many mobile application security testing tools available can help identify vulnerabilities and security risks in mobile apps.
Here are ten popular mobile app security testing tools:
OWASP Mobile Security Testing Guide (MSTG)
This open-source mobile app security testing guide provides a comprehensive set of guidelines for testing mobile apps.
OWASP Mobile Security Testing Framework (MSTF)
This is an open-source framework that provides a set of tools for testing mobile apps.
Burp Suite
This is a popular web application security testing tool that can also be used to test mobile apps.
AppScan
This is a mobile app security testing tool that can be used to identify vulnerabilities and security risks in mobile apps.
Mobile App Attestation
This is a security testing tool that can ensure that a mobile app is running on an authorized device.
XCUITest
This is a mobile app security testing tool that can be used to automate UI testing for iOS apps.
Appium
This is an open-source mobile app security testing tool that can be used to automate the testing of Android and iOS apps.
MobSF
This is an open-source mobile app security testing tool that can be used to perform automated security testing of mobile apps.
Drozer
This is a mobile app security testing tool that can be used to identify vulnerabilities and security risks in Android apps.
iXGuard
This is a mobile app security testing tool that can be used to identify vulnerabilities and security risks in iOS apps.
How AppSealing Makes Mobile App Security Holistic and Effective?
It’s worth noting that no single tool can provide comprehensive security coverage and it’s important to use multiple tools to get comprehensive security for your mobile app.
The AppSealing mobile app security platform is a cloud-based, pay-as-you-go solution that helps developers and companies secure their mobile applications in real-time. AppSealing is a robust tool that offers a variety of features to help keep your app safe, including instant security alerts, regular scans, and more. Take a Test Demo today!