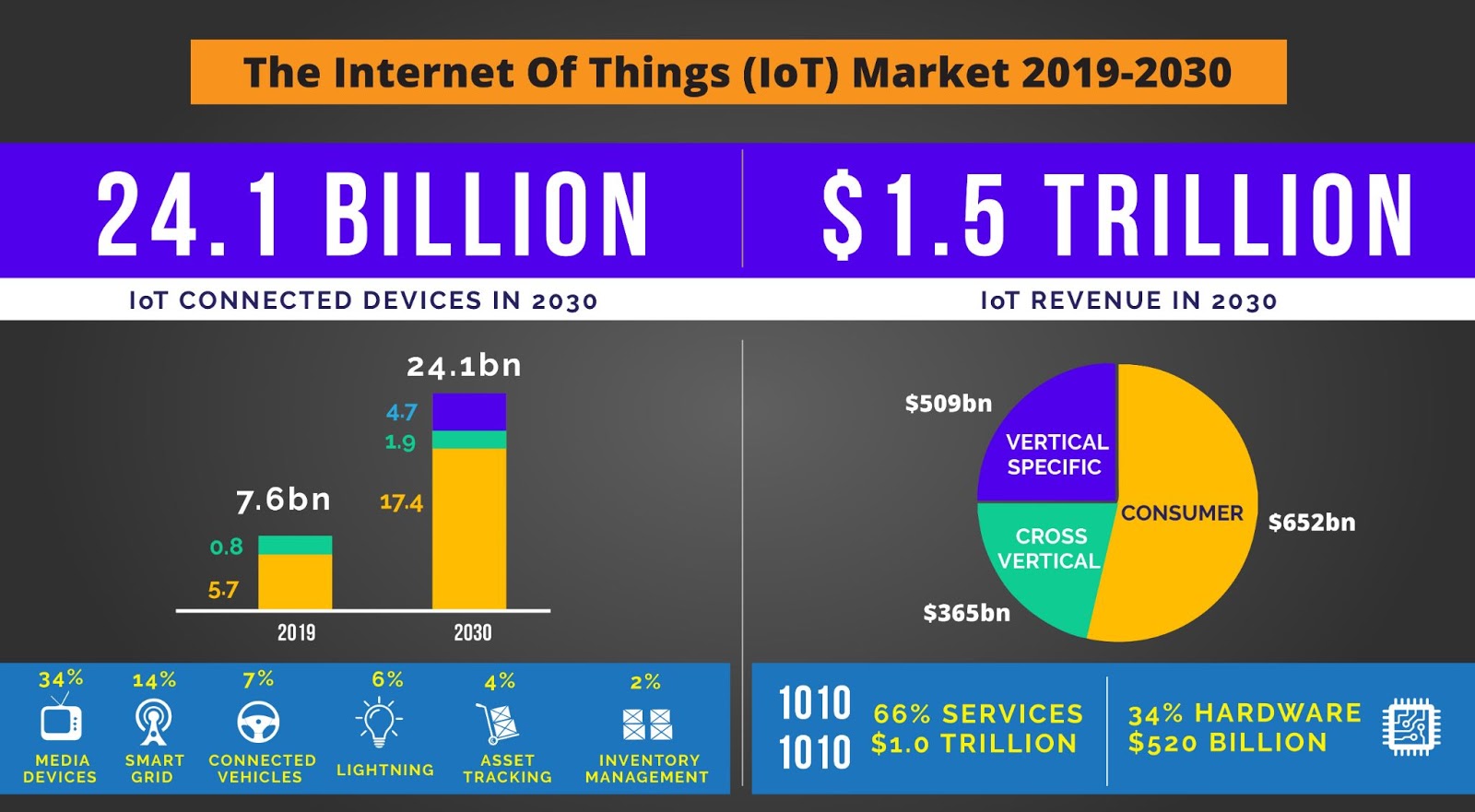
IoT has moved past the stage of being ‘something that could shape our future’. It is shaping our present, actively. The seamless management of data for real time monitoring, automation and optimization of workflows that IoT facilitates has found many admirers. And its acceptance and applications are growing every second – there are currently more than 10 billion IoT devices today. Fitness, healthcare, telecommunications and retail are some of the industries that have witnessed major transformation owing to the IoT boom. According to a 2020 report, the worldwide spending on IoT will have a CAGR of 11.3% in 2021.
With the IoT market expanding at an exponential rate, security continues to be a major concern. While only 16% of IoT devices were subjected to cyber attacks in 2019, the number rose to 33% in the year 2020. The rising attacks are testament to the lack of security compliance and the increasing sophistication of hackers.
Lack of security defeats the whole purpose of having an advanced data transfer and management system and leads to operational risks and financial losses. An attack on any of the connected IoT devices can compromise the security of the entire network. Hence, IoT Manufacturers need to adopt a security-focused approach to thwart attacks and maximize its full potential.
The widely revered Open Web Application Security Project (OWASP) with an aim to promote a secure digital ecosystem has listed the OWASP IoT top 10 vulnerabilities to assist manufacturers, enterprises and consumers to better understand the security threats lurking within the internet world. Let’s understand what this list is, what it means for IoT security, and how we can work around it to enforce stronger security.
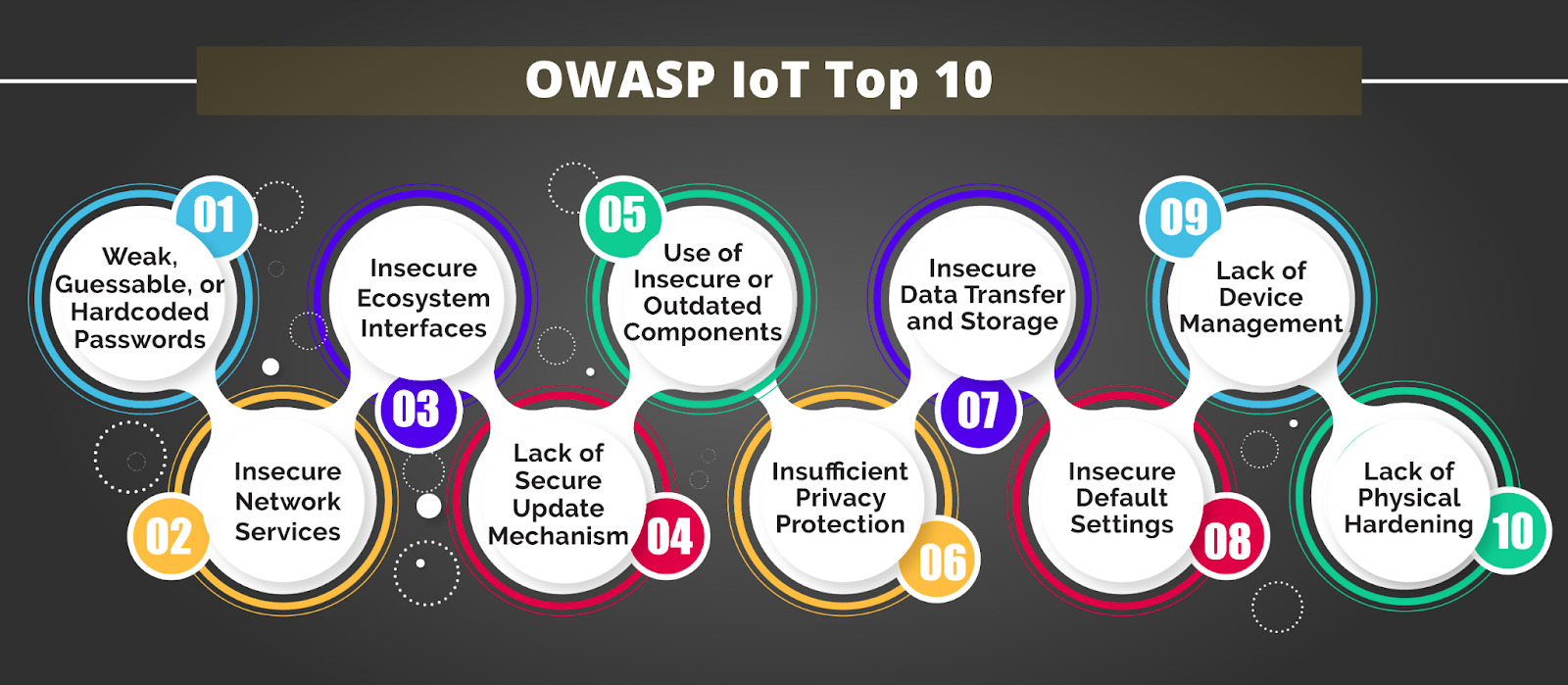
OWASP IoT Top 10
OWASP IoT Top 10 is an online publication that gives insights into the security loopholes present in the system. Security experts across the globe have collectively identified these threats after a thorough review of the existing state of affairs. The report aims to educate the developers and enterprises on the prevalent risks and vulnerabilities to take corrective actions and tighten security before the launch of the product.
OWASP prepares the top 10 list after evaluating the cyber attacks on the basis of ease of exploitability, the severity of the vulnerabilities, detectability and the magnitude of the potential impacts. Here is the latest OWASP IoT top 10 that lists vulnerabilities every manufacturer must take into account before creating smart devices.
1. Weak, guessable or hard coded passwords
IoT devices with weak default passwords are prone to cyber attacks. IoT device manufacturers must pay attention to password settings while launching the device. Either the device doesn’t allow the users to change the default password or the users prefer not to change it even if they can. Moreover, a successful attempt to gain unauthorized access into one device leaves others in the system vulnerable as IoT devices often share the same default passwords.
2. Insecure network services
Network services running within the device can pose a threat to the security and integrity of the system. These, when exposed to the internet, pave way for unauthorized remote access and data leak. Attackers can successfully jeopardize the security of an IoT endpoint by taking advantage of the weaknesses present in the network communication model.
3. Insecure ecosystem interfaces
There are several interfaces like web interface, the backend API, the cloud, and the mobile interface that enable smooth user interaction with the device. However, lack of proper authentication, poor encryption and data filtering can adversely impact the security of IoT devices.
4. Lack of secure update mechanisms
The inability of the device to securely update is the fourth vulnerability in the list. No firmware validation, unencrypted transfer of data, absence of anti rollback mechanisms, lack of security update notifications are the reasons for compromised security of IoT devices.
5. Use of insecure or outdated components
This implies the use of third party hardware or software that have risks associated with it and threatens the security of the entire system. The industrial internet of things (IIoT) is particularly affected by systems that are difficult to update and maintain. Such vulnerabilities can be leveraged to launch an attack and disrupt the smooth functioning of the device.
6. Insufficient privacy protection
IoT devices may have to store and retain sensitive information of users to function properly. However, these devices often fail to offer a secure storage which leads to leakage of critical data when hacked by cyber criminals. In addition to devices, the manufacturer’s databases are also prone to attacks. An encrypted traffic is still prone to threats as there have been instances where passive observers could also extract information.
7. Insecure data transfer and storage
The lack of encryption while handling sensitive data either during transmission, processing or at rest is an opportunity for hackers to steal and expose data. Encryption is must wherever transfer of data is involved.
8. Lack of device management
This refers to the inability to effectively secure all the devices on the network. It exposes the system to numerous threats. Irrespective of the number of devices involved or their size, each one of them needs to be protected against data breach.
9. Insecure default settings
The existing vulnerabilities in the default settings expose the system to an array of security issues. It might be fixed passwords, inability to keep up with the security updates and presence of outdated components.
10. Lack of physical hardening
Lack of physical hardening can easily help users with malicious intent to gain remote control over the system. Failure to remove debug ports or removal of the memory card can expose the system to attacks owing to lack of physical hardening.
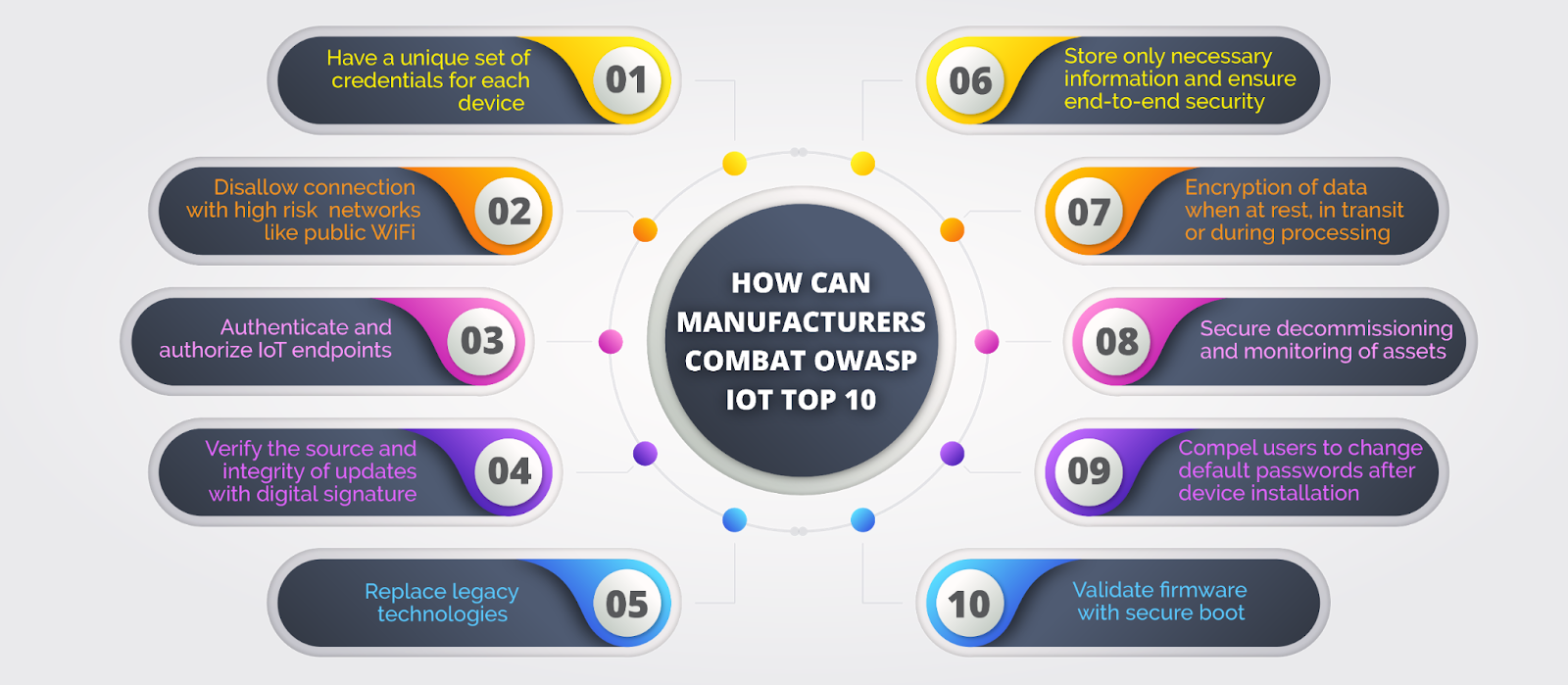
What can manufacturers do to combat IoT vulnerabilities?
The threat of OWASP IoT Top 10 vulnerabilities could be mitigated to a large extent if manufacturers implement best practices to tackle them. Here’s an overview of that.
1. Weak, guessable or hardcoded passwords
To combat the first vulnerability listed by OWASP, manufacturers must take the following steps:
- Every device must have a unique set of credentials
- Disable weak passwords
- Removing backdoors created during debugging
2. Insecure network services
To prevent threats arising from insecure network services, manufacturers should:
- Use secure protocols like HTTPS, sFTP, and SSH
- Disable non-essential ports and services that provide remote access
- Keep IoT devices on a separate network
- Installation of regular updates
3. Insecure ecosystem interfaces
To address insecure interfaces, the following tips are useful:
- Adhering to the principle of least privilege
- Block public access to S3 bucket
- Strong authentication of IoT endpoints
4. Lack of secure update mechanisms
For secure delivery of updates to IoT devices, manufacturers must:
- Only implement updates that are digitally signed
- Implement anti-rollback mechanisms
- Secure and verify access to updates
5. Use of insecure or outdated components
IoT manufacturers are advised to :
- Refrain from legacy technologies
- Ensure continuous tracking of hardware and software components
- Immediately replace any of the components that turn obsolete
6. Insufficient privacy protection
Consumer privacy is one of the key concerns that need to be addressed with the following measures:
- Limit the storage of personal data on devices
- Frame a data protection policy for your organization
- Prepare an incident response plan to combat any breach of security in the future
7. Insecure storage and transfer of data
To ensure maximum protection of data, IoT manufacturers need to implement the following for complete security:
- Ensure encryption at all levels
- Strictly utilize secure channels like HTTPS, sFTP and SSH
- Opt for one-time-use keys that aren’t stored in the device
8. Lack of device management
There is an increased risk of attacks if there are several devices with weak security functioning within the same system. The following steps must be implemented for flawless device management.
- Secure decommissioning, endpoint quarantine and blacklisting
- Integrate devices with asset management, bug tracking and patch management systems
- Build an interface that is flexible and seamlessly integrates with other systems
9. Insecure default settings
The following 3 tips can enable IoT manufacturers to thwart the risks associated with weak default settings:
- Use only secure default settings
- Grant users permission to change default passwords
- Prompt users to change their default passwords compulsorily
10. Lack of physical hardening
To counter physical threats to IoT devices, manufacturers should:
- Understand how a user may modify the device
- Proactively anticipate what damages any user may inflict on the device
- Devise solutions and build an IoT device that can withstand all the possible attacks
With IoT gaining widespread popularity, both manufacturers and users can avail maximum benefits only if the devices are reinforced with stringent security measures.
How can runtime application self-protection (RASP) help secure IoT devices and apps?
After having looked at the industry best practices to secure IoT devices, let’s have a brief overview of one of the most important security solutions that have redefined app security with its proactive methods. Runtime application self protection or RASP is an in-app security solution that shields against destructive attempts to breach security.
RASP equips the app to deal with runtime attacks and monitors the incoming traffic with enhanced visibility into hidden vulnerabilities. The benefits of RASP are as follows:
- RASP works within the application unlike traditional security solutions like firewall.
- It detects and counteracts attacks without affecting the application performance.
- RASP can accurately differentiate between legitimate requests and malicious attacks which reduces false positives.
- It has the ability to prevent zero day attacks with accurate insights into application logic, configuration, and data event flows.
- It helps developers to identify the exact lines of codes where vulnerabilities exist and aids them in their pen testing efforts.
- RASP is a scalable security solution that can adapt to the ever changing environment.
There are different methods of RASP deployment depending on which it will either monitor or block incoming illegitimate requests. While traditional firewalls can only deal with known threats, RASP can actively detect unknown threats and vulnerabilities that may have escaped the development team’s attention. And this capability is what could make RASP a potent weapon to fight IoT security threats.
Conclusion
IoT is undoubtedly a boon for modern consumers and enterprises. However, weak security will do more harm than good and create disastrous consequences. IoT devices are easy prey to attacks owing to unencrypted data transmission. Inexperienced manufacturers are unaware of security dangers and create devices that rank low on security. These devices require the manufacturers to have advanced programming knowledge compared to traditional software. Unfortunately, security is not a top priority while creating IoT devices since most manufacturers are in a race to reach consumers before competition does.
OWASP has published the top 10 IoT vulnerabilities in view of the rising cases of cyber attacks for manufacturers to build the learnings into the device. Adopting security measures equips the manufacturer and the buyer to better address the threats. Manufacturers are expected to integrate end-to-end security with continuous testing throughout all product development stages. That is, perhaps, our best shot at nullifying IoT security risks.
AppSealing is a security solutions provider that protects your applications from data manipulation and theft. Discover and troubleshoot vulnerabilities in IoT devices with robust and easy-to-use security solutions that work perfectly across different operating systems without impacting the performance.
To secure your IOT apps without ANY CODING from emerging threats, click on the link below to know more about AppSealing and sign-up for a free trial.
Secure My App
Frequently Asked Questions
1. What is the OWASP IoT Top 10?
The OWASP IoT Top 10 is a list of the top security vulnerabilities for IoT devices. It includes issues such as weak, guessable, or hardcoded passwords. The list is aimed at helping manufacturers, developers, and consumers better understand and address the security issues associated with the Internet of Things. It provides guidance to fortify the security of IoT products.
2. Why is the OWASP IoT Top 10 important?
The OWASP IoT Top 10 is important because it provides a comprehensive list of the most critical security issues for manufacturers, enterprises, and consumers in the IoT industry. It helps identify vulnerabilities such as weak passwords and lack of physical hardening, allowing for corrective actions to fortify the security of IoT products. This guidance aims to improve security decisions when building, deploying, or assessing IoT technologies.
3. How does the OWASP IoT Top 10 help secure IoT devices?
The OWASP IoT Top 10 helps secure IoT devices by providing a unified list of the top things to avoid when dealing with IoT security. It sheds light on prevalent security gaps, such as insecure network protocols and outdated components, enabling developers and enterprises to take corrective actions and fortify the security of IoT devices.
4. What are the common vulnerabilities addressed by the OWASP IoT Top 10?
The common vulnerabilities addressed by the OWASP IoT Top 10 include weak, guessable, or hardcoded passwords, insecure network services, and insecure ecosystem interfaces. These vulnerabilities can compromise the security of IoT devices and can be mitigated through measures such as employing secure network protocols and regularly updating network services.
5. How can I use the OWASP IoT Top 10 to assess the security of my IoT devices?
The OWASP IoT Top 10 provides a comprehensive methodology for assessing IoT device security. You can use it to identify vulnerabilities such as weak passwords and insecure network protocols. By following the guide, you can plan tests, define test scope, and apply the latest security practices to fortify your IoT products.