
In July 2020, the digital landscape witnessed a remarkable incident of cyber theft that reverberated globally. Famous Twitter accounts, belonging to notable personalities such as Elon Musk, Bill Gates, Barack Obama, and Joe Biden, were utilized to propagate an alluring proposition: individuals who sent Bitcoin to a designated address would receive a generous doubling of their contribution. The international community watched in astonishment and the promise of multiplying Bitcoin holdings was nothing more than a deceitful scheme, designed to pilfer digital currency from unsuspecting followers.
Contemplating the events of that fateful day in July 2020 and the subsequent surge in account takeover attacks, it becomes evident that the digital landscape, despite its numerous advantages, has become a breeding ground for conflict.
According to recent data, there has been a significant surge in Account Takeover (ATO) attacks, allegedly, with a remarkable increase of 354% by 2023. To provide a clearer perspective, these malicious cyber assaults have impacted a substantial portion of the U.S. population, affecting approximately 22% of adults, equivalent to more than 24 million households.
But why this persistent rise in account takeovers attacks?
It goes without saying that our digital identities encompass a wide range of aspects, including social media profiles, email correspondence, financial accounts, and work platforms. Each of these components, akin to pieces of a digital mosaic, presents a potential vulnerability that cybercriminals can exploit. The allure of substantial rewards, exemplified by incidents like the Twitter Bitcoin Scam, combined with the relatively low risks associated with the anonymous nature of the online world, further intensifies the need for heightened vigilance.
The threat is real, it is persistent, and it shows no signs of abating. In this blog, let’s delve into Account Takeover attacks in detail.
But first, let’s understand the basics.
Account Takeover Attack (ATO) and How To Avoid It
An Account Takeover Attack (ATO) occurs when a malicious actor gains unauthorized access to a user’s online account without their permission.
Unauthorized access to login credentials is commonly achieved by maliciously acquiring the user’s login information through deceptive methods, including phishing, keylogging, or taking advantage of data breaches.
Once inside, the attacker can:
- disrupt service delivery,
- initiate unauthorized transactions, and
- commit fraud etc.
Their motives can range from seeking profit through theft or fraudulent activities to simply causing chaos and damaging the user’s reputation. Given the vast array of online services we rely on daily, from banking and shopping to social interactions, the repercussions of an Account Takeover Attack (ATO) can be both personally and financially devastating.
How do Account Takeovers work?
The First Step – Obtaining Stolen Credentials
The initial and arguably most crucial step in the process of an Account Takeover (ATO) attack is obtaining stolen credentials. Credentials, in this context, refer to the combination of usernames and passwords that individuals use to access their online accounts. But how do attackers get their hands on these private details?
The answer often lies in data leaks and massive data breaches.
A data breach refers to unauthorized access by individuals to a company’s or organization’s database, potentially compromising a plethora of valuable information, such as user usernames and passwords. Notably, a single breach at a prominent tech company or social media platform can lead to the widespread exposure of account credentials.
Once data is breached, it does not simply disappear. Instead, these compromised credentials, numbering in the billions, frequently make their way onto the dark web and, in certain instances, even onto sections of the public Internet. Cybercriminals can acquire these credentials for a minimal cost, enabling them to carry out account takeover attacks with ease.
With these credentials in hand, attackers are well on their way to accessing accounts without the rightful owner’s knowledge or permission.
Brute-force attacks
A brute-force attack is an attacker’s relentless determination rather than relying on finesse. By utilizing automated scripts, the attacker systematically attempts numerous combinations of usernames and passwords across multiple accounts until they discover a successful match. An often-encountered variation is the dictionary attack, in which attackers employ a compilation of commonly used passwords and actual words from dictionaries in their endeavors.
A brute-force attack in the digital realm involves attempting every possible combination until the desired outcome is achieved, resembling the process of unlocking a combination lock.
Breach replay attack (Credential stuffing):
It is common for individuals, despite being aware of the risks, to utilize identical passwords for multiple accounts. In the event of a data breach, wherein one of these passwords is compromised, malicious actors can exploit this vulnerability to gain unauthorized access to other accounts employing the same username and password pairing. This form of attack is commonly referred to as a breach replay or credential stuffing attack.
A possible example is when your email and password combination from a gaming site gets leaked, and you use the same combination for your online banking, you’re at risk.
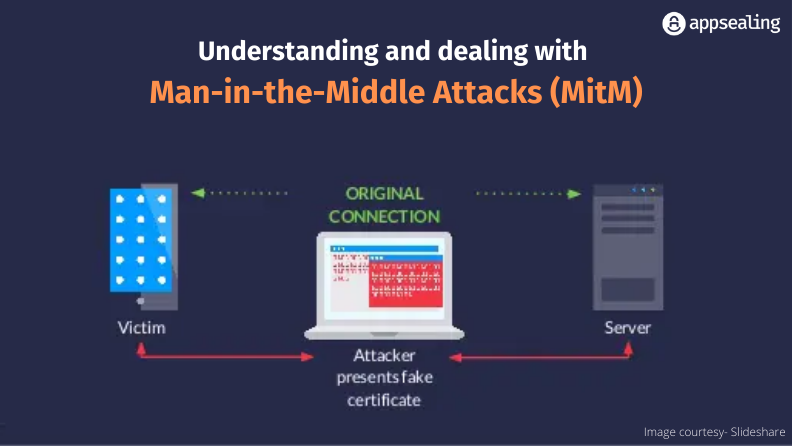
Man-in-the-middle (MitM) attacks:
Man-in-the-middle (MitM) attacks involve the interception of communication between a user and a website. This malicious act enables attackers to illicitly acquire valuable login credentials and other confidential information. Consequently, the attackers effectively position themselves as intermediaries between the user and the service, thereby gaining the ability to capture data.
An example: Imagine sending a letter, but someone intercepts it, reads its contents, and then sends it on its way. In the digital world, this interception can happen with your online data.
Phishing:
Phishing involves cunningly manipulating victims into divulging their credentials. This is typically achieved through the art of mimicking genuine websites or by sending deceitful emails that cunningly coerce users to “log in.”
An example: Upon receiving an email purportedly from your financial institution, specifically requesting verification of your account particulars, you unwittingly succumb to the trick and proceed to click on the embedded link. As a result, you are redirected to an illicit website where, unbeknownst to you, you inadvertently disclose your login credentials.
Malware attacks:
Malicious software, such as keyloggers and stealers, can surreptitiously infiltrate a user’s device. These nefarious programs are designed to clandestinely capture and transmit user credentials to attackers.
Suppose you unknowingly download an app or file, believing it to be harmless. However, unbeknownst to you, this seemingly innocuous download harbors a malicious keylogger that meticulously records each keystroke you enter. As a result, this insidious program captures sensitive information such as your login credentials.
Data exfiltration:
Data exfiltration is the act of illicitly retrieving or transferring data from a device or server. This malicious technique allows attackers to gain access to a wealth of valuable information, which may include sensitive login credentials.
Example: An employee unknowingly inserts an infected USB drive into a company computer. The malware on the drive begins copying sensitive data, including login credentials, and sends it to the attacker.
SentryMBA: The Credential Stuffing Powerhouse
Building on the various methods of account takeover we discussed earlier, tools like SentryMBA streamline and automate the process, especially when it comes to credential stuffing. SentryMBA is a popular and configurable credential-stuffing tool that cybercriminals use to exploit the vast reservoirs of stolen credentials available from data breaches.
Here’s how it fits into the ATO landscape: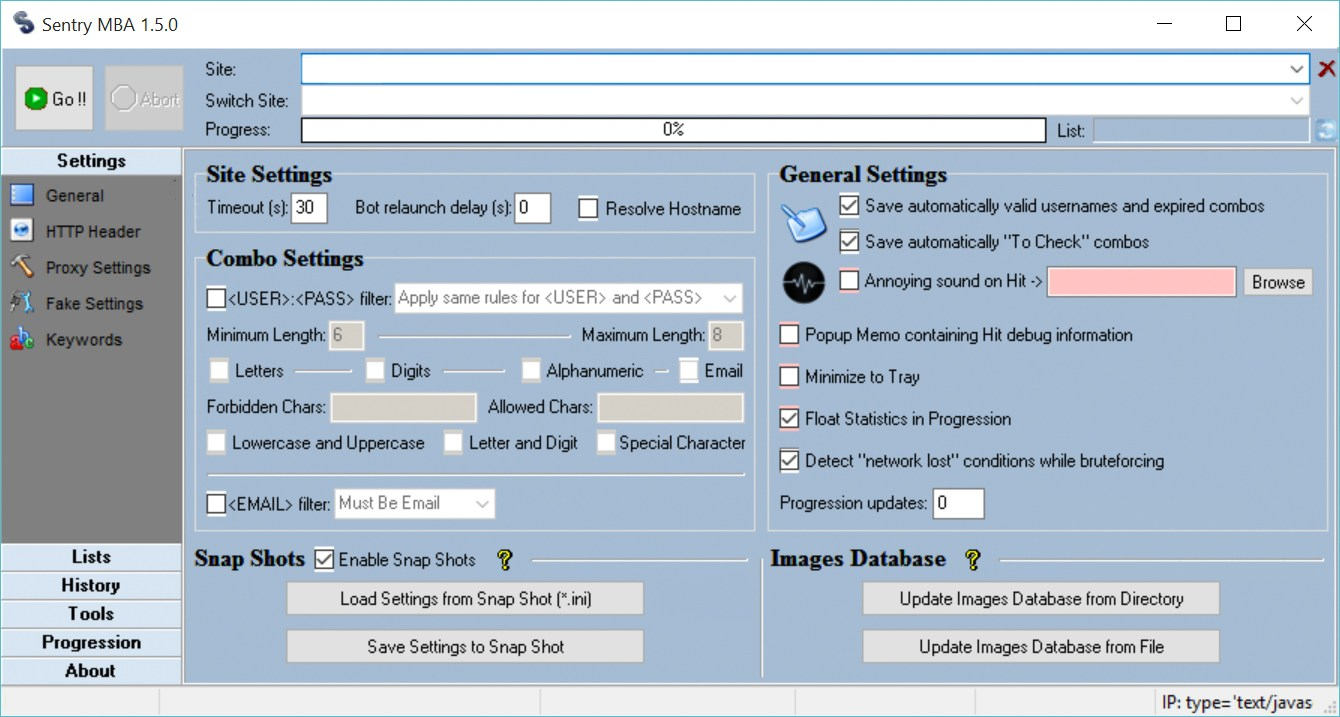
Leveraging Breached Data: Remember the breach replay attacks and credential stuffing methods? SentryMBA thrives on these. It uses vast lists of usernames and passwords, often sourced from data breaches, to launch its attacks.
Customized Attacks with Configuration Files: For each target website or application, SentryMBA requires a specific “config” that tells it how to navigate the login process, ensuring it can adapt to different platforms.
Bypassing Security Measures: Just as attackers use various methods to bypass security in other forms of ATOs, SentryMBA, with the right configurations, can often circumvent common security measures like CAPTCHAs or rate limits.
Automated and Efficient: In the world of brute-force attacks, automation is key. SentryMBA can rapidly test multiple combinations, making it a potent tool for attackers looking to exploit users who reuse passwords across platforms.
Example: Think back to the data exfiltration method of ATO. If an attacker extracts a list of usernames and passwords from a company’s server, they could feed this data into SentryMBA and target multiple websites, banking on the likelihood that some individuals reuse their passwords.
The Second Stage: Exploitation or Monetization of Valid Credentials
After successfully identifying valid credentials through tools like SentryMBA or other methods, attackers reach a pivotal juncture in the account takeover process. This stage is characterized by the decision to either directly exploit the compromised account or monetize the access by selling the credentials to others.
Direct Exploitation:
With valid credentials in hand, attackers can log into the compromised account to extract value for themselves. The nature of this exploitation varies based on the type of account:
- For financial accounts, they might initiate unauthorized transactions, transferring funds or making purchases.
- On social media platforms, they could spread misinformation, send spam, or even blackmail the account owner.
- In the case of email accounts, attackers can harvest personal information, reset passwords for other linked accounts, or launch phishing attacks on contacts.
Selling the Credentials:
There are attackers with alternative motives beyond directly exploiting compromised accounts. A faction of them gravitates towards the business aspect of cybercrime. These individuals engage in the trade of legitimate login credentials on underground forums or the dark web. Subsequently, buyers either exploit these accounts or redistribute the acquired credentials. The cost of these credentials fluctuates depending on the perceived worth of the account. Notably, credentials for a bank account with substantial funds or a prominent social media account are likely to command a higher price compared to an account with limited activity or value.
To connect, imagine a digital “black market” where various goods are traded. Among these goods are lists of usernames and passwords, neatly categorized: bank logins, streaming service accounts, premium app accounts, and more. An attacker, having successfully identified a set of valid credentials, might set up a virtual “stall” in this market, offering their latest haul to the highest bidder.
The Third Stage: The Domino Effect of Compromised Accounts
Once an unauthorized individual successfully gains entry into a specific account, it frequently serves as a pivotal point for subsequent account infiltrations and a wide range of chain reactions of breaches and malicious activities.
Expanding the Attack Surface:
A compromised account, particularly one that plays a central role in a user’s online presence, can prove to be a highly valuable asset for malicious actors. Specifically, an email account often serves as a central point of access for numerous other online accounts. It serves as a recipient for password reset links, verification codes, and other confidential communications. Consequently, gaining control over an email account can grant an attacker unrestricted access to a user’s complete digital realm.
Password Resets:
Having control over an email account grants attackers the ability to trigger password resets for associated accounts. This includes various platforms such as social media profiles, online banking services, and e-commerce websites. As a result, the attacker can potentially restrict the original user’s access and seize control of these accounts.
Defrauding Personal Contacts:
One frequently underestimated outcome of email account takeovers is the possibility for assailants to direct their attention toward the contacts of the victim. Exploiting the compromised account, attackers can exploit the trust associated with it by dispatching phishing emails or deceitful appeals for financial assistance to the victim’s friends, family, and colleagues.
Consider the scenario where you encounter an urgent email from a dear acquaintance, stating their current predicament of being stranded in a foreign country and desperately requiring financial assistance to return home. In such a situation, one might feel inclined to offer support, unaware that the sender’s email account has fallen victim to a breach, and the plea for aid is actually a deceitful scheme orchestrated by an attacker.
What type of Businesses are affected by ATO Attacks?
The digital era has witnessed a growing reliance on online platforms and technologies by industries to effectively function, cater to their clientele, and maintain competitiveness. Despite the manifold benefits presented by this digital transformation, the reach and impact of Account Takeover attacks have expanded substantially, presenting formidable obstacles for businesses and underscoring the imperative for resilient cybersecurity measures.
Let’s delve into how each of these industries is impacted by Account Takeover (ATO) attacks:
Media and Entertainment Industry:
The media and entertainment industry, particularly music and video streaming services, is currently experiencing a notable increase in ATO attacks. Cybercriminals are taking advantage of the widespread popularity of these platforms to carry out their malicious activities. Their primary objective is to illicitly obtain login credentials, with a particular focus on those belonging to premium subscribers. These stolen credentials are later sold at reduced prices, enabling unauthorized individuals to access premium content without paying the rightful price. Consequently, this illicit practice deprives the industry of its rightful revenue and poses a significant challenge to its legitimacy.
Imagine a user paying for a premium movie streaming service, only to find out that someone else is watching movies on their account without their knowledge.
Financial Industry:
Financial institutions, such as banks and insurance companies, are highly susceptible to Account Takeover (ATO) attacks. Cybercriminals employ a myriad of techniques, ranging from credential theft to intricate phishing schemes, to illicitly accessing accounts. This poses significant risks, as potential losses can amount to millions of dollars and there is a genuine threat of undermining customer confidence and trust.
A possible example is when a user might receive a seemingly genuine email from their bank asking to confirm account details, leading them to inadvertently give away their login credentials.
Hospitality Industry:
The hospitality industry, including hotels, resorts, and other establishments, faces significant vulnerability to ATO attacks. Cybercriminals frequently focus on loyalty and reward programs, aiming to pilfer points and balances and subsequently exploit them. These breaches do not solely lead to financial losses but also have the potential to damage the brand’s reputation and undermine customer loyalty.
Imagine a scenario when a loyal hotel guest might discover that their accumulated reward points, meant for a dream vacation, have been maliciously redeemed by someone else.
Sports Industry:
The sports industry possesses a considerable amount of sensitive data, encompassing athlete contracts and medical records, which makes it an alluring target for Account Takeover Attacks (ATO attacks). Cybercriminals aim to exploit any vulnerability to gain access to this valuable information, with the intention of either selling it or utilizing it for malicious purposes.
Imagine an upcoming athlete’s medical records could be stolen and leaked, affecting their career prospects or contract negotiations.
Retail Industry:
The retail industry encounters a range of intricate challenges due to ATO attacks. Unauthorized access granted to cybercriminals enables them to partake in fraudulent actions such as placing orders for merchandise, purchasing gift cards, or exploiting reward points. In more malicious circumstances, these compromised accounts may be traded on the dark web.
A shopper might find unauthorized purchases on their account, or worse, discover their account details up for sale on underground forums.
Gaming Industry:
Gaming platforms, due to their extensive user bases and in-game transactions, are highly susceptible to ATO attacks. Cybercriminals frequently exploit these platforms to pilfer in-game assets or payment details for unauthorized acquisitions. Moreover, they may manipulate compromised accounts to deceive unsuspecting players by presenting alluring propositions.
A gamer could log in to find their in-game currency depleted or receive messages from “friends” offering free in-game items, only to be led to a phishing site.
What is the difference between credential stuffing and account takeover?
While credential stuffing is a method to achieve account takeover, ATO represents the end result and can be achieved through various attack vectors. Let’s try to understand as under:
Credential Stuffing:
Credential Stuffing is a specific type of cyberattack technique. In credential stuffing, attackers use automated tools to try and log into accounts. They don’t guess passwords randomly; instead, they use previously stolen or leaked usernames and passwords. The idea is that many people reuse their passwords across multiple platforms. So, if a password was leaked from one site, it might work on another.
Think of it like someone having a master key and trying it on numerous doors in a city, hoping that some residents have used the same lock and key mechanism.
Account Takeover (ATO):
Account takeover is a comprehensive term encompassing the culmination of diverse cyberattack methods, including the possibility of credential stuffing. In the event of an ATO, it signifies that an unauthorized individual has effectively acquired illicit access to a user’s account. Such incidents can arise through various channels, such as successful credential stuffing, phishing attacks that deceive users into divulging their credentials, or password spraying, which involves attempting common passwords across numerous accounts with the expectation of gaining entry.
Using the previous analogy, ATO would be like someone successfully entering a house using either the master key, tricking the homeowner into handing over their key, or trying a few commonly used keys until one works.
How to protect Apps from Account Takeover Attacks (ATO)?
 Inspect logins, proactively
Inspect logins, proactively
To ensure the utmost security, it is essential to thoroughly cross-refer the login credentials of new users with databases containing information from previous breaches. This diligent practice enables the identification of any instances where users are registering with credentials that have previously been compromised. Additionally, it is highly recommended to conduct regular reviews of your existing user database. By doing so, you can promptly notify your valued users in the unfortunate event that their details are exposed in a new breach.
Employ Device Recognition Techniques
Device recognition, commonly known as device fingerprinting, is an effective tool in combating account takeovers. This technique monitors and examines distinct device attributes to identify abnormal login activities. Examples include repeated unsuccessful login attempts, logins from devices with identical fingerprints, or access from unfamiliar devices, all of which can raise suspicion. In the event of a sudden alteration in the device signature or an unexpected login from a different location, further security protocols can be activated. These measures may include requesting additional authentication steps from the user or temporarily suspending the account to prevent unauthorized access.
Implement Restrictions on Login attempts:
To enhance the security measures against unauthorized access to user accounts, it is advisable to implement limits on the number of login attempts. These restrictions can be determined by carefully analyzing the customary patterns exhibited by your users, taking into account variables such as username, device, and IP address. Furthermore, it is prudent to impose constraints on the utilization of tools that can obscure identity, including proxies and virtual private networks (VPNs). By adopting this approach, the efficacy of brute-force attempts and other automated attacks is significantly diminished.
Issue Alerts for Account Updates:
Maintaining transparent and continuous communication with users regarding any modifications made to their accounts is of utmost importance. By diligently sending timely notifications whenever alterations occur, users can promptly detect any unauthorized activities. This proactive strategy guarantees that, even if a cybercriminal bypasses your security measures, the user’s immediate awareness can effectively mitigate potential threats and prevent further substantial harm.
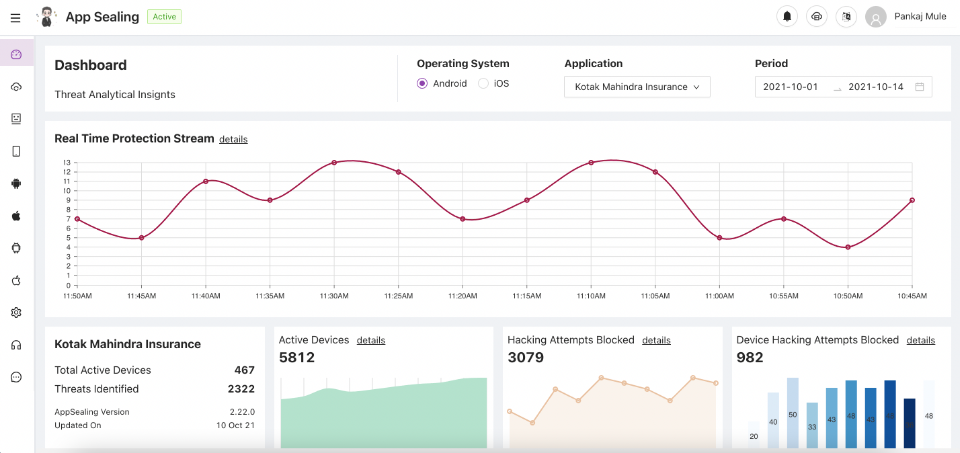
RealtimeThreat Monitoring:
Gone are the days of waiting for periodic reports; instead, you gain access to a dynamic feed that is constantly updated. This means that you can instantly observe the number of hacking attempts made on your application, the tools or devices being utilized, and even identify the geographical hotspots of these threats.
Conclusion:
Account Takeover (ATO) attacks are a growing menace in the digital world, with industries ranging from media to finance being targeted. These attacks begin with obtaining compromised credentials, often from data breaches, and can escalate using tools. The threat doesn’t end with a single breach; one compromised account can trigger a domino effect, leading to multiple unauthorized accesses. To combat this, businesses are employing various strategies. These include checking credentials against breach databases, limiting login attempts, using device fingerprinting, and implementing real-time threat analysis. The importance of these preventive measures is immense. As our online and offline worlds become increasingly intertwined, the security of our digital accounts directly impacts our personal and financial safety. In this evolving cyber landscape, proactive defense against ATOs is not just advisable; it’s essential.

 Inspect logins, proactively
Inspect logins, proactively



