In the current digital environment, the establishment of secure online connections holds paramount importance. The bedrock of this security lies in the implementation of SSL and TLS, which facilitate encrypted communication between users and servers. Nonetheless, it is imperative to acknowledge that this system is not impervious to flaws. Attackers can exploit vulnerabilities in browsers to steal data, gain unauthorized access to systems, and launch denial-of-service attacks.
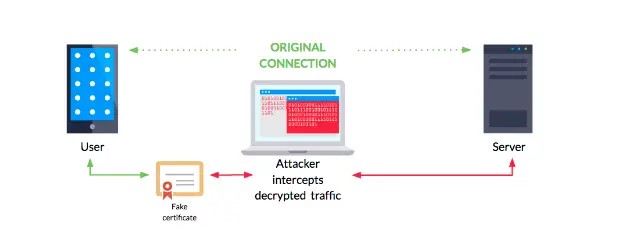
SSL Pinning is a security measure that addresses the vulnerability mentioned above. By adopting this approach, the risk of users encountering fake certificates and falling victim to man-in-the-middle attacks is significantly reduced. In today’s rapidly evolving cyber threat landscape, SSL pinning has emerged as a critical tool in preserving the security and integrity of online interactions.
What is SSL Pinning?
SSL Pinning, also known as “pinning,” is a robust security measure incorporated into applications to combat unauthorized interceptions and man-in-the-middle (MITM) attacks. By implementing SSL Pinning, applications are engineered to exclusively accept a designated SSL/TLS certificate for a particular host or group of hosts. Rather than accepting any legitimate certificate provided by the server, which could potentially originate from a malicious entity, the application is tailored to solely acknowledge and validate the predetermined, precise certificate or public key.
SSL Pinning is a crucial security measure that prevents cyber criminals from using fake SSL certificates to deceive applications. When an application implements pinning, it hard-codes or pre-defines specific certificate details that the SSL certificate must match to be accepted. This effectively eliminates the risk of attackers successfully using counterfeit certificates, even if they compromise a Certificate Authority (CA) and create seemingly legitimate certificates for a domain.
The Operational Mechanics of SSL Pinning
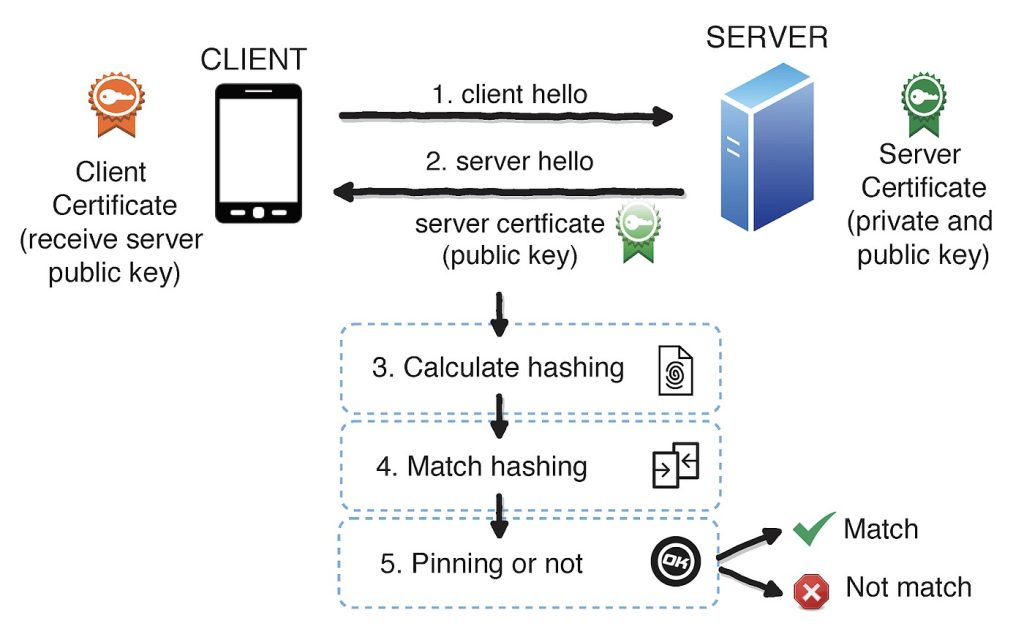
SSL Pinning operates on the fundamental principle of enhancing security by not blindly trusting every certificate that claims to be valid. Instead, an application adopts a more discerning approach by selectively trusting only certain certificates or public keys that have been pre-determined and deemed trustworthy.
Source: Apurv Pandey, Medium
Here’s how it functions, considering both mobile and non-mobile application traffic:
Initialization :
When developing the application, whether it’s mobile or web-based, the developer embeds a copy of the legitimate server’s SSL certificate or its public key within the application itself.
Connection Establishment :
When the application tries to establish a secure connection with the server, the server presents its SSL certificate to the application as usual.
Certificate Verification :
For applications without pinning, as long as the certificate is signed by a recognized Certificate Authority (CA), the connection is deemed secure. However, with SSL pinning, the application does an additional verification step.
The application compares the presented certificate or its public key with the one that has been embedded (or ‘pinned’) within it.
Decision :
If the certificate matches the pinned version, the connection proceeds.
If there’s any discrepancy, the application will terminate the connection, safeguarding the user from any potential man-in-the-middle (MITM) attack.
Mobile vs. Non-Mobile Applications :
For mobile applications, SSL pinning is usually implemented within the app’s code. Many mobile development frameworks and libraries provide tools or modules specifically for this purpose.
For non-mobile applications or web applications: Browser extensions or specific client-side scripts can be used to implement SSL pinning.
Source: Learn Worthy
However, it’s less common in standard browsers due to the flexibility needed to trust various CAs. More often, web-based pinning might be seen in web applications utilizing dedicated client software or plugins.
SSL pinning is a valuable security measure that significantly mitigates the potential risks associated with fraudulent certificates. By implementing SSL pinning, the application will only accept certificates that precisely match the pinned certificate or public key. This additional layer of security provides robust protection against malicious actors attempting to exploit fake or compromised certificates in MITM attacks.
Exploring Digital Certificates for Secure Connectivity
Digital Certificates, often referred to as public key certificates, are foundational to the secure encryption of online data and the authentication of devices and users. Rooted in the science of cryptography, these certificates function within the Public Key Infrastructure (PKI) to ensure that data transferred between two systems—be it between two servers, a user’s device and a server, or any combination thereof—is both encrypted and authenticated.
The digital certificate plays a pivotal role in ensuring the security of online connections. It serves as the cornerstone in validating the legitimacy of the server, as well as expediting the encryption process. Moreover, it safeguards the privacy and reliability of the exchanged data. These certificates are indispensable in establishing trust and upholding data security on the internet, without which the task would be considerably more arduous
Digital certificates and the process of securing connections are inextricably linked, functioning cohesively to guarantee the confidentiality and authenticity of our online communications.
Here’s how they function together:
Establishing Trust:
When initiating a connection to a secure website, the server presents its digital certificate to your web browser. This certificate serves as a reliable guarantee of the server’s identity and is exclusively issued by a reputable Certificate Authority (CA).
Your browser contains a list of trusted CAs. It will check the server’s certificate against this list to determine if it’s from a trusted source.
Encryption:
- A digital certificate stores the public key of the server, playing a crucial role in facilitating encryption.
- After verifying the authenticity of the certificate, the browser proceeds to generate a distinctive session key. This key is then encrypted using the server’s public key and transmitted back to the server.
- The decryption of the session key is performed by the server, utilizing the corresponding private key. As a result, both the server and the browser possess a mutually shared session key, enabling them to establish a secure and encrypted connection.
Data Transfer:
When the encrypted connection is established, data transmitted between the server and the browser undergoes encryption through the utilization of sophisticated algorithms. This protective measure guarantees that in the event of data interception, unauthorized individuals will be unable to decipher the information without access to the exclusive session key.
Authentication:
The digital certificate serves a broader purpose beyond mere encryption facilitation. Its verification by the browser guarantees secure communication with the authentic server, protecting against potential threats such as malicious entities attempting to impersonate the server through man-in-the-middle attacks.
Ending the Session:
Once the secure session concludes, the session key is promptly discarded, ensuring enhanced security measures. If the user revisits the website or refreshes the page, a fresh session key is promptly established, thereby bolstering the existing security protocols.
Four Key Components of Digital Certificates:
A digital certificate is not a singular entity but rather a combination of multiple integral components that work together to enhance its effectiveness and dependability. To grasp a comprehensive understanding of a digital certificate, it is crucial to explore and comprehend the significance of its four key components.
- Subject’s Public Key: The primary content of the certificate. Others will use this public key to encrypt data that only the subject (owner of the certificate) can decrypt using their private key.
- Subject’s Information: Details about the entity or device the certificate represents, such as a website’s domain name or an organization’s details.
- Issuer’s Information: Information about the Certificate Authority (CA) that issued the certificate. This tells receivers who vouched for the authenticity of the device or user.
- Digital Signature: A signature from the issuing CA. This ensures that the certificate remains tamper-proof. If anyone attempts to alter the certificate, this signature will become invalid.
A Brief Note About The Role of Certificate Authorities (CAs):Certificate Authorities (CAs) play a crucial role within the Public Key Infrastructure (PKI) ecosystem as trusted entities. Their primary duties encompass the issuance, renewal, and revocation of digital certificates. Before issuing a digital certificate, CAs diligently undertake the validation process to ascertain the identity of the requesting entity, be it a user, device, or organization. This rigorous validation process establishes the authenticity of the user or device, ensuring their claimed identity is indeed verified.
After successful identity verification, the Certificate Authority (CA) will proceed to issue a digital certificate that includes the public key of the entity along with other relevant information. It is crucial to note that the CA will securely seal this certificate by applying its private key to create a trust mark. Any party that places trust in this CA (and possesses its public key) can ensure the certificate’s authenticity by validating the CA’s digital signature imprinted upon it.
What are the types of SSL Pinning?
SSL pinning is a valuable security measure that goes beyond relying solely on default trust mechanisms. By implementing SSL pinning, an application can enhance the security of its connections by guaranteeing that it only communicates with a specific server. To fully comprehend the intricacies and functionality of SSL pinning, it is important to distinguish between its two primary types: Static SSL Pinning and Dynamic SSL Pinning.
In order to gain a comprehensive understanding of each, let us explore their distinctive characteristics and practical uses. Below, you will find a concise summary:
Static SSL Pinning :
In this approach, the certificate or public key is embedded directly into the application during its development phase. This means that the pinned data is static and remains unchanged unless the application is updated with a new version that contains a different certificate or key.
The advantage is that it’s straightforward and offers a high degree of security, especially against man-in-the-middle attacks.
The downside is that if the certificate on the server changes (e.g., due to expiration or revocation), the application must also be updated to reflect this change, or it will fail to establish secure connections.
Practical Application:
- Mobile applications that don’t undergo frequent updates and operate in controlled environments often utilize static pinning. Examples could include specialized apps used in corporate settings or apps where security is of the utmost importance and developers want to reduce potential points of compromise.
Challenges:
- Inflexibility: If the server’s SSL certificate changes (maybe due to expiration, compromise, or other reasons), the application will start rejecting the connection until it’s updated with the new certificate or key.
- Update Overhead: Every change necessitates a new version of the application, which then needs to be pushed to users, and users have to update the app on their devices.
Dynamic SSL Pinning :
Instead of hardcoding the certificate or key, dynamic pinning allows the application to update its pins based on the certificates it encounters during its operations. Typically, the application will have a process to fetch and update its set of trusted pins without requiring a full application update.
This method provides more flexibility as it allows for changes in the server’s certificate without necessitating immediate app updates.
However, it can be a bit more complex and may introduce risks if the process of updating pins needs to be secured adequately.
Practical Application:
- Apps that need flexibility in managing certificates benefit from dynamic pinning. These include apps that communicate with multiple servers or services, each potentially having different credentials, or apps where server certificates might change frequently.
- Dynamic pinning can also be found in situations where the initial pinning is done during the first connection to the server, trusting it as a “bootstrap” process.
Challenges:
- Security of Pin Updates: Since the application can update its set of pinned certificates dynamically, it’s crucial to ensure the process is secure. An attacker could exploit a weak update mechanism to insert a malicious certificate.
- Complex Implementation: Implementing dynamic pinning requires a more sophisticated setup, often involving additional server-side components to deliver updated pins securely.
- Potential for Temporary Disruptions: If not executed carefully, dynamic updates might occasionally result in disruptions, especially if a newly fetched pin doesn’t match the server’s certificate due to some misconfiguration or error.
Both methods have their advantages and challenges, and the choice between them often hinges on the specific requirements and operational considerations of the application in question.
Advantages of SSL Pinning
SSL Pinning is a potent countermeasure against such attempts, and here’s how it enhances security:
Pre-Configured Trust :
Unlike the traditional model where an app or browser trusts any certificate signed by a recognized Certificate Authority (CA), SSL pinning involves pre-configuring an application with a specific certificate or public key. This pre-configured element is referred to as the “pin.”
Rigorous Verification :
When the application communicates with the server, it doesn’t just blindly trust the server’s certificate if a known CA signs it. Instead, it checks if the presented certificate or its public key matches the pre-configured “pin” embedded within the application.
Thwarting MiTM Attempts :
Even if an attacker successfully compromises a CA and issues a fake certificate for the domain they wish to impersonate, SSL pinning ensures that the application won’t trust it, as it doesn’t match the pre-configured pin. This is particularly powerful because it provides an additional layer of defense even if traditional trust mechanisms are compromised.
Enhanced Security Assurance :
For end-users, this means that even if there’s a rogue certificate out there, as long as they’re using an app with SSL pinning correctly implemented, their data remains secure against MiTM attempts using fake certificates.
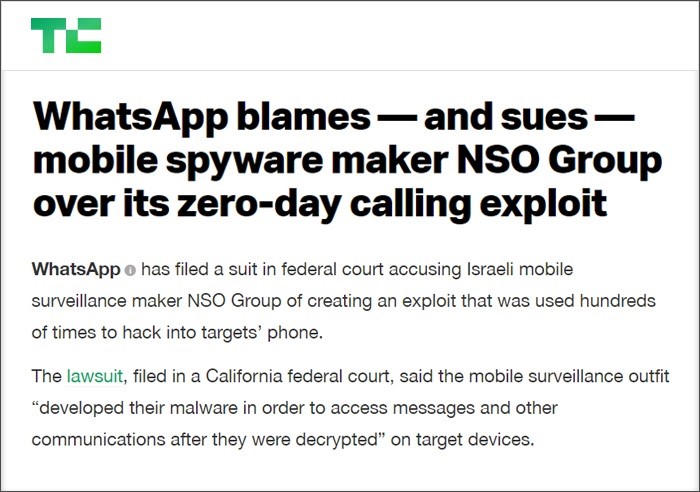
Source: TechCrunch
Mitigating Certificate-Based Attacks
Here’s how SSL pinning, particularly by hard-coding the certificate or public key, provides a strong bulwark against certificate-based attacks:
Defining Trust Explicitly :
Typically, systems trust a server if it presents a certificate signed by a trusted Certificate Authority (CA). However, this generalized trust model can be vulnerable. With SSL pinning, an application’s trust is explicitly defined. Instead of trusting any certificate from any recognized CA, the app only trusts the specific, hard-coded certificate or public key it has been embedded with.
No Room for Impersonation :
Even if an attacker manages to acquire a falsely issued certificate for a domain (either by compromising a CA or through other means), they need help with apps employing SSL pinning. The application will outright reject the attacker’s certificate because it doesn’t match the embedded, hard-coded value.
Guarding Encrypted Traffic :
One of the ultimate goals of certificate-based attacks is to decrypt encrypted traffic. However, with SSL pinning in place, even if attackers position themselves in the communication pathway, they will need help to present their fake certificates successfully. This means they can’t establish the encrypted channel required to intercept and decrypt the traffic. The app will refuse to communicate, leaving the attacker high and dry.
Consistency in Trust :
Since the hard-coded certificate or public key remains consistent across all instances of the application, users are assured of a uniform security measure. There’s no reliance on potentially fluctuating external factors, such as the integrity of various CAs.
Ensuring Trust Between Client and Server :
SSL Pinning plays a crucial role in fortifying the trust relationship between a client (typically an application) and a server. It acts as an additional layer of verification, over and above standard SSL certificate validation, by ensuring that the application communicates only with a server whose SSL certificate or public key has been “pinned” within the application itself.
Source: Developers Android
Let’s consider a mobile banking application as an example to elucidate how SSL pinning ensures trust.
Initialization: During the development phase, the banking application is coded to include (“pin”) the specific SSL certificate or public key of its banking server. This hard-coded certificate or key becomes the reference point for future connections.
Connection Attempt: A user launches the banking app and tries to log in, initiating a secure connection request to the bank’s server.
Standard SSL Validation: Typically, the server responds by presenting its SSL certificate. The client app first performs standard SSL validation by checking if the certificate is issued by a trusted Certificate Authority (CA).
SSL Pinning Verification: After standard validation, the application performs an additional step. It compares the presented certificate or public key from the server with the one that’s hard-coded into the application.
- Match: If they match, the application proceeds with establishing a secure connection, confirming that it is indeed communicating with the genuine banking server.
- Mismatch: If they don’t match, the application terminates the connection immediately, preventing any data exchange. This stops any potential Man-in-the-Middle (MiTM) attackers who might be using a fraudulent certificate from intercepting sensitive banking information.
Through this mechanism, SSL pinning ensures an elevated level of trust between the client app and server. Even if an attacker is crafty enough to produce a fake but technically valid SSL certificate, the application will reject it, maintaining the integrity and security of the client-server communication.
Limitations of SSL Pinning
While SSL pinning is an invaluable tool in bolstering application security, it isn’t without its challenges. Incorporating this advanced measure enhances the trustworthiness of client-server communications but also introduces complexities in development, deployment, and ongoing maintenance.
The rigid nature of hard-coded certificates may lead to reduced operational flexibility, necessitating frequent app updates if server certificates change. As effective as SSL pinning is in mitigating certain types of cyber threats, it’s essential to be aware of these limitations to make informed decisions on its implementation. Below, we will delve into some of the key drawbacks that come with employing SSL pinning.
Challenges in Update and Rollout
One of the inherent downsides of SSL pinning is that it adds complexity to the deployment and ongoing maintenance of applications. If you ever need to change the SSL certificate or public key on the server, you have to release an updated version of the client application to align with the new certificate.
Example: Imagine you run an e-commerce app. If your server’s SSL certificate is about to expire and you renew it with a new one, you’ll also have to release an updated version of your mobile app with the new pinned certificate. Users must update the app before they can experience connectivity issues.
Increased Development Complexity
Incorporating SSL pinning requires more work from the development team. They have to code the application to store the pinned certificate securely and ensure that it aligns with the server’s actual certificate.
In a messaging app, developers have to use secure storage mechanisms like Android’s Keystore or iOS’s Keychain to store the pinned certificates. Please do this securely to avoid exposing the app to vulnerabilities.
Reduced Adaptability
SSL pinning can make it harder to make swift changes to your security configurations. For example, if you wish to change the SSL certificate, the app needs to be updated and redistributed through app stores, which can be a time-consuming process.
Example: Suppose you’ve developed a news aggregation app, and you decide to implement more robust encryption methods requiring a new type of SSL certificate. With SSL pinning in place, you can’t just update the server-side certificate; you’ll have to push an entirely new app update through platforms like Google Play, forcing users to download the updated version to continue using your service securely.
Final Thoughts
SSL Pinning serves as a robust security mechanism designed to enhance the trust and integrity of client-server communications. Through types like Static and Dynamic SSL Pinning, it offers an additional layer of verification beyond the traditional SSL certificate validation. By hard-coding the server’s SSL certificate or public key into the client application, SSL Pinning ensures that the app communicates only with the intended server, thereby thwarting potential Man-in-the-Middle (MiTM) attacks and certificate-based exploits.
However, it’s crucial to understand that SSL Pinning isn’t a one-size-fits-all solution. It introduces challenges, such as complicating the app deployment process, adding to the development workload, and reducing operational flexibility. These limitations require careful consideration, especially when balancing the need for heightened security against the demands of agile development and deployment processes.
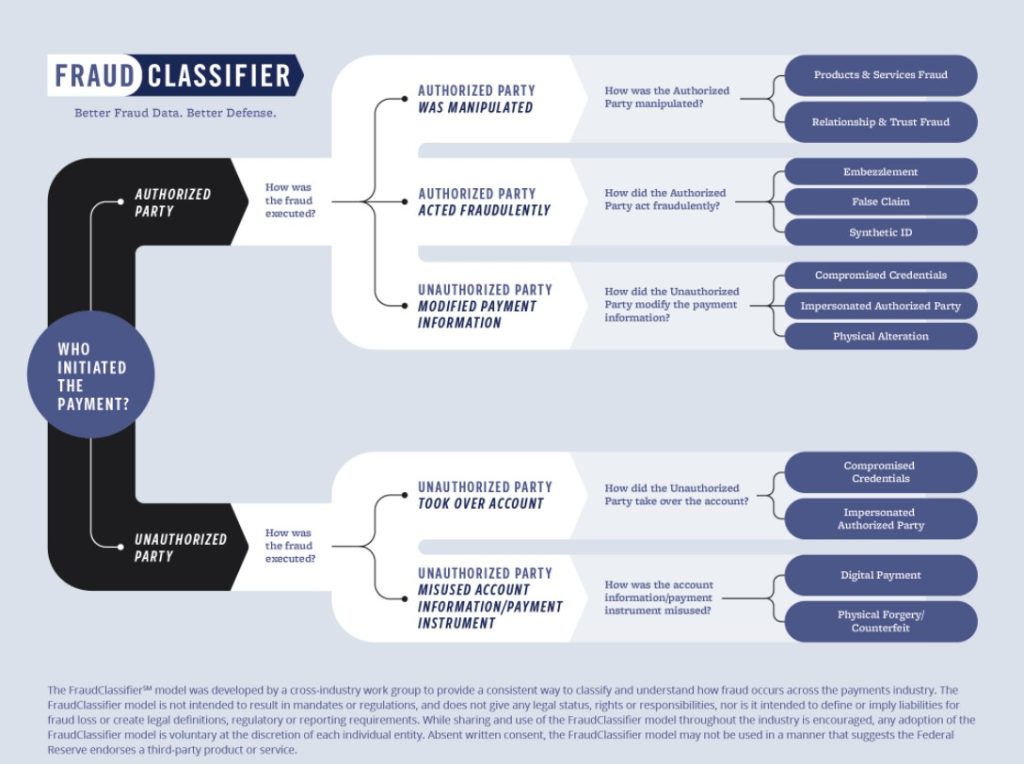
Source: The Federal Reserve
Let’s dive deeper into the nuanced role that a “Refined Rules Engine” plays in the modern landscape of fraud prevention.
The Continuing Relevance of Rules in a Machine Learning World
While machine learning has been a game-changer in identifying complex fraud patterns, it’s not the end-all-be-all solution. Rules still serve as a vital tool in a fraud analyst’s arsenal for several reasons:
Quick Response to Ongoing Attacks
Rules can be implemented in real time to halt a fraud attack as it’s happening. This is particularly useful when the attack can be traced to a specific location or characteristic.
Example: Imagine a scenario where a series of fraudulent transactions are all coming from a particular IP address in a specific city. A rule can be immediately set to block all transactions originating from that IP address, effectively stopping the attack in its tracks.
Proactively Blocking Emerging Fraud Trends
Machine learning models often rely on historical data, which may not be up-to-date with the very latest fraud schemes. Rules can be set to counteract new types of fraud that haven’t yet been incorporated into the machine learning model.
Example: If there’s a new phishing technique that fraudsters are using to gain access to accounts, but this technique hasn’t yet resulted in chargebacks and thus isn’t in the historical data, a rule can be set to flag or block transactions that show signs of this new phishing method.
Allowing Good Customers and Adapting to Business Changes
Rules aren’t just about blocking or flagging; they can also be set to allow certain types of transactions. This is particularly useful when a business changes, like acquiring a new brand or launching a new kind of transaction, that the machine learning model needs to be trained on.
Example: A retail business acquires a luxury brand. The average transaction value for this new brand is significantly higher than the existing brands. A rule can be set to allow these higher-value transactions without flagging them as potential fraud, giving the machine learning model time to adapt.
Safeguards and the Responsibility that Comes with Rule-Making
The power to set rules comes with the responsibility to ensure they don’t have unintended negative consequences. Here’s how that’s managed:
- Impact Tests: Before a rule is set live, its potential impact is assessed using historical data. If the rule would affect a significant percentage of transactions, it requires additional oversight and approval.
- Test Rules: This feature allows analysts to “dry run” a rule to see its potential impact without actually setting it live. This is a crucial step in fine-tuning rules to ensure they’re both effective and safe.
- Expert Oversight: Specialized investigation teams are on hand to assist in setting rules, particularly when a rule could have a broad impact. These teams have the experience to know which combinations of conditions are most effective and least likely to result in false positives or negatives.
Machine Learning
Instead of binary yes/no decisions that traditional rule-based systems offer, Machine Learning uses sophisticated algorithms to evaluate the risk level of each transaction, categorizing them as low, medium, or high risk. This nuanced approach allows for more targeted and effective fraud prevention measures.
Unlike rule-based engines that require manual input for each rule, machine learning models are proactive and operate in real time. They continuously learn from both historical data and new incoming information to make accurate risk assessments. This makes machine learning particularly agile and responsive to emerging fraud trends.
Further, the automation and scalability of machine learning are also noteworthy.
Imagine having a team of analysts running hundreds of thousands of queries to evaluate each transaction; machine learning accomplishes this Herculean task in mere milliseconds and with little to no human intervention. This makes it incredibly efficient at handling the high volume of transactions that occur every second in today’s digital payment landscape.
Link Analysis Using Graph Databases
Imagine a detective’s workspace, where photos of suspects, dates, and locations are pinned on a board. Connecting these pieces of evidence are strings, forming a web that helps the detective piece together the story and identify culprits. This visual representation, which helps in understanding relationships and patterns, is akin to what link analysis does in the digital realm.
A graph network operates on a similar principle. It’s a digital tool that maps out and examines the intricate connections across all customer data.
By analyzing these connections, it’s possible to discern patterns and behaviors typical of fraudsters. This “big picture” view enables businesses to identify and stop potential fraudulent activities proactively.
But the beauty of modern fraud prevention is that it doesn’t rely on just one method. Machine learning models, which autonomously analyze and score transactions based on risk, can work hand-in-hand with graph networks. For instance, a machine learning model can be trained to spot unusually large networks or networks that expand rapidly.
How to Detect & Prevent Payment Fraud
To efficiently identify and mitigate payment fraud, businesses are progressively adopting specialized technologies that extensively analyze transactional particulars and customer behaviors. Here’s a look at some of these methods:
Device Fingerprinting
Device Fingerprinting is a sophisticated method that captures and meticulously analyzes the distinctive amalgamation of software and hardware configurations found on a customer’s device. Through this meticulous process, it becomes possible to discern any suspicious or recurring patterns that may serve as indicators of potential fraudulent activity.
BIN Lookup
A Bank Identification Number (BIN) is the primary numerical sequence located on a credit card. Employing a BIN lookup aids in confirming the legitimacy and accuracy of a card by cross-referencing its particulars with a comprehensive database encompassing recognized bank numbers.
IP Lookup
Examining the IP address from which a transaction originates enables businesses to acquire valuable insights regarding the user’s geographical location and the type of connection they are utilizing. This information plays a crucial role in identifying transactions originating from high-risk locations or those that deviate from the user’s typical behavior patterns.
Reverse Email and Phone Lookup
The Reverse Email and Phone Lookup method entails the collection of supplementary data about a user’s email address or phone number. This approach enables the acquisition of valuable insights regarding the user’s credibility, particularly in cases where the email or phone number has been linked to dubious activities previously.
How to Choose a Payment Fraud Prevention Solution
Here’s how to choose a Payment Fraud Prevention Solution, focusing on key elements:
On-site Monitoring with External Data Enrichment: This is a hybrid approach where you have in-house monitoring, but you also use external tools to enhance your data.
Outsourced End-to-End Solution: Here, you rely entirely on an external provider for fraud prevention.
External Solution with Third-Party Data Enrichment: This combines an external end-to-end solution with additional data enrichment from another provider.
Also suggested is to look for solutions that offer modular features, allowing you to turn specific functionalities on or off. This helps in controlling costs and data processing.
API Integration
APIs are crucial for real-time protection and seamless updates. They allow you to integrate the fraud prevention system into your existing infrastructure easily. The benefits include real-time protection, scalability, and customization, all while the vendor manages the technical aspects.
Whitebox Systems
Opt for a transparent system—known as a whitebox system. This allows your team to understand the logic behind the risk scores and rules, offering more control and insight. It’s essential for effective communication within the company and with customers.
Dynamic Friction
Striking a balance between user experience and security is vital. Dynamic friction allows you to perform most security checks in the background, triggering additional verification only for high-risk transactions. This minimizes user friction while maintaining security.
Productivity Enhancements <h3>
Your chosen solution should not only integrate well with your existing systems but also enhance your team’s decision-making abilities. It should present information clearly and highlight what’s important.
Pricing Model
The pricing model can significantly impact your risk management strategy. Some vendors offer a chargeback guarantee, which can be reassuring but may also make the vendor overly conservative. Alternatively, a pay-per-API-call model provides more control and scalability.
Frequently Asked Questions
How long does fraud detection take?
With modern technologies, many fraud detection systems operate in real-time or near-real-time. This means potentially fraudulent transactions can be flagged within milliseconds. However, the duration for a comprehensive review or investigation can vary based on the complexity of the case.
What is faster payment fraud?
Faster payment fraud refers to fraudulent activities that exploit real-time or faster payment systems. As transactions in these systems are processed almost instantly, it provides limited time for checks, making it a target for fraudsters.
What is payment hijacking?
Payment hijacking, also known as man-in-the-middle attacks, occurs when a fraudster intercepts or alters communication between two parties during a transaction. This allows the fraudster to redirect payments to their own accounts or steal sensitive payment information.
What type of fraud is most difficult to detect?
Sophisticated frauds that use a combination of techniques, such as synthetic identity fraud (where fraudsters create new, fake identities using a mix of real and fabricated information), are among the most challenging to detect. These frauds often don’t show immediate signs of malicious activity, making them harder to identify using traditional methods.