In most cases, Bluetooth is secured because of what it uses to ensure communication between devices connected over the air. As a wireless data transfer standard, there is no question that among many potential risks associated with Bluetooth, cyber security falls into the undeniable category. You wouldn’t want your phone to access other devices while Bluetooth was enabled and vice-versa. But we often don’t know much about this wireless connection protocol. So, what is it exactly? How does Bluetooth work? What attacks are there, and how can you secure your devices against them?
NIST Guide to Bluetooth Security
Bluetooth Technology Characteristics
Bluetooth technology counters interference by applying a form of frequency-hopping spread spectrum (FH-SS) called adaptive frequency hopping (AFH).
When it comes down to devices communicating via Bluetooth technology, each device can make calculations to determine it’s Received Signal Strength Indication (RSSI) and communicate with the other network devices to adjust their relative radio power levels (i.e., incrementally increase or decrease the transmission power.)
Bluetooth has introduced three different power modes that define the energy the Bluetooth device chooses to radiate. In this way, it can adhere to the international standards for radiation used for wireless devices and keeps the power efficiency up so as not to interrupt any neighboring devices.
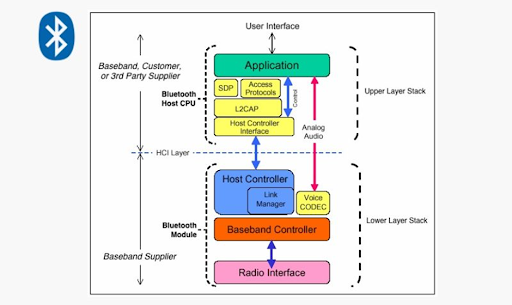
Bluetooth Architecture
Ad-hoc networks are formed between two or more devices, typically two radio devices. One host device and one client device, the master and slave, work together to create a piconet. All of the units involved in the ad-hoc network share a common channel.
There may be up to seven active slaves at a time within a piconet. Thus, each active device within a piconet is identifiable by a 3-bit active device address.
Enters Scatternet
A scatternet is a network that consists of smaller piconets that all work together. A piconet is one small part of that network, and it may also mean an area where your team members are in touch with each other. They can also be called groups. You may have more than one master for each piconet, but you must have slaves to assist all the masters throughout the time to ensure everything runs smoothly. These slaves participate in different piconets on a time-division multiplex basis so that everyone knows their place.
Security Features of Bluetooth BR/EDR/HS
The NIST’s Guide to Bluetooth Security is used to help prevent security breaches on devices that utilize Bluetooth technology, such as headphones or wireless keyboards. It not only references multiple other security standards and guidelines proposed by the NIST and the U.S. Department of Commerce about Bluetooth technology, but it is also intended to be compatible with other standards set forth by these agencies.
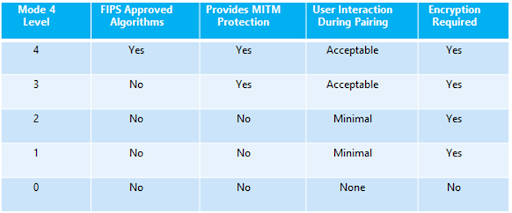
The National Institute for Standards and Technology NIST has five different levels of security for Bluetooth devices.
- Level 4: Secure Connections required to authenticate link key
- Level 3: Authenticated link key required
- Level 2: Unauthenticated link key required
- Level 1: No security is required
- Level 0: No security required. (Only allowed for Service Discovery Protocol)
The five levels of Bluetooth security provided by the NIST are to be used as guidelines for various ant-cybersecurity practices, including MitM threats and DDoS attacks, which can commonly result in user confusion and threaten security.
Source: Argus-Sec
The SP 800-121 document throws light on risk mitigation strategies that include:
Link Keys:
For a BT device, the primary key to secure authentication should be the generation of a secret symmetric key used to build what is referred to as “link keys” or “long-term keys,” depending on which version you’re referring to.
For Personal Identification Number (PIN) – also known as a legacy pairing -security is brought to the user by a randomly generated link key that’s shared between two devices. Because this link key isn’t sent or stored anywhere, it ensures your data is secure.
Authentication
Bluetooth devices are implemented using a system of challenge-response authentication, and some devices attempt to prove their identity by replying with something that the other device can verify.
The claimer-verifier scheme is the way that Bluetooth devices authenticate. Some devices are challengers, and others are verifiers.
Encryption
The NIST suggests using the AES-CMAC with a p-256 elliptic curve for high-security requirements. This satisfies SL 4, but only at 112 bits of security. It is not recommended to go above this level as one might run into issues on e-commerce websites as they already encrypt credit card information. You might also want to consider one of the non-ECC-based algorithms.
It is worthwhile to learn that the Secure Connections Only mode is incompatible with older versions.
Vulnerabilities
We’re in a new climate of security threats. The NIST is tackling enabling technology that could protect the future of both devices and homes. However, as detailed above, the NIST throws light on several vulnerabilities and makes it clear that there are plenty more to be taken care of, such as weak encryption algorithms and the poor implementation (or lack thereof) of security protocols on devices.
The NIST outlines several vulnerabilities, and the most important ones include
- Eavesdropping and attacks on link keys
- Reusing the duplicate keys and insecure storage of said keys
- Spoofing insecure devices to obtain keys from other devices they pair with
- Short PINs without using random number generators
- Sharing the key from a master device to other piconets
- Using weak encryption algorithms
Security Features of Bluetooth LE
A Bluetooth LE connection is secured with a specific security mode that supports the different levels of security. Bluetooth security mode/level requirements may change due to various factors, and it is essential to check the conditions at each stage of development.
Bluetooth 4.0 LE uses Security Mode 1 Level 3 as the most robust mode under its belt because it also has two other great qualities: authenticated pairing and encryption.
Two Bluetooth devices, which aren’t connected but are likely to want to interact together, must first become paired if they’re to do something that requires security.
Encryption and Authentication
Bluetooth LE devices utilize 128-bit AES encryption with CBC-MAC authentication.
Your connection Signature Resolving Key (CSRK) is provided by Bluetooth (LE), a digital signature that verifies the authenticity of the data.
Security Modes and Levels of a BLE
The GAP stands for Generic Access Protocol, and its primary goal is to allow Bluetooth devices to share data in an interconnected fashion easily. Generic Access Profile (GAP) defines two security modes:
- Security Mode 1
- Security Mode 2), and several levels within each method.
There are four kinds of security levels for Bluetooth:
Level 1: communication without security, i.e., no encryption,
Level 2: AES-CMAC encryption during communications (devices unpaired)
Level 3: Encryption is needed when devices are paired
Level 4: Encryption and pairing needed
LE Pairing Methods
The Bluetooth pairing process is a security-focused way of connecting to one’s Bluetooth devices. The pairing process takes place beforehand so that the device can only be used by one person and only in a certain way.
- Numeric Comparison
- Passkey Entry
- Just Works
- Out of Band (OOB)
Numeric Comparison
The “Bluetooth Numeric Comparison Pairing Model” is used when two devices show the same six-digit value on their respective screens, and matching them is essential for later pairing. Make sure both devices have a screen to display this number and that you click the Yes/ No the correct key every time you do this process so that things go smoothly when it comes down to setting up your Bluetooth device.
Passkey Entry
In the passkey entry Bluetooth LE pairing, there are six digits involved. One device will display them, and the other will match up accordingly.
Just Works
Not every device has a screen panel, and since pairing over Bluetooth LE can happen without visual feedback, the Just Works method is currently the most popular way of doing so. If we look at Just Works, the Bluetooth pairing method is the same as Numeric Comparison, but the six-digit value is set when pairing two devices for the first time and is left unchanged.
Out of Band (OOB)
The OOB pairing method is designed to pair Bluetooth devices that support NFC. To help prevent eavesdroppers or man-in-the-middle attackers from stealing sensitive data, Out of Band Bluetooth uses the Near Field Communication (NFC) instead of the 2.4 GHz band used by the BLE protocol.
Confidentiality, Authentication, and Integrity
Bluetooth device encryption is based on the Advanced Encryption Standard with a cipher block chaining message authentication code (AES-CCM) defined in RFC 3610. AES-CCM is an encryption protocol used in Bluetooth LE to provide confidentiality, per-packet authentication, and integrity.
Bluetooth (LE) authentication works by digitally signing data with a connection’s signature resolving key.
Bluetooth Vulnerabilities, Threats, and Countermeasures
Baking offers several benefits and advantages; however, these are not guaranteed without a few shortcomings resulting in a lost opportunity. Bluetooth devices transmit radio waves that may interfere with your network signal. There are some concerns (for example) about people hacking into your device to use it for nefarious purposes (like stealing essential data). On top of all this, there’s always the chance your device won’t connect properly if something you didn’t expect is blocking the signal.
| Vulnerability | Risk Posed |
| Using a series of static and repeated link keys for every pairing | Enabling the same bluetooth key for every device a unit connects to be a serious key management vulnerability. |
| Pairing Bluetooth devices based on unit keys leads to a multitude of attacks like eavesdropping and spoofing. | Once one Bluetooth device is “paired” with another, anyone who knows which key to use can then trick either or both of these units into thinking they are the other device and gain access to information zipped off from this secondary device. |
| Pins of less character (short) length. | Weak Bluetooth device PINs (as a security mechanism), which are used to generate link keys during pairing, can be easily guessed. |
Top 5 Attacks on Bluetooth Security
Bluejacking
Bluejacking is a type of attack that takes place when someone sends you data through your Bluetooth, without notifying you who it was that sent data to your device under the pretence of sending something impersonating someone else.
Bluebugging
Bluebugging is a type of Bluetooth attack in which you are able to infiltrate a device, stealing data and communications, listen in on phone calls, read emails and text messages, as well as making calls (all without the owner being aware of it).
Car Whisperer
Using a Car Whisperer software a remote hacker may be able to listen to confidential conversations or transmit malicious audio to the speaker system simply by hacking through the car’s Bluetooth connection.
Denial of Service
A DoS attack is considered one of the most common attacks on Bluetooth. It can occur when a malicious threat actor sends so many messages at such a rapid pace to a device that legitimate users are unable to access systems, devices, or other resources.
Fuzzing Attacks
Bluetooth fuzz testing attack Bluetooth fuzz testing attack is a method of sending systems incorrect information that they hopefully reject, thereby creating problems and defects.
Risk Mitigation and Countermeasures
Policies are vital for keeping your business safe and sound, but if you’re not careful about developing a sturdy set of mobile security guidelines then this can result in a lot of unneeded stress as well. Policies help ensure that data is secured and managed with proper respect to the needs of end-users while their devices are enabled with Bluetooth functionality.
1: Wireless Security Policy:
An effective way to protect oneself would be to develop a strategic organizational policy that covers Bluetooth-related technology.
2: Shared responsibility
For Bluetooth security, all users should become aware that they have a role to play in using their devices compliantly, and this will ensure the security of the network.
3: Regular assessments
To get to know about the security level of your Bluetooth and see sources which need to be protected, conduct a formal Bluetooth security assessment at regular intervals for the organization. A list of all devices that have Bluetooth capabilities can be used to perform an audit that searches for unauthorized use of wireless technologies within a given area.