IoT is the hottest buzzword today in pretty much every industry. IoT can transform (or it already has transformed) a lot of industries and processes across the spectrum – we are now safer in our homes and on the road and have become better at manufacturing and consuming tech-driven products as a direct consequence of IoT applications. But with all the good that IoT promises, there are hurdles we need to overcome to ensure we don’t bring onto ourselves the bad that could come of IoT. And by far the greatest of those challenges ahead of us is IoT security.
This article will focus on this pressing pain points for IoT security and will touch upon subjects such as:
- The nature and scope of IoT security challenges
- Industries most vulnerable to IoT security challenges
- How can we make IoT devices more secure?
- How can we nullify the IoT security threat at enterprise level?
- What does the future hold in store for IoT?
IoT Security
IoT security is the technological sphere engaged with protecting devices and networks connected to the Internet of Things from security attacks. The IoT security landscape covers technologies, processes, and regulations necessary to safeguard IoT devices and networks. It encompasses industrial machines, entertainment and home automation devices, energy grids, workplace systems, and even devices that aren’t particularly designed for network security.
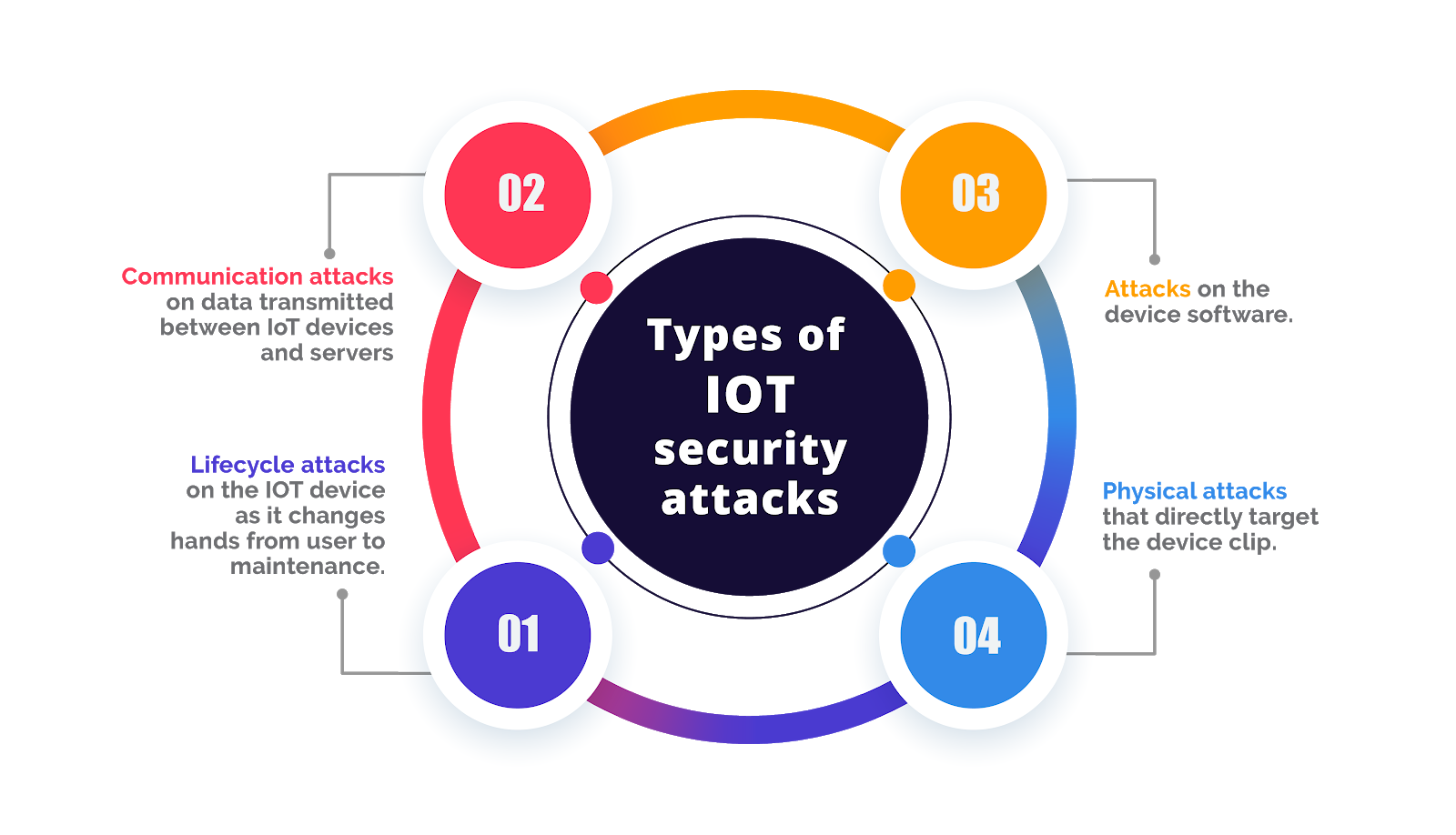
IoT security provides blanket protection to networks, systems, devices, and data from a host of IoT security attacks, including these 4 prominent vulnerabilities:
Importance of IoT Security
The modern IoT ecosystem, to put it mildly, is a little complex. Pick any industry and you’d find machines and objects that could be configured to send data over to clouds and backend applications. And as we have learnt with cyberattacks over the years, anything that is connected to the internet is prone to cybersecurity breaches. There is a stream of hackers waiting to capitalize on any opportunity to infiltrate IoT systems and devices.
Another factor at play here is building universal trust in the IoT ecosystem to get it into most households, businesses, and industries and expose a larger proportion of the populace and enterprises to its benefits. But the inherent security risks of IoT have put a spanner in the works. A 2018 survey showed that 90% of consumers do not trust IoT security. Another survey suggested that 63% of consumers find any kind of connected device ‘creepy’! IoT security can help combat this challenge. The more secure IoT devices and networks are, the more parties will trust it, and consequently join it.
What are the biggest IoT security challenges in 2021?
Numerous challenges prevent end-to-end implementation of IoT security solutions today. Let’s break them down to understand the magnanimity of what we are facing.
Authorizing Access:
Setting a proper user authentication system is one of the biggest challenges. Industrial IoT networks have several devices with different authorization needs. And it becomes difficult to set proper user authentication systems for different devices.
Network Weak Points:
When there is a complex network of devices it can extremely pinpoint the weak points. Every additional device in the system brings new vulnerabilities, which the hackers may exploit if left unprotected. For example, a device within the IoT setup may run unsafe programs, and hackers may access sensitive information from the device. By the time such a breach gets detected within the complex network, it is usually very late.
Software Updates:
Outdated software is one of the most common reasons for a security breach. Business software may not receive the latest security updates on time, leaving the software vulnerable to the latest malware. Applications can sometimes have vulnerabilities in their structure that may go undetected, leaving open gates for hackers.
Human Error:
In large enterprises, human error is a major concern for IoT security. Employees may accidentally click on insecure links, access unsafe websites, or use a public Wi-Fi connection on IoT devices, leaving open loopholes for hackers to enter the network. Especially when there are hundreds of employees connected to the IoT network, controlling employee activity is very challenging, and human errors are bound to occur.
Compromised Devices:
In a vast IoT set up some devices may be infected, and it can go unnoticed for a long time. Infected devices often run normally, but the device may still compromise information continuously. Hackers use such intrusion techniques for information gathering. The compromised device stays undetected and leaks information in small packages that go undetected. The information is collected quietly and as soon as sufficient information is obtained, the hacker may conduct a major attack. Many IoT devices are also resource-constrained and do not have the compute resources required to implement sturdy security solutions. Some devices, such as temperature and humidity sensors, are not designed to run with advanced security features.
Go-to Market Pressure:
As IoT is still a nascent industry, many manufacturers and designers don’t prioritize it during the product design and development phase. Their focus lies on getting the product out quickly, even if it compromises security. Without the security solution integration from the outset, most devices on the IoT are exposed to cybersecurity threats.
Integrating Legacy Assets:
Another major IoT security challenge is connecting legacy assets that are not inherently designed for IoT connectivity. Replacing such assets with connected technologies is expensive, so they are usually retrofitted with smart sensors. And because legacy assets have never really encountered modern security threats, the attack surface becomes even larger.
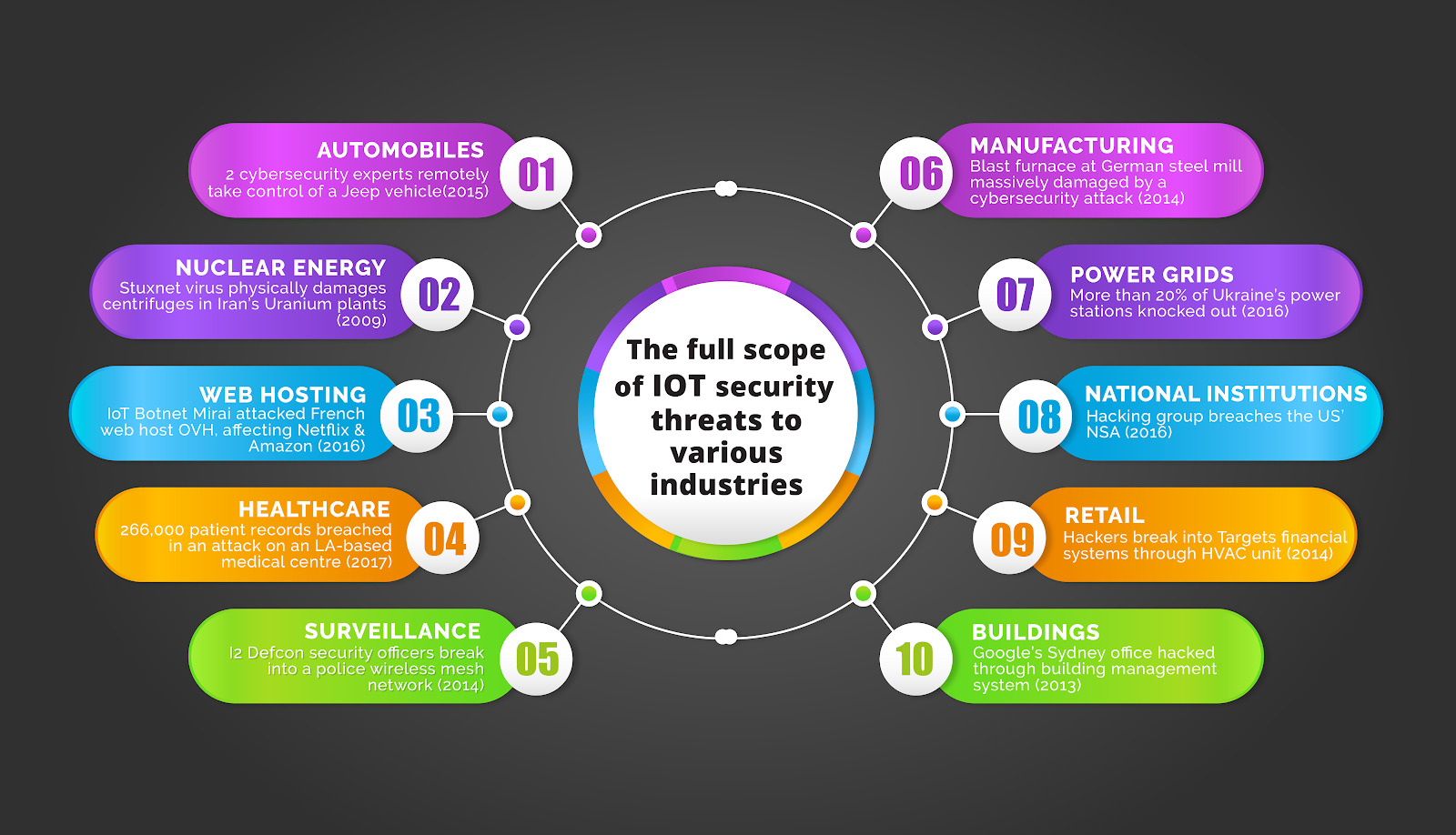
Industries are Most Vulnerable to IoT Security Attacks
Everything that is connected to the IoT ecosystem is vulnerable to security attacks. A smart home, an IoT connected car, a manufacturing unit, a smart power grid – every unit is exposed to IoT security threats. The degree of the threat, of course, varies; as does the severity of the impact.
For instance, an attack that overrides manual operation of the accelerator on a car, or one that disables its brakes, could have life-threatening implications. Similarly, a hacked insulin pump could pump in too much or too little medication to the patient and put their life at risk.
We have had hundreds of IoT security attacks over the past 2 decades and the affected industries range from giant retail chains (2013 Target attack) to financial steel mills (Germany 2014).
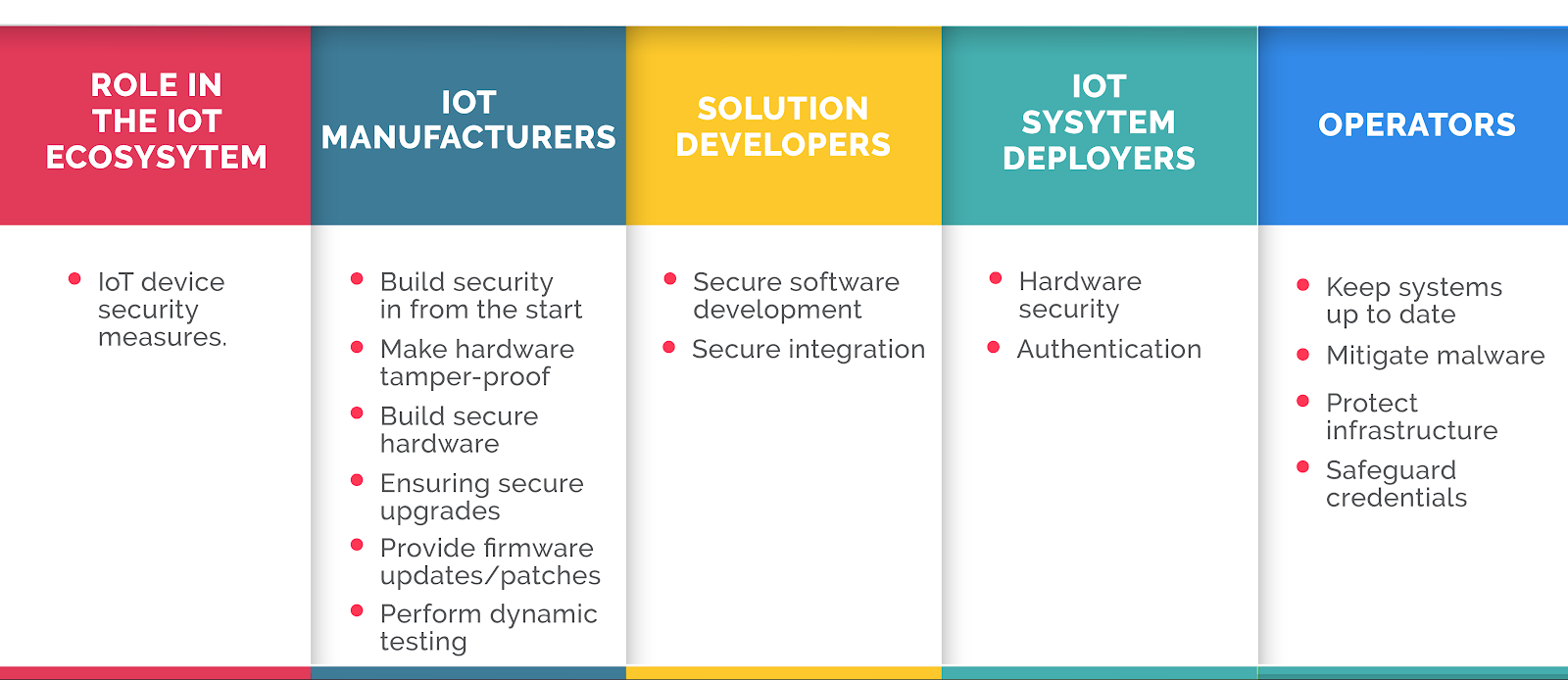
Securing IoT Network and Devices
IoT security measures vary according to the specific IoT application and the various roles in the IoT ecosystem. Here’s an overview of what security measures can be implemented at different levels to enhance IoT device security:
IoT Security Tips for Safeguarding IoT Devices from Threats
Incorporate security at the design phase
IoT security should be at the forefront of device development processes, whether it be a consumer device or industrial. Enabling security by default, designing for the latest operating systems and using secure hardware is critical. The more security measures built into the device from the outset, the more tamper-proof it will be.
Eliminate hard coded credentials from the design process
Hard coded credentials can actually foster cyber attacks. Users must be mandated to update credentials to get their device functioning. If the device has default credentials, then users should modify them with a strong password, multi-factor authentication, or biometrics.
Provide robust software protection
Active and sturdy software security measures must be implemented to secure devices connected to the IoT. manufacturers and developers must implement the following security measures:
- Password protection should be mandatory to allow access to the software. The passwords must be confidential to the user.
- Restrictions must be put in place on internet usage through connected devices. Usage could be restricted to only certain software features to prevent critical data leak.
- Sensitive programs should be blocked behind firewalls.
- Every connected device must be updated to the latest version of the software.
- Potential threats must be constantly monitored. Periodic security inspection must be performed. Security loopholes identified during such inspections must be immediately resolved.
Integrate API security
Application performance indicator (API) security safeguards the integrity of the data that is sent from IoT devices to various back-end systems. It ensures that only authorized devices, developers and apps can communicate with the APIs.
Device Identity management
Each device can be assigned a unique identifier, which will help understand and monitor the device’s behavior, its interaction with other devices and identify the proper security measures for that particular device. It will also help thwart identity spoofing attempts.
Strengthen Hardware security
Making devices more tamper-proof through hardened security helps thwart many IoT security attacks. This method assumes even more importance for devices that are usually used in harsh environments or where continuous physical monitoring of devices is not possible.
Network security
A secure network enhances IoT device security exponentially. The following IoT network security measures could be taken to facilitate that:
- Ensure port security; avoid opening ports when not required
- Use anti-malware and firewalls
- Deploy intrusion detection (or prevention) systems
- Block unauthorized IP addresses
- Patch and update all systems
Security gateways
Security gateways serve as intermediaries between the network and devices connected on it. They have greater processing power, memory and far more advanced capabilities than IoT devices, which facilitates the implementation of features like firewalls to ensure that hackers can’t access the IoT devices they protect.
Patch management
All connected devices and software should be constantly updated over the network connections or even through automation. Vulnerabilities must be disclosed promptly to ensure time efficient patch management. Antivirus updates must also be installed automatically.
Staff training
Many existing security teams struggle with IoT and operational system security as they are still new concepts for them. Training the security staff and keeping them up to date with new systems becomes critical. They should be taught new architectures and programming languages and be prepared for unknown security challenges. In particular, C-level and cybersecurity teams must be regularly trained to stay up to date with modern cybersecurity threats and protective/preventive measures.
Integrate disparate teams
Integrating disparate teams working towards a common goal can facilitate the development of stringent security measures based on knowledge exchange. For instance, when you have programming developers working with security specialists, the developers will be up to date with the security challenges on the ground and would be able to add proper controls to the devices during the development phase.
Consumer education
Consumers can play a key role in motivating device manufacturers towards creating more secure devices. For this to happen, they need to be educated about the security threats to their IoT device and the measures they could take to enhance their device’s security. When consumers become more aware and alert about security, they will refuse to use devices that aren’t equipped with security solutions, ultimately prompting manufacturers to make more secure IoT devices.
Improving IoT Security at the Enterprise Level
As more and more devices are introduced to the IoT ecosystem, enterprises are finding it increasingly difficult to keep them secure and thwart IoT attacks. IoT devices are fraught with vulnerabilities and have a massive attack surface ripe for breaches, making them a lucrative target for cybercriminals. However, enterprises can negate this threat to a large extent by implementing some actionable ideas to secure their IoT systems.
- Cryptographic algorithms and end-to-end encryption should be deployed to secure data at rest in a backend server and also in transit across the network.
- Network segmentation reduces the attack surface by keeping devices connected to their own network and restricting their access and interaction with the main network.
- Maintain a detailed inventory of all connected IoT assets to ensure that all devices are identified. Create a risk profile for each device and utilize these profiles for smart segmentation.
- Once your enterprise starts using IoT devices, make sure that every firmware update is deployed. These updates contain important security patches that prevent unauthorized access.
- Secure all mobile devices with a strong password or biometric so that in the event of a loss or theft of the device, no one can get into it and access its data.
- Invest in device access management tools to control which device can access what data, and to prevent unauthorized access.
- There is a likelihood that a security breach may occur despite putting security solutions in place. In such an event, it is important to have a security breach plan that highlights the steps that need to be taken after the breach to minimize the damage.
What Does the Future of IoT Look Like?
IoT IS THE FUTURE!
It is estimated that we’ll have more than 25 billion IoT devices by 2025. The impending 5G boom will accelerate the growth of IoT ecosystems, as faster speeds and wireless connectivity will prompt more enterprises to join the IoT bandwagon. Artificial Intelligence will assume an even more prominent role in the IoT stratosphere, as enterprises look for options to streamline data collection, analytics, and inference derivation processes. Blockchain technologies may make an appearance in the IoT ecosystem and IoT Edge Computing will gain more traction. But most importantly, security will be at the forefront of everything IoT.
IoT security is the biggest roadblock on the IoT’s path to universal application. Unfortunately, there is no ‘one size fits all’ solution to the looming IoT security threat, owing to the vast variables in the nature of devices, systems, data types, and device computing powers in the IoT ecosystem. The only way to mitigate risks successfully is to study each IoT deployment individually and curate bespoke cybersecurity solutions for it. IoT security solutions need to be built into devices and networks from the ground up and they must be put in place at every point in the IoT ecosystem throughout its lifecycle.
AppSealing is a cloud-based security solution that protects mobile apps from cybercriminals. It is an easy to use solution that can be implemented without writing a single line of code. Get in touch with them to develop and use a robust mobile app and add scalable security solutions to mobile IoT devices.