
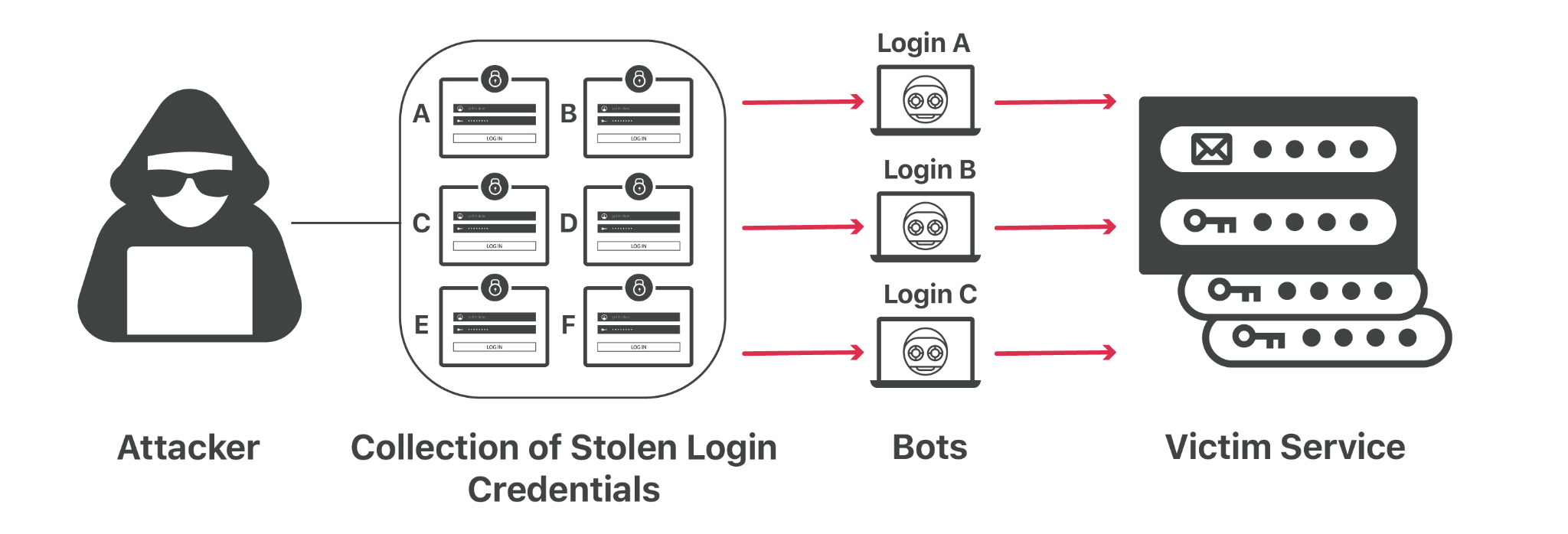
In the ever-evolving landscape of cybersecurity, credential stuffing has emerged as a formidable and increasingly prevalent threat. This malicious tactic involves the automated injection of stolen login credentials into various websites and applications, aiming to gain unauthorized access to user accounts.
Credential stuffing represents a significant threat in the digital world, primarily due to common password reuse practices. Both individuals and organizations need to be proactive in implementing security measures to mitigate the risks associated with these types of attacks.
The pervasiveness of credential stuffing attacks is staggering. According to a recent report by Okta, a leading identity and access management provider, credential stuffing accounted for a staggering 34% of all logins attempts in 2022. This translates to over 10 billion credential stuffing attempts recorded on Okta’s platform in the first 90 days of the year alone.
The success rate of credential stuffing attacks may seem low, with estimates suggesting a success rate of around 0.1%. However, given the sheer volume of stolen credentials available to attackers, even a small success rate can lead to significant damage. In 2022, Okta detected almost 300 million credential stuffing attempts per day, highlighting the magnitude of this threat.
The impact of credential stuffing attacks can be far-reaching, extending beyond compromised user accounts. Businesses face the risk of data breaches, financial losses, and reputational damage. For individuals, the consequences can include identity theft, financial fraud, and psychological distress.
So, what is Credential Stuffing and How Does It Work?
Credential stuffing is a prevalent form of cyberattack that exploits the common habit of password reuse across multiple online platforms. By using stolen credentials from one breach, attackers attempt to gain unauthorized access to user accounts on various other websites. This introduction will explore the mechanics of credential stuffing attacks and why they are a significant concern in today’s digital landscape.
How Credential Stuffing Works
In this section, we delve into the step-by-step process of how credential stuffing attacks are carried out. From the acquisition of stolen credentials to the automated process of testing these credentials across various websites, we will explore the methodology used by cybercriminals to exploit user accounts.
Collection of Credentials:
Attackers obtain lists of usernames and passwords from previous data breaches. These lists are often traded or sold on the dark web.
Automated Login Attempts:
Using automated tools, attackers use these credentials to attempt to log in to various websites and online services. This is typically done at a large scale, targeting many users across multiple sites.
Exploiting Successful Logins:
When a login attempt is successful, attackers can gain unauthorized access to accounts. They may steal personal information, financial data, or use the account for other malicious activities.
Secondary Attacks:
Sometimes, access to one account can lead to breaches of other accounts, especially if the same credentials or similar patterns are used.
What are the 7 reasons making Credential stuffing a rising threat vector?
Credential stuffing attacks are alarmingly effective for several reasons. This part of the discussion focuses on understanding the factors that contribute to the success of these attacks, including the widespread issue of password reuse and the capabilities of automated attack tools.
-
Widespread Data Breaches:
The frequency and scale of data breaches have significantly increased in recent years. Each breach often results in millions of usernames and passwords being leaked. These credentials are then available on the dark web, providing a rich resource for attackers to use in credential stuffing attacks.
-
Password Reuse:
Despite repeated warnings from security experts, many people continue to reuse their passwords across multiple sites and services. This habit makes it easier for attackers to gain access to multiple accounts using the same set of stolen credentials. The more a password is reused, the greater the potential impact of a single successful credential stuffing attack.
-
Advancements in Automation and Bot Technology:
Attackers now have access to more sophisticated automated tools and bots that can test thousands of credentials per minute on various websites. These tools not only speed up the process but can also mimic human login patterns to evade detection mechanisms like CAPTCHA or IP rate limiting.
-
Lack of Awareness and Poor Security Practices:
Many users and even some organizations are not fully aware of the risks associated with credential stuffing. This lack of awareness, combined with poor security practices like not enabling two-factor authentication or not monitoring access logs, makes it easier for attackers to succeed.
-
Ease and Low Cost of Attacks:
Compared to other forms of cyberattacks, credential stuffing can be relatively easy and inexpensive to execute. The tools required are readily available, and the technical expertise needed is not as high as that required for more sophisticated attacks. This accessibility makes credential stuffing a popular choice for a wide range of attackers, from amateur hackers to organized cybercrime groups.
-
Password Reuse:
Many users reuse their passwords across multiple sites, making it easier for attackers to gain access to several accounts with the same credentials.
-
Scale of Attacks:
Automated tools allow attackers to test millions of credential combinations, increasing the likelihood of successful breaches.
These factors collectively contribute to making credential stuffing a particularly insidious and rapidly growing threat in the cyber world. The simplicity of the attack, combined with the abundance of available credentials and general user complacency, creates a fertile ground for these types of cyberattacks to thrive and expand.
How is a Credential Attack Executed?
A credential stuffing attack is a methodical process that leverages automated tools to exploit the common practice of password reuse across multiple services. By systematically testing stolen credentials, extracting valuable data from successful logins, and retaining access for future misuse, attackers can inflict significant harm both to individuals and organizations.
-
Setting Up a Bot for Automated Logins:
The attacker begins by configuring a bot, a type of automated software, designed to log into user accounts. This bot is sophisticated enough to perform login attempts on multiple accounts simultaneously. To avoid detection, it is programmed to fake different IP addresses. This tactic helps in evading security measures like IP-based rate limiting or blacklisting, which are commonly used by websites to prevent automated attacks. By appearing as if the login attempts are coming from various locations, the bot can operate more stealthily.
-
Running Automated Credential Tests Across Multiple Sites:
The next step involves deploying an automated process that tests the stolen credentials across numerous websites. This is done in parallel, meaning the bot attempts to log into different services at the same time, rather than repeatedly trying to access a single service. This parallel approach not only speeds up the process but also reduces the risk of triggering security alerts that might arise from too many failed login attempts on one site. The attacker leverages the fact that many users reuse their passwords across different platforms, increasing the chances of finding a match.
-
Monitoring for Successful Logins and Data Extraction:
Once the bot starts operating, the attacker monitors for any successful logins. A successful login indicates that the credentials used are valid for that account. Upon gaining access, the attacker can extract valuable information from these compromised accounts. This information often includes personally identifiable information (PII), credit card details, or other sensitive data that can be used for illicit purposes. This step is crucial as it determines the actual ‘yield’ of the attack, turning the effort into a potentially profitable venture for the attacker.p
-
Retaining Compromised Account Information for Future Exploits:
The final step in the process involves retaining the information of successfully compromised accounts for future malicious activities. The attacker may use this information for a range of purposes. For instance, they might launch phishing attacks, where they impersonate a legitimate service to extract more information from the victim. Alternatively, they could use the access provided by these accounts to carry out transactions, sell the credentials on the dark web, or even launch further attacks. The compromised accounts thus become a resource for ongoing or future cybercriminal activities.
Recent 8 Instances of Credential Stuffing Attacks
-
General Motors credential stuffing attack exposes car owners info.
General Motors announced that it was the victim of a credential stuffing attack last month that exposed customer information. The attack took place in February 2023 and affected over 5 million customers. The attack allowed the hackers to redeem rewards points for gift cards.
-
Genetics firm 23andMe says user data was stolen in credential stuffing attack.
23andMe announced that it was the victim of a credential stuffing attack in October 2023. The attack took place in September 2023 and affected over 4 million customers. The attack allowed the hackers to access usernames, email addresses, and dates of birth.
-
Retail chain Hot Topic discloses wave of credential-stuffing attacks.
Hot Topic disclosed that it was the victim of a series of credential stuffing attacks in August 2023. The attacks took place over a period of several months and affected over 1 million customers. The attacks allowed the hackers to access usernames, email addresses, and passwords.
-
18-year-old charged with hacking 60,000 DraftKings betting accounts.
An 18-year-old from New Jersey has been charged with hacking into over 60,000 DraftKings betting accounts. The defendant allegedly used stolen login credentials to access the accounts and make unauthorized withdrawals.
-
Chick-fil-A confirms accounts hacked in months-long “automated” attack.
Chick-fil-A confirmed that it was the victim of a months-long credential stuffing attack. The attack took place in June 2023 and affected over 100,000 customers. The attack allowed the hackers to access usernames, email addresses, and passwords.
-
Okta: Credential stuffing accounts for 34% of all login attempts.
Okta published a report that found that credential stuffing accounts for 34% of all login attempts. The report also found that Southeast Asia and the United States are the most targeted regions for credential stuffing attacks.
-
The North Face. 200,000 North Face accounts hacked in credential stuffing attack.
The North Face announced that it was the victim of a credential stuffing attack that affected over 200,000 accounts. The attack took place in August 2023 and allowed the hackers to access user names, email addresses, and passwords.
-
FBI warns of hackers selling credentials for U.S. college networks.
The FBI issued a warning about hackers who are selling access credentials for U.S. college networks. The hackers are allegedly selling the credentials for thousands of dollars. The FBI is urging colleges and universities to be vigilant and take steps to protect their networks.
How Do Hackers Benefit From Credential Stuffing?
Credential stuffing not only breaches user privacy but also serves as a lucrative venture for hackers. This section delves into the various ways in which cybercriminals exploit the data obtained from such attacks. Beyond the initial unauthorized access, the repercussions extend into various forms of cybercrime, affecting individuals and organizations alike. Now, we will explore the multifaceted ways in which hackers turn compromised credentials into profitable opportunities. Understanding these methods is crucial in comprehending the full scope and impact of credential stuffing attacks in the digital realm.
-
Trading Stolen Data on the Dark Web:
Hackers often profit by selling bulk collections of stolen data to other criminals on the dark web. These collections can contain millions of records, including usernames, passwords, and other personal information.
For example, a hacker might infiltrate a popular online service, steal user data, and then sell this data in a dark web marketplace. The buyers, often other cybercriminals, can use this data for various illicit activities, such as launching more targeted attacks or committing fraud.
-
Facilitating Identity Theft with Personal Information:
Personal information obtained from online accounts is a goldmine for identity theft. Many online services require users to provide sensitive details like their full name, address, and credit card numbers. Hackers exploit this information to impersonate the victim, potentially using their credit card for unauthorized purchases or applying for loans under the victim’s name.
For instance, a hacker might use stolen credentials to access an e-commerce account, gather personal and financial information, and then use that information to make fraudulent purchases or transactions.
-
Executing Account Takeovers for Financial Gain:
Stolen login details are instrumental in account takeovers, particularly for accounts linked to financial information or online shopping. In such cases, the criminal gains control of the account, often changing the password and locking out the legitimate user. This can lead to direct financial losses for the victim if the account contains stored payment details.
For example, a hacker might use credential stuffing to access a user’s Amazon account, change the account’s password, and then make purchases using the stored credit card information.
-
Launching Phishing Attacks and Extortion Schemes:
With access to personal data, criminals can craft convincing phishing attacks. These attacks trick victims into voluntarily handing over sensitive information, like login credentials or credit card details, under the guise of a legitimate request. In more severe cases, if the stolen data includes highly sensitive or embarrassing information, the criminals might use it to extort money from the victim. <
For example, a hacker might use a stolen email list to send phishing emails that appear to be from a trusted source, tricking recipients into revealing their credit card information. /li>
-
Targeting Companies with Spear-Phishing and Malware:
Stolen personal information can also be used to harm businesses. Criminals might use this information to conduct spear-phishing attacks, where they target specific individuals within a company to extract confidential information or to deceive them into making unauthorized payments. Additionally, access to personal information can facilitate attempts to breach company networks, either to spy on corporate activities or to inject malware. For example, a hacker might use information from a compromised employee’s account to send a spear-phishing email to another employee, tricking them into revealing sensitive company information or credentials.
How To Detect And Prevent Credential Stuffing?
In this section, we delve into a comprehensive set of strategies and measures designed to detect and thwart credential stuffing attacks. Each suggestion is tailored to address the unique challenges posed by these attacks, ensuring that users and systems remain secure in an ever-evolving cyber landscape.
By understanding and applying these methods, we can significantly reduce the risk and impact of credential stuffing, fortifying our digital defenses against this pervasive threat.
-
Enhancing Security with Multi-Factor Authentication (MFA):
MFA is a critical defense against password-related attacks, including credential stuffing. It adds an extra layer of security by requiring additional verification beyond just a password. For instance, after entering their password, a user might also need to enter a code sent to their phone. To balance security and usability, MFA can be selectively applied in situations where a login attempt seems suspicious, like from a new device or an unusual location. For example, a financial institution might require MFA for logins from a foreign country but not from a user’s home IP address.
-
Layered Defense Strategies When MFA Isn’t Feasible:
In cases where MFA isn’t practical, employing multiple alternative defenses can provide substantial protection. This might include different security measures for various user roles, like requiring MFA for administrators but not for regular users. For example, an online retailer might enforce stricter login protocols for its staff accounts than for customer accounts.
-
Implementing Defense in Depth and Monitoring Metrics:
A defense-in-depth strategy involves using multiple security layers that work together, ensuring that if one defense fails, others are still in place. Monitoring metrics for each defense helps in detecting potential attacks or failures. For instance, a company might use both client-side defenses like JavaScript challenges and server-side defenses like rate limiting, ensuring that if attackers bypass one, the other still provides protection.
-
Secondary Authentication Factors:
Asking users for additional security information like a PIN, specific characters from a memorable word, or answers to security questions can add an extra layer of security. While not as robust as MFA, this approach can still deter attackers. For example, a bank might require users to answer a security question after entering their password but before accessing their account.
-
Utilizing CAPTCHAs to Deter Automated Attacks:
CAPTCHAs can slow down or prevent automated login attempts, a common component of credential stuffing. They might be selectively applied in suspicious circumstances, similar to MFA. For example, an online forum might only require a CAPTCHA after several failed login attempts or when logging in from a new device.
-
IP Address Mitigation and Intelligence:
Implementing a nuanced approach to blocking or challenging IP addresses based on various factors like geolocation or behavior can help in mitigating attacks. For instance, a social media platform might temporarily block IPs that have made numerous failed login attempts in a short period.
-
Device Fingerprinting for Enhanced Authentication:
By collecting data like operating system, browser type, and other device characteristics, websites can create a unique fingerprint for each user’s device. This can be used to detect when a login attempt is made from an unfamiliar device. For example, an e-commerce site might flag an account for additional verification if a login attempt is made from a device with an unfamiliar fingerprint.
-
Connection Fingerprinting for Authenticity Checks:
Techniques like JA3 fingerprinting can be used to analyze how a connection is made, providing another layer of security. This can help in identifying when a login attempt doesn’t match the typical pattern of a legitimate user. For instance, a login attempt that appears to come from a script rather than a human user can be flagged for additional scrutiny.
-
Encouraging Unpredictable Usernames:
By requiring users to create unique usernames instead of using their email addresses, the effectiveness of credential stuffing can be reduced. This makes it harder for attackers to guess valid username-password combinations. For example, a gaming website might allow users to create unique usernames that are different from their email addresses.
-
Implementing Multi-Step Login Processes
: Adding additional steps to the login process can make automated attacks more difficult. This could include entering the username and password in separate steps or requiring a CSRF token.
However, care must be taken to avoid facilitating user enumeration. For example, a corporate intranet might require employees to go through multiple steps to log in, each step validating different credentials.
-
Requiring JavaScript and Blocking Headless Browsers:
By requiring JavaScript for login and identifying headless browsers, websites can prevent many automated attacks. However, this approach must be balanced with accessibility concerns. For instance, an online store might require JavaScript to complete the login process, thereby deterring bots that cannot execute JavaScript.
-
Implementing Deterrents to Slow Down Attacks:
Introducing measures that increase the time and effort required for an attack can be effective. This might include complex JavaScript challenges or randomized error messages. For example, a cloud service provider might introduce a delay in responding to login requests after detecting suspicious activity.
-
Identifying and Alerting on Leaked Passwords:
Using services like Pwned Passwords to check if a user’s password has been part of a data breach can prevent the use of compromised credentials. For example, a website might prevent users from setting passwords that have been exposed in previous breaches.
-
Notifying Users of Unusual Security Events:
Alerting users to suspicious activities related to their accounts is a crucial step in the early detection and prevention of credential stuffing. This approach involves monitoring user accounts for any unusual behavior that could indicate a security breach, such as login attempts from unfamiliar locations or devices, multiple failed login attempts, or unusual patterns of activity.
When such activities are detected, promptly notifying the user can be an effective way to mitigate potential damage. For example, if a user’s account shows a login attempt from a country they’ve never accessed before, the system can send an alert to the user’s registered email or phone number. This notification should ideally include details of the suspicious activity and instructions on how to respond, such as changing their password or verifying recent transactions.
Conclusion
Combating credential stuffing attacks is a complex yet essential task in today’s digital landscape. Encouraging unpredictable usernames and implementing multi-step login processes can further complicate these attacks. Requiring JavaScript and introducing deterrents to slow down attackers, and identifying leaked passwords helps in preemptive defense. Crucially, notifying users of unusual security events empowers them to be part of the defense strategy. These measures, when combined, create a robust defense system that not only detects but also effectively prevents credential stuffing, ensuring the security of user data and maintaining the integrity of online platforms.


 Cloudflare Thought
Cloudflare Thought Source
Source



