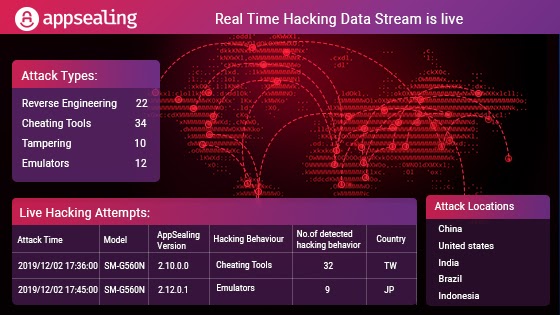
With a lot of research, testing and development over the months, we are pleased to announce our Real-time hacking Data Stream service is lived for our customers. All our customers can get immediate metrics and visibility into the real-time threat level their mobile apps are facing, allowing them to quickly mobilize resources to respond.
When a hacking attempt is detected, a response occurs instantly and detailed information such as the region, mobile device, hacking tools, and techniques and hacking trial cycles are analyzed once a day and the data displayed on the dashboard.
The speed of detection, investigation, and response are essential for effective security. Traditionally, organizations have struggled to meet these metrics due to a lack of resources and prioritization of an ever-growing number of alerts. AppSealing changes the game by solving both problems. So the Newly added Real-time hacking data stream service monitors, detects and analyzes hacking event data from the last 6 hours to the present enabling customers a simple view into their application’s threat exposure and the ability to rapidly prevent the most critical threats in their environment.
Key features and benefits of Real-time Hacking Datastream service include:
- Live data streaming for instant hacking detection and response
- Hacking data attribution map
- Able to identify hackers by the advanced search function
- Ability to monitor hacking data stream in LiveOps of customers through API (Available for Enterprise plan)
To learn more about Real-Time Hacking Data Stream please log into AppSealing Developer Console.