Mobile application security has been heavily compromised in the last decade, which was expected as billions of people now rely on mobile applications more than ever before to conduct a range of activities from booking tickets and banking to playing games and finding and sharing information. While developers may pay painstaking attention to design and development of an app, the security aspect is most of the time overlooked, leading to breaches and attacks.
The consequences of breach are huge not only for the consumers but also for enterprises that failed to implement strict security measures in the first place. While security measures may not provide foolproof protection, it minimizes the impact of damage and mitigates risks, saving companies from huge amounts of financial losses. This article discusses app hardening, a very important and potent security measure that will make your app a difficult target for hackers.
Use Cases of Application Hardening
Mobile Banking Apps
Enhancing the security of mobile banking apps is crucial as an increasing number of users depend on their devices for banking transactions. This translates into a heightened risk of fraudsters attempting to exploit any vulnerabilities. Application hardening plays a vital role in thwarting these malicious efforts by making it more challenging for attackers to develop and execute fraudulent activities within the mobile banking app.
Mobile Healthcare Apps
Mobile healthcare apps manage sensitive patient information, protected under the HIPAA regulations. Violations of patient data confidentiality through telehealth apps can result in severe penalties for healthcare providers and related entities. Employing application hardening prevents cyber attackers from gaining unauthorized access to Protected Health Information. This proactive security measure helps healthcare providers avoid HIPAA fines by ensuring the robust protection of patient data.
Mobile Retail Apps
Mobile retail apps handle sensitive card data governed by the PCI DSS. Non-compliance with PCI DSS regulations exposes online merchants to potential consequences, including fines imposed by credit card companies, erosion of customer trust, and the risk of FTC audits. Implementing robust application hardening measures is pivotal in fortifying the security of mobile retail apps, ensuring adherence to PCI DSS standards, and mitigating the associated risks that could harm both financial and reputational aspects of online businesses.
Public Service Apps
Public services personnel and government agency officials rely on mobile apps to access, transmit, and store sensitive information. The nature of this data may fall under the purview of regulations like HIPAA, specific agency policies, or overarching privacy rules. Application hardening safeguards such sensitive information and aligns the apps with the compliance requirements set forth by relevant regulations and policies
The hardening of consumer-facing apps provides protection against attacks. Embedded systems in homes, workplaces, and factories are becoming increasingly connected, and application hardening is becoming increasingly important to protect them.
Application Hardening
Application hardening is the process of securing apps against reverse engineering and tampering. Application hardening increases the effort required to manipulate the application, thereby thwarting a large number of cyber attacks. It is extremely important to implement application hardening for smooth functioning of apps in zero-trust environments.
App hardening makes the application immune to both static and dynamic analysis. Static analysis refers to an attack where the hacker tries to decompile applications on a local machine. Dynamic attacks on the other hand manipulate apps by using a debugger tool or hooking frameworks.
Benefits of App Hardening
App hardening is integral to creating a secure mobile environment. It protects the application from vulnerabilities exploitation, IP theft, tampering, misuse of data and repackaging by people with malicious intent. Following are some of the important benefits of application hardening:
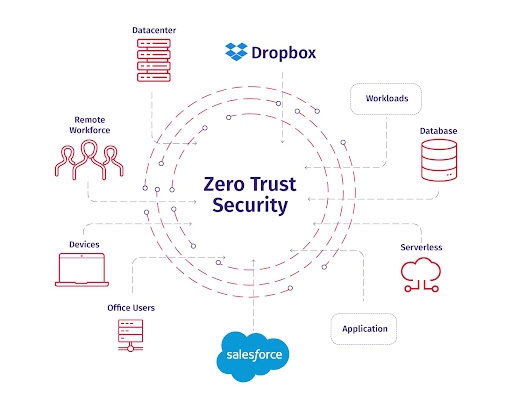
Protection in Zero Trust Environments
App hardening facilitates smooth and safe functioning of apps in zero trust environments. Many organizations today support BYOD policies and it has become difficult to ensure app security across a range of devices and environments that lie outside your control. App hardening ensures protection even if the application is run on less secure, unknown environments.
Source: Azion
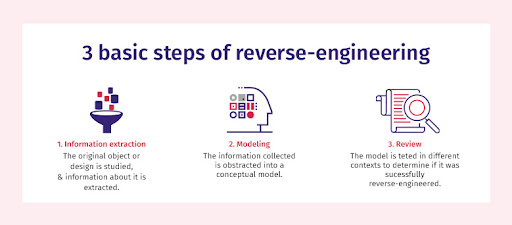
Prevents Reverse Engineering
Reverse engineering can lead to IP theft and repackaging. When a hacker tries to trace the application’s source code, app hardening ensures that the code is difficult to decipher through obfuscation techniques.
Source: Tech Target
Protection Against Tampering
Tampering is one of the top 10 mobile app security threats. Unprotected mobile apps can be easily tampered with resulting in data theft. App hardening maintains the integrity and triggers the application to identify and respond to threats. Hackers are unable to gain access to the internal values when the app is secured through app hardening.
Protects all the Sensitive Information of App Users
When there is sensitive data involved, it becomes critical to ensure stringent security. Apps that store credit card numbers or any such confidential information are prime targets for hackers. Such data, when exposed, can put your entire consumer base’ personal information at risk. App hardening is a step in the right direction to ensure data doesn’t fall into wrong hands.
Saves Enterprises from Financial Losses
A single data breach can result in consumers filing legal suits against your enterprise and imposing penalties. The costs of data breach rose from USD 3.86 million to USD 4.24 million in 2021. By implementing app hardening, you save your enterprise from enormous losses.
Protects the Brand Image and Reputation of the Company
Negligence towards security doesn’t just have financial consequences, it contributes to reputational damage too. Once consumers lose trust, it will take forever for your enterprise to win back the hard earned reputation. Following security best practices such as app hardening helps maintain your reputation in the industry and also gives a competitive edge.
Does Your App Require Hardening?
Application hardening is important for the development of a secure software application. If you are thinking whether your application needs app hardening, here are a few points to help clear your doubts. Answer the following questions and you will gain more clarity on app hardening:
- Does your application store users’ sensitive information?
- Does your application have important information about your business that may put your organization at risk if exposed?
- Does your application store decryption keys?
- Will your application run on many devices and environments outside your control?
- Does your application enable controlled access to privileged app functionality and services?
If your answer is yes to any of the above questions, app hardening should not be avoided. Applications today run on unknown devices and environments making it difficult to ensure their security. App hardening will protect your application from dangers lurking in a compromised environment. In addition to the above ones, here are three more critical points to consider:
- What are the risks and damages involved if data is leaked?
- What kind of reputational risks are involved in case of malicious app cloning?
- Does application threat modeling pinpoint any other risks to your application?
The damage can be irreversible if you are negligent towards app security. App hardening makes the application resilient against hacker attacks and helps maintain consumer trust.
Types of App Hardening
There are two types of app hardening namely passive and active. Passive app hardening is implemented to safeguard apps against static analysis. Active hardening is a series of techniques that offer protection against dynamic analysis. Here’s a more detailed explanation of the two forms.
Passive Hardening
Passive hardening involves methods that safeguard the app against decompilation. Decompilation refers to turning machine-readable code into human-readable code. Passive hardening is implemented with the objective of making it extremely difficult for hackers to understand the code. This technique primarily relies on obfuscation. The application behavior remains unchanged.
Active Hardening
Active hardening means the application is capable of protecting itself against runtime attacks. Hackers use debuggers and emulators as a means for dynamic analysis. Active hardening is used to modify the application’s behavior and response in runtime if dynamic attacks are detected.
Methods of Application Hardening
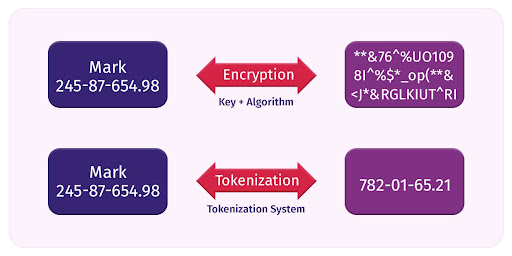
Data Obfuscation
Data obfuscation is an app hardening method that uses encryption or tokenization to obfuscate data. It is a way of scrambling data so as to make it unreadable for hackers. Tokenization turns sensitive data into an algorithmically generated number called token. It is impossible for hackers to reconstruct the original data if they can’t figure out the meaning of the tokens used to substitute the original data. This technique is especially useful for shielding banking apps.
Source: CloudMask
Code Obfuscation
Native code obfuscation makes it difficult to decipher the code. The entire code or certain parts of the code are encrypted and such a code doesn’t make any sense to an attacker who is attempting to attack the application. The code would appear meaningless to the hacker but the application function isn’t affected. An auxiliary process or self-decryption technique can be used to decipher the code.
Source: Mehran Jodavi on ResearchGate
It is recommended to obfuscate as much data as possible. In addition to that, code obfuscation also involves injecting meaningless code into the application’s binary. This can help deceive hackers. Replacing variable names with pointless labels and removing metadata are some of the important obfuscation techniques.
Anti-debugging
Debuggers are originally used to detect bugs in the system. But malicious actors use debuggers to understand the way an application works and reverse engineer it. It is common for hackers to use debuggers to exploit vulnerabilities in the app. App hardening prepares the application to detect debuggers. Anti-debugging code is inserted to facilitate blocking of debuggers by the application.
Anti-tampering
When an attacker tries to gain unauthorized access to clone or copy the application, it is called tampering. Anti-tampering is an important app hardening technique that safeguards the application. Anti-tampering mechanisms involve integrity checking. Attackers clone the application and redistribute it for fraudulent purposes. Anti-tampering can detect debugging tools and instrumentation frameworks while also binding the application to identification values like PUF variables and identifiers provided by cryptographic hashes or hardware and other cryptographic secrets.
Emulator Detection
The primary objective of a hacker is to understand the application’s functioning and modify it for illegitimate purposes. Hackers achieve this by running the application on an emulator. Emulators enable the hacker to run the application inside a controlled environment. Emulators replicate the functioning of original operating systems. Applications must be able to sense and respond appropriately when they are run on emulators.
Source: EIZO
Emulators leave behind some artifacts like files and processes which can be used by the application to detect their presence. When the application is equipped with emulator detection capabilities, it can detect emulator presence from processes, registry keys and CPU instructions, etc.
Jailbreak Detection
Jailbreak refers to an iOS device with compromised security. The security controls and limitations employed by the manufacturer or service providers are removed if the device is jailbroken. Your application data and keys are easily accessible for hackers now. Jailbreak protection is an app hardening method that alerts the application when the device security is compromised and equips it to take appropriate actions.
Android Rooting Detection
This is similar to Jailbreak detection but is applicable for Android devices. Here, the hacker gains root access to the Android device which poses a great security risk for the applications running on it. There are certain known values like specific processes, custom builds, and packages that are commonly found in case the device is jailbroken or rooted. Rooting detection techniques ensure the application data isn’t misused by actively detecting any security breach in the device’s operating system.
Final Thoughts
Application hardening is an effective measure to protect the app’s IP and prevent repackaging. It is a critical component in building a secure software development lifecycle process. An application that isn’t hardened using any of the above mentioned techniques presents a ripe opportunity for hackers to cause damage in terms of both revenue and reputation. Application hardening, when implemented in conjunction with other defense mechanisms and security controls, can enable the app to defend itself against a range of suspicious activities.
Enhance your application’s security self-reliance with a layered defense strategy that facilitates disabling of attack vectors. Application hardening as part of a layered app security approach includes runtime protection, strong authentication, and other techniques to defend against several attack scenarios. While it may not completely eliminate the threat of an attack (nothing does), it definitely makes it harder for cybercriminals to break down your security shield.
Appsealing provides next generation security solutions for Android, iOS, and hybrid applications. Add scalable security to your application with zero codings and protect your application from known and unknown threats. With affordable robust security solutions, it provides runtime security for movie apps, gaming, fintech, e-commerce among others. Having blocked more than 150+ million hacking vectors yearly, Appsealing offers real-time threat analytics for developers to make informed decisions. Get in touch with our team to ensure full compliance with industry security standards.
Application Hardening – Frequently Added Questions
1. What is server application hardening?
By preventing tampering and reverse engineering, mobile apps are made more secure. Hackers have to work harder to manipulate servers because of it. Each technique addresses a specific threat. In addition to preventing static analyses (offline), servers can also be hardened against dynamic analyses (online). A dynamic analysis allows attackers to manipulate an app remotely during runtime, such as bypassing authentication and understanding code logic.
2. What is the use of hardening?
App hardening involves various methods for optimal security. Code obfuscation prevents easy reading of source code, using sub-techniques like renaming, packing, and dummy code insertion. Its goal is to change the code without impacting app functions or performance.
3. What is an example of application hardening?
One of the examples of application hardening is Data Obfuscation. By using this technique, sensitive code sections can be obscured in mobile apps. If a hacker accesses a database, valuable information, like financial data, appears as a random string, enhancing security.
4. What is hardening in SDLC?
Hardening in Software Development Life Cycle (SDLC) refers to the phase where the software
is fortified and prepared for release. It involves rigorous testing, security checks, and
optimization to ensure the application is robust, secure, and ready for deployment.