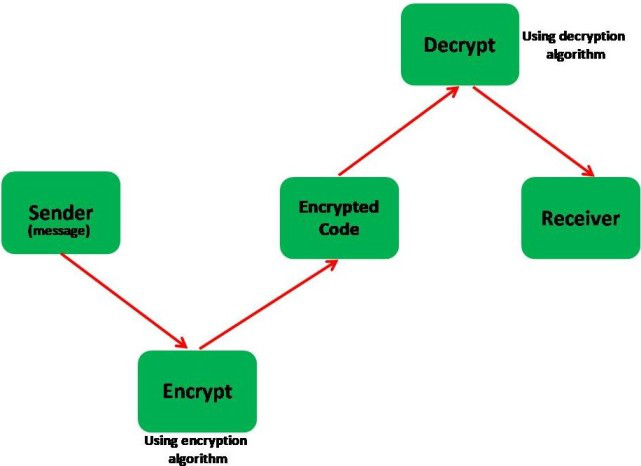
The lack of Android app encryption presents many risks for both the users and developers of an Android application. Without proper encryption, malicious attackers can gain access to sensitive information contained within an app’s code. That data may include personally identifiable information, such as usernames and passwords, allowing the attackers to access restricted accounts with high levels of privilege. Additionally, missing encryption in an app could compromise its integrity by letting attackers easily make modifications or inject malware into the codebase. These risks could lead to serious security and privacy issues that can have a lasting impact on the reputation of a company and their customers.
Android App Encryption
Android app encryption is essential to protect sensitive data that is stored and transmitted by an app. Encryption is the process of converting data into a coded format that can only be deciphered with a specific key, making it unreadable to unauthorized users who may try to access the data. The following are some examples of the importance of Android app encryption:
- Protecting user data: Android apps often store sensitive user data, such as login credentials, personal information, and financial data. Encryption can prevent this data from being accessed or stolen by unauthorized users in case of a data breach.
- Ensuring data integrity: Encryption can also be used to ensure data integrity. By encrypting data, developers can confirm that the data has not been altered or tampered with in transit, preventing malicious actors from modifying the data.
- Meeting compliance requirements: Many regulatory bodies and industries, such as healthcare and finance, require that data be encrypted to protect user privacy and meet legal requirements.
- Preventing reverse engineering: Encryption can also be used to protect app code from reverse engineering. By encrypting code, developers can make it more difficult for attackers to understand how the app works and reverse engineer it to find vulnerabilities.
- Preventing malware attacks: Android app encryption can also protect against malware attacks that target the app. If an app’s code is encrypted, malware cannot modify it, preventing malicious actions from being taken.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.

Importance of Android App Encryption
Android mobile apps present a larger attack surface than just the server. Once an Android mobile app is installed, it opens up the possibility for attacks from several endpoints. When code runs from the operating system of the endpoint (mobile device), it introduces risks to intellectual property (IP) in several ways.
One of the primary reasons for Android data vulnerability is the open-source nature of the operating system, which means that the code is available for anyone to inspect and modify. While this allows for greater flexibility and customization, it also makes the system more susceptible to vulnerabilities and exploits.
Secondly, the operating system can provide attackers with access to critical system resources and data, which can be used to launch attacks against other devices or systems. This is because the operating system provides access to various hardware components, such as the camera, microphone, and sensors, which can be used by attackers to collect sensitive data or spy on user activities.
Thirdly, the operating system provides a platform for the execution of third-party applications, which can introduce additional risks to IP. When applications run on the operating system, they can access and modify sensitive data, such as user credentials, without the user’s knowledge. Malicious applications can also be used to launch attacks against other devices or systems.
Fourthly, when code runs from the operating system, it can be reverse-engineered, tampered with, or stolen. Attackers can decompile the code, extract intellectual property, and modify it for their purposes. This can lead to the theft of trade secrets, proprietary algorithms, or other sensitive IP.
Furthermore, Android’s fragmentation, i.e., the wide range of devices and software versions in use, can make it challenging to address security vulnerabilities and roll out security updates promptly. This can result in security vulnerabilities remaining unpatched and leaving devices and user data exposed to cyber threats.
Different Encryption Standards and Algorithms
There are several encryption standards and algorithms used in Android for securing data at rest and in transit. Here are some of the most commonly used encryption standards and algorithms in Android:
The Cipher algorithm
The Cipher algorithm in Android supports AES encryption with 256-bit keys in both CBC and GCM modes. The Cipher class provides cryptographic functionality for key generation, encryption, and decryption, and supports a variety of encryption modes and padding modes to meet the specific security requirements of the application. The choice of encryption mode and padding mode depends on the specific use case and security requirements of the application. It is important to note that the use of strong encryption algorithms and appropriate key lengths is crucial for ensuring the security and confidentiality of sensitive data in mobile applications.
The Cipher algorithm in Android supports a variety of encryption modes, including CBC (Cipher Block Chaining) and GCM (Galois/Counter Mode), with AES (Advanced Encryption Standard) encryption using 256-bit keys. The AES algorithm is a symmetric encryption algorithm that provides strong encryption and is widely used in modern applications. The following is a detailed explanation of the Cipher algorithm in Android using AES in either CBC or GCM mode with 256-bit keys:
- Key generation: Before the encryption process begins, a 256-bit key must be generated. The key is a random sequence of bytes that is used by the Cipher algorithm to encrypt and decrypt data. In Android, keys can be generated using the KeyGenerator class.
- Cipher initialization: Once the key has been generated, the Cipher algorithm must be initialized with the appropriate encryption mode, padding, and key. For AES encryption in CBC mode with 256-bit keys, the Cipher instance can be initialized using the following code:
Cipher cipher = Cipher.getInstance(“AES/CBC/PKCS5Padding”);
SecretKeySpec keySpec = new SecretKeySpec(key, “AES”);
IvParameterSpec ivSpec = new IvParameterSpec(iv);
cipher.init(Cipher.ENCRYPT_MODE, keySpec, ivSpec);
For AES encryption in GCM mode with 256-bit keys, the Cipher instance can be initialized using the following code:
Cipher cipher = Cipher.getInstance(“AES/GCM/NoPadding”);
SecretKeySpec keySpec = new SecretKeySpec(key, “AES”);
GCMParameterSpec gcmSpec = new GCMParameterSpec(tagLen, iv);
cipher.init(Cipher.ENCRYPT_MODE, keySpec, gcmSpec);
In both cases, the initialization vector (IV) is a random sequence of bytes that is used to ensure that each encryption operation produces a unique ciphertext. The IV is passed to the Cipher.init() method along with the key.
- Data encryption: After the Cipher algorithm has been initialized, plaintext data can be encrypted by passing it to the Cipher object using the Cipher.update() method. The update() method returns a byte array containing the encrypted data.
- Finalization: Once all of the plaintext data has been encrypted, the Cipher object must be finalized by calling the Cipher.doFinal() method. This method returns a byte array containing the final block of encrypted data.
- Decryption: To decrypt the ciphertext data, the Cipher object must be initialized with the same encryption mode, padding, and key that were used for encryption. The encrypted data can then be passed to the Cipher object using the Cipher.update() method, and the final decrypted data can be obtained using the Cipher.doFinal() method.
MessageDigest Algorithm:
The MessageDigest class provides cryptographic functionality for hashing data using the SHA-2 family of hash algorithms, including SHA-256, SHA-384, and SHA-512. The following is a detailed explanation of the MessageDigest algorithm using SHA-256:
- Data input: The MessageDigest algorithm takes input data as a byte array, which can be obtained from a file, string, or any other source. In Android, data can be read into a byte array using the FileInputStream or InputStream classes.
- MessageDigest initialization: Once the input data has been obtained, the MessageDigest algorithm must be initialized with the appropriate hashing algorithm. In Android, the MessageDigest class can be initialized using the MessageDigest.getInstance(“SHA-256”) method to select the SHA-256 hashing algorithm.
- Data hashing: After the MessageDigest algorithm has been initialized, the input data can be hashed by passing it to the MessageDigest object using the update() method. The update() method can be called repeatedly to hash additional data.\
- Finalization: Once all of the input data has been hashed, the MessageDigest object must be finalized by calling the digest() method. This method returns a byte array containing the hashed data.
The SHA-256 algorithm generates a 256-bit hash value that can be used to verify the integrity of data. The hash value is unique to the input data, and any modification to the input data will result in a different hash value. This makes the SHA-256 algorithm useful for verifying the authenticity of files and data transmitted over insecure channels.
MAC
The MAC (Message Authentication Code) class provides cryptographic functionality for generating a keyed hash message authentication code using the HMAC (Hash-based Message Authentication Code) algorithm with the SHA-2 family of hash functions, including HMACSHA256. The following is a detailed explanation of the Android MAC class algorithm using HMACSHA256:
- Key input: The MAC class algorithm takes input data as a byte array and a secret key as a Key object, which can be generated using the KeyGenerator class in Android. The secret key is used to authenticate the integrity and authenticity of the input data.
- MAC initialization: Once the input data and secret key have been obtained, the MAC algorithm must be initialized with the appropriate hashing algorithm. In Android, the MAC class can be initialized using the Mac.getInstance(“HmacSHA256”) method to select the HMACSHA256 algorithm.
- Data hashing: After the MAC algorithm has been initialized, the input data can be hashed by passing it to the MAC object using the update() method. The update() method can be called repeatedly to hash additional data.
- Finalization: Once all of the input data has been hashed, the MAC object must be finalized by calling the doFinal() method. This method returns a byte array containing the generated MAC value.
The HMACSHA256 algorithm generates a message authentication code that can be used to verify the authenticity and integrity of data. The MAC value is unique to the input data and secret key, and any modification to the input data or secret key will result in a different MAC value. This makes the HMACSHA256 algorithm useful for verifying the authenticity of messages transmitted over insecure channels.
In addition to HMACSHA256, the MAC class in Android supports other SHA-2 family HMAC algorithms, including HMACSHA384 and HMACSHA512. These algorithms generate MAC values with longer bit lengths, providing increased security against attacks such as collisions and preimage attacks.
The Signature class
The algorithm provides cryptographic functionality for generating and verifying digital signatures using the SHA-2 family of hash functions with the Elliptic Curve Digital Signature Algorithm (ECDSA), including SHA256withECDSA. The following is a detailed explanation of the Android Signature class algorithm:
- Key pair generation: Before a digital signature can be created or verified, a key pair must be generated using the KeyPairGenerator class in Android. The key pair consists of a private key and a corresponding public key. The private key is used to sign data, while the public key is used to verify signatures.
- Signature initialization: Once the key pair has been generated, the Signature class must be initialized with the appropriate hashing algorithm and the private key. In Android, the Signature class can be initialized using the Signature.getInstance(“SHA256withECDSA”) method to select the SHA256withECDSA algorithm.
- Data hashing: After the Signature object has been initialized, the input data must be hashed using a hash function from the SHA-2 family, such as SHA-256. The hash function can be accessed using the MessageDigest class in Android.
- Signature generation: Once the input data has been hashed, it can be signed by passing it to the Signature object using the update() method. The update() method can be called repeatedly to sign additional data.
- Finalization: Once all of the input data has been signed, the Signature object must be finalized by calling the sign() method. This method returns a byte array containing the generated digital signature.
To verify a digital signature, the Signature object must be initialized with the public key instead of the private key. The input data must also be hashed using the same hash function as used during signature generation. Once the Signature object has been initialized, the digital signature can be passed to it using the update() method. Finally, the verify() method can be called to verify the signature, which returns a boolean value indicating whether the signature is valid or not.
Methods of Data Encryption in Android Applications
Symmetric encryption
Symmetric encryption is a type of encryption where the same secret key is used for both encryption and decryption. Android uses the Advanced Encryption Standard (AES) for symmetric encryption, which is a widely-used and highly-secure encryption algorithm.
The AES algorithm is a block cipher, which means that it encrypts data in fixed-size blocks. The size of the blocks used in AES is 128 bits. AES uses a secret key of either 128 bits, 192 bits, or 256 bits in length.
In Android, the AES algorithm is implemented using the Java Cryptography Extension (JCE) framework. The JCE provides a set of classes and interfaces that allow developers to use cryptographic services, such as encryption and decryption.
Here is some example Java code that demonstrates how to use AES encryption in Android:
// Generate a secret key
KeyGenerator keyGen = KeyGenerator.getInstance(“AES”);
SecureRandom secureRandom = new SecureRandom();
keyGen.init(256, secureRandom);
SecretKey secretKey = keyGen.generateKey();// Initialize the cipher
Cipher cipher = Cipher.getInstance(“AES/CBC/PKCS5Padding”);
cipher.init(Cipher.ENCRYPT_MODE, secretKey);// Encrypt the data
byte[] plaintext = “Hello, world!”.getBytes(“UTF-8”);
byte[] ciphertext = cipher.doFinal(plaintext);// Initialize the cipher for decryption
cipher.init(Cipher.DECRYPT_MODE, secretKey);// Decrypt the data
byte[] decryptedText = cipher.doFinal(ciphertext);
String decryptedString = new String(decryptedText, “UTF-8”);
System.out.println(decryptedString); // Output: “Hello, world!”
In the above example, a 256-bit secret key is generated using the AES algorithm. The cipher is then initialized for encryption mode and the plaintext “Hello, world!” is encrypted. The cipher is then initialized for decryption mode and the ciphertext is decrypted. Finally, the decrypted plaintext is printed to the console.
Asymmetric encryption
Android asymmetric encryption refers to a type of encryption technique that uses a pair of keys, one for encryption and one for decryption. These keys are mathematically related, but it is computationally infeasible to determine one key based on the other.
In Android, asymmetric encryption is often used in secure communication between two parties. One party, the sender, uses the recipient’s public key to encrypt a message, and the recipient uses their private key to decrypt it. Because only the recipient can access their private key, they can only decrypt the message.
Asymmetric encryption is often used with other cryptographic techniques, such as digital signatures and certificates, to provide secure communication and authentication in Android applications.
Final Thoughts
AppSealing’s data encryption solution for Android applications protects sensitive data like authentication tokens, unique identifiers, and passwords from unauthorized access and modification. By encrypting this data, AppSealing ensures that only authorized users can access it, providing an extra layer of security for your Android apps.
The key features of the product include:
-Whitebox AES 128 & FIPS 140-2 encryption for Android mobile devices, software, and operating systems
-Runtime protection covering encryption keys, API keys, authentication tokens, etc.
-End-to-end support system encompassing legacy native file input/output interface
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.