In today’s cybersecurity landscape, where cyber-attacks are becoming more sophisticated and frequent, advanced encryption algorithms such as AES have become more important. Hackers constantly look for vulnerabilities in encryption algorithms to exploit and gain unauthorized access to sensitive data. Therefore, it is critical for mobile app developers and organizations to implement data encryption as part of their overall data security strategy.
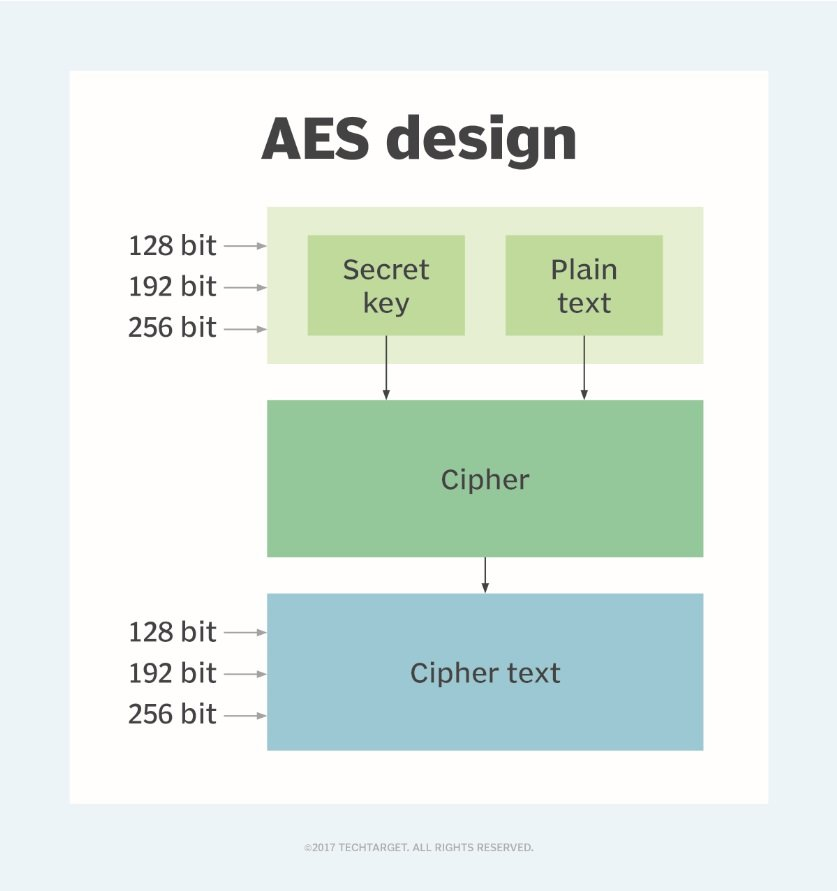
The Advanced Encryption Standard (AES) algorithm is a widely used symmetric key encryption algorithm that uses a block cipher to encrypt and decrypt data. It was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen. It was chosen by the National Institute of Standards and Technology (NIST) in 2001 as the standard encryption algorithm for protecting sensitive and confidential information in the United States.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.

AES Encryption
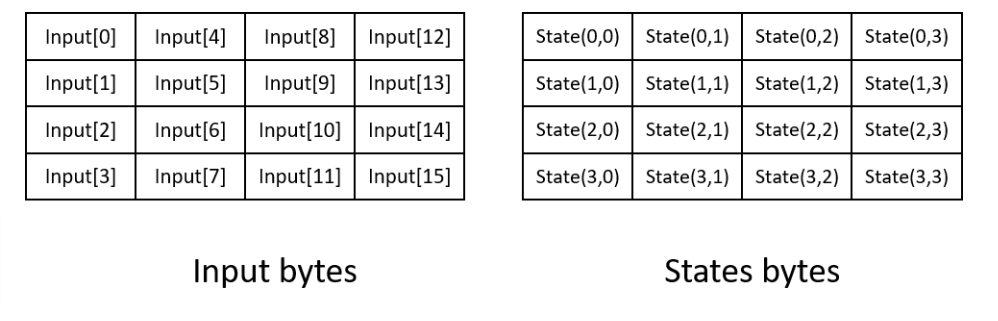
Implemented in software and hardware, the AES encryption algorithm uses a fixed block size of 128 bits and supports key sizes of 128, 192, and 256 bits to encrypt data at rest and data in transit. It works by dividing the data to be encrypted into blocks of 128 bits and then using a series of mathematical operations, including substitution, permutation, and XOR, to transform each block into a cipher block.
The AES encryption algorithm is a symmetric key encryption algorithm, meaning that the same key is used to encrypt and decrypt the data. The key is shared between the sender and the recipient of the encrypted data and is kept secret to prevent unauthorized access.
The strength of the AES encryption algorithm lies in its ability to resist attacks by brute force. Brute force attacks involve trying all possible combinations of keys until the correct key is found. With a key size of 128 bits, there are approximately 3.4 x 10^38 possible keys, making it practically impossible to break the encryption by brute force.
Another advantage of the AES encryption algorithm is its efficiency. It can encrypt and decrypt data quickly without too much processing power. This makes it suitable for applications requiring real-time encryption and decryption, such as online transactions and secure communication.
The AES encryption algorithm is widely used in various applications, including online banking, e-commerce, and secure communication. It is supported by most modern operating systems and platforms, making it a popular choice for securing sensitive and confidential information.
In conclusion, the Advanced Encryption Standard (AES) algorithm is a widely used symmetric key encryption algorithm that uses a block cipher to encrypt and decrypt data. It is considered secure, efficient, and reliable, making it an ideal choice for securing sensitive and confidential information. Its strength lies in its ability to resist attacks by brute force, and its efficiency makes it suitable for use in applications that require real-time encryption and decryption.
How does AES encryption work?
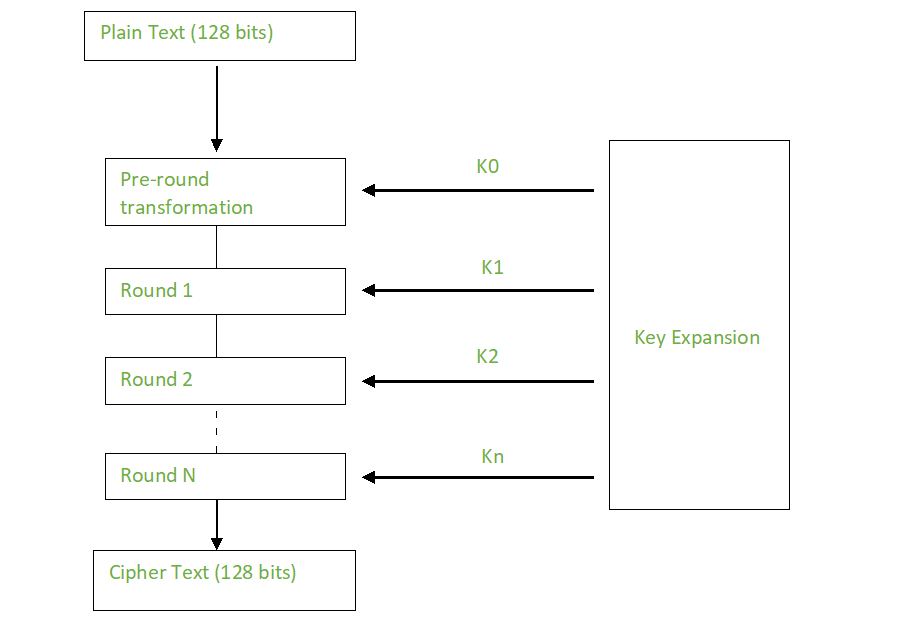
The Advanced Encryption Standard (AES) algorithm works by dividing the data to be encrypted into blocks of 128 bits and then using a series of mathematical operations to transform each block into a cipher block.
This section will explain how the AES algorithm works in detail.
The AES encryption algorithm uses a fixed block size of 128 bits and supports key sizes of 128, 192, and 256 bits. The key size determines the strength of the encryption, with larger key sizes providing greater security. The key is shared between the sender and the recipient of the encrypted data and is kept secret to prevent unauthorized access.
The AES encryption algorithm consists of four main operations:
- SubBytes
- ShiftRows
- MixColumns, and
- AddRoundKey
These operations are repeated several times, depending on the key size, to create multiple rounds of encryption. The number of rounds varies depending on the key size, with 10 rounds for 128-bit keys, 12 rounds for 192-bit keys, and 14 rounds for 256-bit keys.
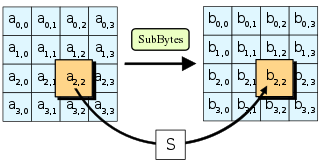
SubBytes
The first operation in the AES algorithm is SubBytes. In this operation, each byte in the input block is replaced with a corresponding byte from a fixed substitution table called the S-box.
The S-box contains a randomly generated permutation of all possible 8-bit values, which makes it difficult to determine the original data from the encrypted data.
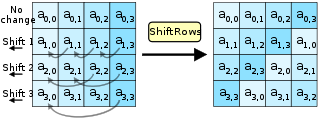
ShiftRows
The second operation in the AES algorithm is ShiftRows. In this operation, the bytes in each row of the input block are shifted a certain number of positions to the left. The first row is not shifted. The second row is shifted by one position to the left, two positions shift the third row to the left, and three positions shift the fourth row to the left.
This operation ensures that the data is spread across the block and reduces the correlation between adjacent bytes, making it more difficult to determine the original data from the encrypted data.
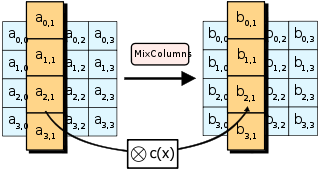
MixColumns
The third operation in the AES algorithm is MixColumns. In this operation, each column in the input block is multiplied by a fixed matrix, resulting in a new column.
This operation ensures that each byte in the output block is affected by multiple bytes in the input block, making it more difficult to determine the original data from the encrypted data.
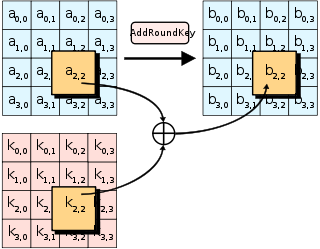
AddRoundKey
The final operation in the AES algorithm is AddRoundKey. In this operation, each byte in the input block is XORed with a corresponding byte from the key schedule generated from the original key.
This operation ensures that each output block byte depends on the key’s corresponding byte, making it impossible to decrypt the data without the correct key.
After the first round of encryption, the four operations are repeated many times, depending on the key size, to create multiple rounds of encryption. Each round uses a different key from the key schedule generated from the original key. The final round does not include the MixColumns operation, simplifying decryption.
Applications of AES Encryption
AES encryption can be used in many applications where sensitive data needs to be protected from unauthorized access. This includes secure communications, data storage, cloud computing, e-commerce, VPNs, and mobile applications.
Here are a few notable examples of AES encryption:
Secure Communications
AES encryption can secure communications between two parties, such as in email, chat applications, or instant messaging. It ensures that the data exchanged between them is protected from eavesdropping or interception by unauthorized parties.
AES Encryption can ensure secure communication between apps by providing confidentiality, integrity, and authentication of data transmitted between them.
Here are some ways that AES Encryption can ensure secure communication between apps:
Confidentiality
AES Encryption ensures confidentiality by encrypting the data transmitted between two apps. This means that even if an attacker intercepts the data, they cannot read it without the encryption key. This ensures that sensitive information, such as passwords, financial data, or personal identification information, remains private and secure.
Integrity
AES Encryption ensures integrity by using a message authentication code (MAC) to verify that the data transmitted between two apps have not been tampered with. The MAC is computed using a secret key and a hash function and is appended to the encrypted data. This ensures that if an attacker tries to modify the data, the MAC will not match, and the receiving app will know that the data has been tampered with.
Authentication
AES Encryption can also ensure authentication by using digital signatures to verify the identity of the sender and receiver of the data. Digital signatures are created using a private key and a hash function and can be verified using the corresponding public key. This ensures that the receiving app can trust that the data came from a trusted source and that it has not been tampered with in transit.
Key Exchange
To ensure secure communication, the apps need to establish a shared encryption key that is used to encrypt and decrypt the data. AES Encryption can ensure secure key exchange by using asymmetric cryptography, such as the Diffie-Hellman key exchange algorithm. This algorithm allows two parties to generate a shared secret key over an insecure communication channel without revealing the key to an attacker.
Data Storage
AES encryption can be used to secure data stored on devices or servers. This can include passwords, financial records, personal identification information, or any other sensitive data that needs to be protected from unauthorized access.
Cloud Computing
Cloud providers offer AES encryption for data in transit and data at rest. For example, Amazon Web Services (AWS) offers AES-256 encryption for its Simple Storage Service (S3) and Elastic Block Store (EBS) storage services.
E-commerce
AES encryption can help e-commerce websites protect sensitive information such as credit card details during online transactions by encrypting the data in transit, at rest, and using secure key management practices.
AES encryption can help e-commerce websites protect sensitive information, such as credit card details, during online transactions by encrypting the data before it is transmitted over the internet. This ensures that even if an attacker intercepts the data, they cannot read it without the encryption key.
Here are some ways that AES encryption can help e-commerce websites protect sensitive information during online transactions:
Transport layer security (TLS)
AES encryption can be used as part of the TLS protocol to encrypt data in transit between the user’s browser and the e-commerce website’s server. TLS uses symmetric encryption with AES to encrypt data, and asymmetric encryption with public key infrastructure (PKI) to securely exchange the encryption keys. This ensures that the data transmitted over the internet remains confidential and secure.
Payment Card Industry Data Security Standard (PCI DSS) compliance
AES encryption is recommended for protecting sensitive data under the PCI DSS standard. The standard requires that sensitive cardholder data be encrypted both in transit and at rest. Using AES encryption, e-commerce websites can ensure that they comply with the PCI DSS standard and protect their customers’ sensitive data.
Encryption of sensitive data
E-commerce websites can also use AES encryption to encrypt sensitive data, such as credit card details, before storing it in their database. This ensures that even if an attacker gains access to the database, they cannot read the sensitive data without the encryption key. The encryption key can be securely managed using key derivation algorithms, key wrapping, or hardware security modules (HSMs) to prevent unauthorized access.
Two-factor authentication
E-commerce websites can also use AES encryption in combination with two-factor authentication to provide an additional layer of security for online transactions. Two-factor authentication requires the user to provide two types of authentication, such as a password and a one-time code sent to their mobile phone, before a transaction can be completed. By using AES encryption to encrypt sensitive data and two-factor authentication to verify the user’s identity, e-commerce websites can ensure secure online transactions.
Virtual Private Networks (VPNs)
By using AES encryption and other security measures, VPNs can protect sensitive corporate data and prevent data breaches or leaks. This ensures that even if an attacker intercepts the data, they cannot read it without the encryption key.
Here are some ways that AES encryption can help VPNs secure data transmitted between remote users and corporate networks:
Tunneling
VPNs use a process called “tunnelling” to encapsulate and encrypt data before it is transmitted over the internet. The encrypted data is then transmitted through the tunnel and decrypted by the receiving VPN gateway. AES encryption can be used to encrypt the data transmitted through the tunnel, ensuring that the data remains secure even if an attacker intercepts the data.
Secure key exchange
VPNs use secure key exchange protocols such as Diffie-Hellman or Internet Key Exchange (IKE) to ensure that the encryption key used to encrypt the data is secure. These protocols allow the two endpoints of the VPN tunnel to securely exchange the encryption keys without exposing them to potential attackers.
Strong encryption
AES encryption is a strong encryption algorithm that many security experts recommend for securing data transmitted over the internet. VPNs can use AES encryption with a key size of 256 bits, which provides a high level of security against brute-force attacks.
Multi-factor authentication
VPNs can also use multi-factor authentication to provide an additional layer of security for remote users accessing the corporate network. Multi-factor authentication requires the user to provide two types of authentication, such as a password and a one-time code sent to their mobile phone, before accessing the network. Using multi-factor authentication combined with AES encryption, VPNs can ensure secure remote access to the corporate network.
Mobile Applications
AES encryption can help mobile applications protect data stored on the device by encrypting it before saving it to its storage. This ensures that the data remains unreadable and secure even if the device is lost, stolen, or accessed by an unauthorized user.
Here are some ways that AES encryption can help mobile applications protect data stored on the device:
File-level encryption
AES encryption can be used to encrypt individual files or directories on the device’s storage. This ensures that sensitive files, such as user credentials, financial data, or personal identification information, remain encrypted and secure even if the device is compromised.
Database encryption
AES encryption can also be used to encrypt the entire database used by the application. This ensures that all data stored in the database, such as user profiles, chat history, or transaction records, remains encrypted and secure.
Key management
To ensure secure data storage, the application’s encryption key must be securely managed. AES encryption can help mobile applications protect the encryption key by using key derivation algorithms, key wrapping, or hardware security modules (HSMs). This ensures the encryption key remains secure even if the device is compromised.
Authentication and access control
To ensure that only authorized users can access the data stored on the device, mobile applications must implement authentication and access control mechanisms. AES encryption can help mobile applications implement secure authentication and access control by encrypting the user’s credentials and using them to derive the encryption key. Only authorized users with the correct credentials can access the encrypted data.
How Secure is AES Encryption?
From a developer and application security point of view, Advanced Encryption Standard (AES) encryption is considered highly secure. It is widely used in many applications to protect sensitive information and has been extensively tested and evaluated by the cryptographic community.
One of the main reasons AES encryption is considered secure is its key size. AES supports key sizes of 128, 192, and 256 bits, meaning there are 2^128, 2^192, and 2^256 possible keys, respectively. This makes it practically impossible to break the encryption by brute force attacks, which involve trying all possible keys until the correct one is found. Even with the most advanced computers, trying all possible keys would take an impractically long time.
In addition to its large key size, AES encryption also uses a secure block cipher design based on the Substitution-Permutation Network (SPN) structure. This design ensures that the encryption process resists various attacks, including differential cryptanalysis, linear cryptanalysis, and algebraic attacks.
From a developer’s point of view:
AES encryption is relatively easy to implement and integrate into applications. Many libraries and frameworks provide AES encryption functionality, including OpenSSL, Microsoft’s CryptoAPI, and the Java Cryptography Extension (JCE). Developers can also use popular programming languages like Python, Java, and C++ to implement AES encryption.
From an application security point of view:
It is important to note that AES encryption is not a panacea for all security risks. While AES encryption can protect data in transit or at rest, it does not protect against other types of attacks, such as social engineering, phishing, or malware attacks. Developers should also ensure that the implementation of AES encryption in their applications is secure and follow best practices for key management, encryption mode selection, and handling of initialization vectors (IVs).
One common vulnerability in AES encryption implementations is the use of weak keys or IVs. Weak keys can make the encryption vulnerable to attacks, and weak IVs can lead to predictable ciphertexts, which attackers can exploit. Developers should ensure they use strong, random keys and IVs and avoid reusing them across different sessions or applications.
Another potential vulnerability in AES encryption implementations is side-channel attacks.
These attacks exploit weaknesses in the physical implementation of the encryption process, such as power consumption, electromagnetic radiation, or timing information, to recover the key or plaintext. Developers can mitigate the risk of side-channel attacks by using hardware security modules (HSMs) or software-based countermeasures, such as constant-time algorithms or random delays.
How AppSealing Helps
AppSealing is the best in the business when it comes to providing cloud-based in-app security solutions. Not only does it protect data, but it also offers valuable insights and threat analytics on attack vectors. Its security solutions can be implemented with zero coding and no negative impacts on app performance, without writing a single line of code.
AppSealing’s data encryption solution helps companies protect sensitive data like authentication tokens, unique identifiers, and passwords from unauthorized access and modification. Key features include:
- Whitebox AES 128 & FIPS 140-2 encryption
- RASP Security
- End-to-end support system
Using AppSealing, companies can keep their data safe and secure, ensuring that only authorized personnel can access and modify authentication tokens, unique identifiers, and passwords.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.