Digital platforms have opened countless opportunities for entrepreneurs to grow and expand their business with online sales that enable cashless transactions. However, this has also opened doors for online fraud and theft. Over 36 billion records were exposed due to data breach in the year 2020. Since online payments involve the exchange of credit card and debit card information, companies accepting online payments must adhere to certain operational and technical standards for processing payments, such as the PCI DSS. In this article, we will discuss PCI and the need to comply with PCI DSS standards in view of the emerging threats in the cyber landscape.
What is PCI DSS?
PCI DSS stands for Payment Card Industry Data Security Standard and it refers to cyber security standards that are intended to keep debit card and credit card information safe. The Payment Card Industry Security Standards Council is credited with the development of a cohesive set of standards for regulation of online payments.
American Express, Discover, JCB International, Mastercard and Visa Inc. founded PCI DSS in the year 2006 to assist merchants and financial institutions to protect cardholder data. Companies that fail to comply with PCI DSS will attract fines. PCI DSS is established with a sole aim to create a secure payment ecosystem.
Any entity that stores or transmits cardholder data should follow PCI DSS guidelines to thwart unauthorized access and attacks by malicious actors.
How does PCI DSS work?
PCI compliance is not a one time event. Entities need to be continually compliant with the security standards to adequately protect payment systems. Investing in PCI security procedures goes a long way in safeguarding the entity both in monetary and reputational terms.
PCI compliance comprises of three steps:
- Assess: In this step, the cardholder data is identified along with the IT assets and business processes involved in conducting the card transaction to detect vulnerabilities.
- Remediate: The detected vulnerabilities are fixed. Storing card data is avoided unless it is absolutely vital for smooth operation.
- Reporting: Reports are submitted to the acquiring bank and card brands. Reports are a way of declaring the entity’s compliance status.
The compliance procedures involve determining an organization’s PCI DSS level. The level is determined depending on the number of annual credit card transactions conducted. A self-assessment questionnaire needs to be filled by the organization. There are different questionnaires available depending on how each entity deals with credit card data. Click here to view all the Self-Assessment Questionnaires (SAQ) available for different types of merchants.
Some organizations have tie-ups with third parties whereas some accept payment through stand-alone payment terminals. Filling out the appropriate questionnaire will help you understand the areas of improvement. If the answers you fill are in adherence to the PCI DSS requirements, you are ready for attestation of compliance.
Who needs PCI DSS?
PCI DSS is applicable to any entity that stores or transmits cardholder data. That means any organization regardless of its size and number of transactions handled needs to adhere to PCI DSS. Even if an organization collects credit card information over the phone, adherence to PCI DSS is a must.
Any organization that sells products or accepts donations are required to follow best practices laid out by PCI DSS. The payment brands and acquiring banks are responsible for enforcing the compliance and not PCI SSC. A business need not adhere to all levels of compliance. There are several levels of PCI DSS compliance that vary with the number of transactions conducted by a business.
The PCI SSC serves financial institutions, merchants, point-of-sale vendors, and hardware and software developers involved in creating and maintaining the infrastructure that supports online payments.
PCI DSS Compliance Levels
There are four levels of compliance specified according to the number of transactions handled by an organization. Each business’ compliance journey varies depending on the levels of compliance. Below mentioned are the four levels of compliance that will help determine the category under which your organization falls and the subsequent compliance procedures to follow.
Level 1
An entity that processes more than six million transactions annually comes under level 1. Such an entity must go through an audit by an Internal Security Assessor or a Quality Security Assessor authorized by PCI. It is the most stringent of all levels.
Organizations that have suffered from a data breach in the past must also comply with level 1 PCI DSS procedures regardless of the number of transactions processed. Once a quarter, an Approved Scanning Vendor will also conduct a PCI scan.
Level 2
Entities that process anywhere between one and six million transactions annually must adhere to Level 2 compliance. Filling a self-assessment questionnaire is recommended for level 2 entities. They should also undergo quarterly ASV scans every quarter.
Level 3
Entities of level 3 are ones that process between 20,000 and one million transactions per year. These entities too, like level 2, are required to complete a self-assessment by filling the appropriate questionnaire. Quarterly external ASV scans are also a must.
Level 4
Merchants that process fewer than 20,000 transactions per year fall under level 4 category. Yearly self-assessment and quarterly PCI scan are compliance requirements for level 4 entities. On-site assessment can be conducted for all levels at merchant discretion.
PCI DSS Requirements
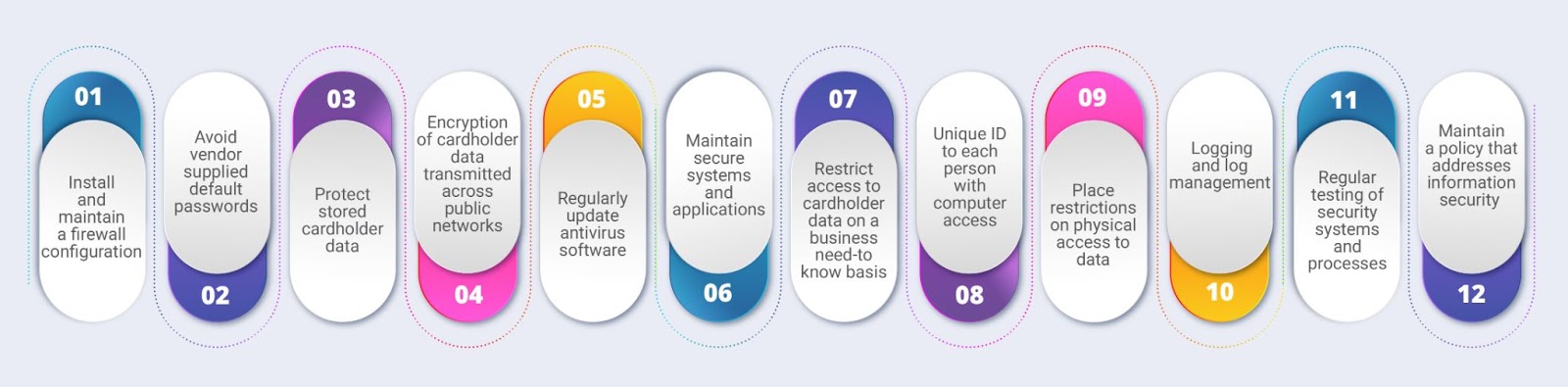
There are 12 requirements specified by PCI DSS with core focus on protecting cardholder data. Compliance with PCI DSS is governed by the contracts signed between merchants and the card brands or banks. Here are 12 important requirements that businesses must comply with :
Installation of Firewalls
Firewalls are a prerequisite for protection of card data environments. Service providers and merchants must install and maintain a firewall configuration to regulate access permissions. According to the rules and criteria laid down by your organization, firewalls will allow or deny access. Reviewing these rules is recommended bi-annually to ensure there are no access rules with compromised security.
Configure Passwords and Settings
Default usernames and passwords are insecure and are strictly not recommended. The default settings need to be changed to strengthen security. This second requirement lays focus on hardening servers, applications, firewalls and other wireless access points. It also requires the organization to maintain an inventory of all the systems and configurations.
Protect Stored Data
Determine the location and retention period of the card data to be stored. Ensure proper encryption of cardholder data. In addition, encryption keys to need to be protected. Primary account numbers (PAN) should not be displayed without implementing some restrictions. As per this requirement, only the first six and last four digits must be displayed. A data discovery tool will help locate unencrypted PAN in the system.
Encrypt Transmission of Cardholder Data
Entities must pay special attention to encrypting card data during transmission over public and open networks. Hackers can easily steal unencrypted data when transmitted to the payment gateway or processor. Implement secure transmission protocols to thwart unauthorized attempts to access data from processors, third parties, backup servers, corporate offices etc.
Update Antivirus Software and Programs
Malwares can adversely affect the system and deploying an antivirus program is an effective solution. It is important to update antivirus software regularly to keep known malware threats from penetrating the system. Verify if the antivirus software is using the latest signature and generates auditable logs.
Maintain Secure Systems and Applications
Security patches must be installed to prevent the exploitation of vulnerabilities in the systems. All the systems involved in the card data environment including POS terminals, operating systems, switches, routers, firewalls, application software, databases must be updated in adherence to the latest security standards.
Restrict Access to Cardholder Data
Access must be granted only on a business need-to-know basis. Implement a role-based access control system to prevent misuse of sensitive information. Prepare a list of all users who deal with card data by defining their roles, privilege level etc. among other such specifics.
Assign a Unique ID to Each User
This requirement prohibits the use of group or shared passwords. Every user who deals with cardholder data must be given a unique ID and password. Weak and guessable passwords are a threat to security. Passwords must be hard to crack and two-factor authorization is a must in case of remote access.
Restrict Physical Access to Cardholder Data
It is critical to implement physical access controls to protect systems with cardholder data. Video cameras and access control systems must be installed to track the movements of visitors. Any attempts of unauthorized access can be monitored and prevented at the right time. All media must be destroyed if it is no longer needed.
Log Management
This requirement deals with sending the logs to a centralized syslog server. Daily monitoring of logs is necessary to detect any suspicious activity. An audit policy is critical to protect all systems. Entities must strictly track all access to network resources and cardholder data.
Test Security Systems and Processes
Maintaining security is a never-ending process. New vulnerabilities and loopholes might be subject to exploitation by hackers. Frequent testing is the only way to stay compliant with all the
security standards.
Internal vulnerability scan and application and network penetration test for external IPs and domains must be conducted yearly without fail. A PCI ASV (approved scanning vendor) must quarterly inspect all external IPs and domains.
Maintain a Policy that Addresses Information Security
An information security policy must be maintained by businesses to comply with the final requirement. The policy must be disseminated to employees, contractors or vendors. Besides, entities must conduct risk assessments yearly and user awareness training along with background checks of employees and incident management.
PCI DSS Certification v/s PCI Assessment
Merchants and service providers must consult the acquiring bank or the payment brands to determine whether onsite PCI DSS assessments must be conducted for compliance. Usually, level 1 merchants are required to go through stringent assessments by Qualified Security Assessor (QSA) as these entities handle more than six million card transactions annually.
Is there such a thing called PCI DSS certification? The answer is no. Certification is not the right word to use. There are two types of assessment – self assessment and assessment by a QSA. Some entities refer to audit and assessment by QSA as a certification process. But it is important to note that entities can be PCI DSS compliant, not PCI DSS certified.
Level 1 merchants are required to compulsorily get their ROC (report of compliance) after thorough evaluation by a QSA. Some organizations may also choose to voluntarily pay for an on-site assessment by QSA. Organizations that suffered from a cybersecurity threat in the past must also go through an on-site assessment.
Level 2 to level 4 merchants can fill out the appropriate questionnaire and do a self-assessment. However, it is highly recommended for organizations to get an onsite assessment owing to its immense security benefits. Level 2 to level 4 merchants can proceed with an attestation of compliance (AOC) whereas level 1 merchants need both ROC and AOC. However, relying solely on self-assessments may create a false sense of security.
What Happens When You Fail to Comply with PCI DSS?
Non-compliance with PCI DSS can have serious consequences for your business. Being compliant with PCI DSS doesn’t mean there are zero chances of breach. But fulfilling the 12 PCI DSS requirements can significantly decrease the chances of a cyber attack. Merchants are required to agree to the terms of fines and penalties imposed by payment processors in case of non-compliance with PCI DSS.
The fine amount can vary from one payment brand to another. Large companies with huge volumes of transactions are subject to hefty penalties. Fine amounts are determined by
assessing the total number of months for which a company failed to comply and also the number of customers affected by breach. The per month charge increases if the company had functioned for longer periods without compliance.
A merchant is not just at risk of financial loss in cases of non-compliance. Security is heavily compromised and huge volumes of data are exposed. It may lead to termination of contract between merchant and card brands. On the other hand, if the data breach occurred even after full compliance, the card brands may lower the penalty amount imposed.
Legal consequences are another concern. A lawsuit can be filed against the entity for risking sensitive data. Reputation is damaged beyond repair and there will be a significant dip in revenue due to lack of trust among clients. PCI DSS is not a law per se but it is extremely risky for any entity to function without compliance due to the fines imposed by card brands.
Wrapping Up
PCI DSS stresses the importance of encrypting data with industry-accepted algorithms and protecting cardholder data from all kinds of online data manipulation and theft.
With cyber attacks increasing at an alarming rate, complying with PCI DSS has become more important than ever for businesses that value data protection and prioritize operating in a safe and secure environment.
It is vital for merchants to maintain PCI compliance to avoid all the security costs arising from compromised security measures. PCI compliance can also be leveraged to build a solid reputation. Merchants and service providers must comply according to their respective PCI DSS compliance levels if we collectively want to make cardholder data nearly unhackable.
Have questions about PCI DSS? Visit https://www.pcicomplianceguide.org/faq/ for more information.
AppSealing is a world-leading security solution provider for enhancing mobile app security. With patented application protection solutions for known and unknown threats, we have deep lying expertise in catering to industries such as fintech, games, movies among others. Guard your brand image, deliver a seamless user experience and create a trustworthy environment for all online transactions. Get in touch with us today to protect your applications from end to end with zero coding and stay in compliance with all security standards.
Frequently Asked Questions
1. What card data is covered by PCI DSS?
PCI DSS covers processes and systems used by vendors and merchants to protect information. It provides standards for managing cardholder data such as the cardholder’s name, card’s expiration date and security code and the primary account number.
2. What happens if you are not PCI compliant?
Non-compliance with PCI makes data vulnerable to attacks. It also leads to hefty penalties and fines. If a breach occurs due to PCI non-compliance, businesses are required to pay fines ranging between $5000 and $500000. It also leads to damaged reputation and revenue loss along with legal consequences.
3. Do all merchants have to be PCI compliant?
Any business or organization that accepts, transmits or stores cardholder data needs to be PCI compliant irrespective of the number of transactions handled by them.
4. Is PCI DSS a legal requirement?
PCI DSS is not exactly a law. However, PCI DSS can apply to merchants as a result of a contractual relationship between the merchant and card company. Certain states may also have incorporated portions of PCI DSS into state law.