Free Wi-Fi is hard to resist in public spaces like cafés, airports, or libraries, and while open networks are convenient, they come with a significant risk—the wily hook for the unwary fish. Cybersecurity threats love free Wi-Fi, and with unsecured networks, cybercriminals find a welcome mat to valuable personal and financial data. Most public network users have no idea how exposed their data is when connecting to these unsecured access points.
Here at AppSealing, we have witnessed the repercussions of these seemingly benign connections—a stolen identity here, a drained bank account there. But fear not, for knowledge is the torch that dispels the darkness of ignorance.
In this article, we’ll journey to decipher the cryptic signals of public unsecured Wi-Fi networks, wield the power of advanced network scanning tools, and adopt the vigilant gaze required to observe and understand network behavior.
Navigating the Risks of Using Unsecured Wi-Fi
Let’s embark on a journey through the dangerous realm of public Wi-Fi, where understanding and vigilance become your shields against the invisible threats that lurk within unsecured networks. May the knowledge in this article and vigilance guide you like a lighthouse through the hidden threats that surround you in unsecured networks – allowing you to survive unscathed with a moat filled with your protected personal data.
Infecting your device with malware
When an infected device connects to a compromised or unsecured public Wi-Fi network or downloads files from unreliable sources, attackers can exploit that network to distribute malware. Malware may silently install itself on devices, where it can steal personal data, spy on users, or use the infected machine to spread the malware further.
Additionally, unsecured Wi-Fi networks lack encryption, which means that data transmitted between your device and the network is sent in plain text. This makes it simple for anyone connected to the network to intercept your unencrypted data, including your personal details.
Here are some types of unsecured networks:
- Open networks: These networks have no password protection and can be accessed by any user within range.
- Wi-Fi Protected Access (WPA) networks with poor passwords: While WPA can be a secure choice, networks with poor passwords are often easily cracked, rendering the network open to nearby attackers.
Stealing your passwords
For a hacker, public Wi-Fi is a playground for stealing data. Unsecured, public Wi-Fi is a mecca for hackers—most of whom are happy to rifle through a victim’s data. With every packet that travels across the unencrypted network, a malicious packet sniffer has a front-row seat to all the traffic on the network.
When you sign in to a service or account on open public Wi-Fi, and you see that little pop-up saying it’s secured, it’s not quite the whole truth. Unlike a secured network where your network administrator can see you’ve accessed a page but nothing more, on open public Wi-Fi, when you enter your username and password, your login credentials are sent in plaintext. If your password is “I love dogs!” an attacker could eavesdrop on this so-called “plaintext” by simply driving by with a laptop.
Snooping for confidential data
We will show you how digital sleuths can snoop on your most confidential information in this wireless Wild West.
- Packet Sniffers: This virtual eavesdropper captures the data packets coursing through the network, essentially listening in on online conversations. It exposes unencrypted data such as website addresses and login credentials.
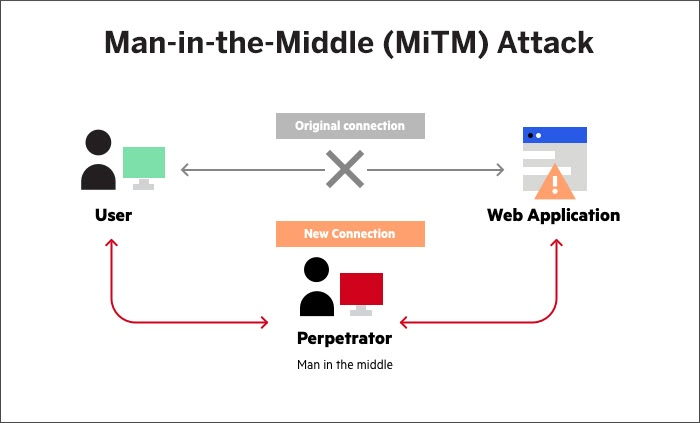
- Man-in-the-Middle (MitM) Attacks: In these covert operations, the hacker stations himself between your gadget and the website you’re attempting to visit, essentially an invisible middleman. This allows him to intercept and modify your data, including passwords and financial data.
- Evil Wi-Fi Networks: These are similar to fake Wi-Fi networks that can assume the name of the coffee shop. When an unknowing user, i.e., you, connects, their data is sent to the eavesdropping hacker.
- Data Interception: As you browse websites or engage in messaging, your data packets are wafting through the air. Their sniffing software then captures them, revealing everything – from your online activity to your password, in cases where it is unencrypted.
- Evil Twin Deception: You believe you’re connecting to a genuine network, but it’s a counterfeit. With every stroke of the key, every message is laying bare your sensitive details, including things like credit card information.
Business Email Compromise
Conducted by transnational criminal organizations using multiple methods — including social engineering, computer intrusions, and email spoofing — BEC is one of the Internet Crime Complaint Center’s (IC3) top complaints.
As an illustration of how the scam is sometimes carried out, consider this scenario:
You are at a conference with Wi-Fi, and you connect to your work email. In the same area, a cybercriminal on the conference Wi-Fi connection, armed with social engineering abilities and malicious tools, is on a mission: As you connect to the café’s free public Wi-Fi on your work laptop, you have no idea that the day’s digitally planned activities would conclude with underground hackers using it to breach the corporate email communications.
How the Attack Unfolds
A hacker employs a packet sniffer on your network to intercept your login credentials as they enter your corporate email account. With your username and password now compromised, the hacker logs in and sets up a forwarder to covertly CC themselves on all emails you receive moving forward.
Over the following weeks, the hackers mount a simple wiretap to watch communication patterns between you, key executives, partners, and clients. One day, they email one of your employees, Sam, as the CEO, attaching an urgent payment request they insist be processed immediately. Sam obeys, and in a very short time, a fraudulent wire transfer has released significant funds to the hackers.
When the company realizes they’ve been business email compromised, data loss and financial damage have been done. The hackers even exploit months of untimely email access to execute additional social engineering fraud, masquerading as partners and clients. All because sensitive login credentials and communications were intercepted in the open and transmitted through a single Wi-Fi network.
Ransomware attacks
Unprotected public Wi-Fi networks pose a significant risk, as attackers are taking advantage of the ease with which such networks can launch ransomware attacks on unsuspecting users. The low level of security of these widely used networks makes them an attractive location for attackers who can use them to gain a foothold and execute their malicious code.
How does a ransomware attack start?
With network agility, ransomware can spread easily from one machine to the next without the need for heavy internet traffic. An offsite user may struggle with malware that, though self-spreading, needs heavy internet traffic to find other machines to spread to them. Criminals went on to ransom your operating system and installed malicious software in place of a network resource.
The Tools of the Trade:
- Packet Sniffers: These function as network traffic eavesdroppers. Hackers can use them to paint a detailed picture of potential targets, identifying personal and work-related information. These tools can snoop more extensively and passively on unsecured Wi-Fi networks.
- Phishing Emails: Crafted with compelling narratives, these emails appear legitimate, often seeming to originate from high-level executives or HR. Hackers exploit compromised email accounts to send these deceptive emails, tricking recipients into opening malicious attachments or links.
- Drive-By Downloads: Merely visiting a compromised site can lead to victimization. The site may host covert code that activates upon your visit, downloading malware without your active engagement.
- Exploits: Hackers collaborate to create exploits for specific vulnerabilities, sometimes targeting zero-day bugs. If you interact with a malicious email or link, these exploits can deliver ransomware directly to your device.
Session hijacking
Session hijacking, sometimes called “token hijacking,” is an online attack where the attacker exploits a valid browser session to gain unauthorized access to information or services in a system. This type of attack targets the security information needed to hijack a user’s session with a service. Essentially, it involves converting the recognizable names we use on the internet into a complex string of numbers that the computers understand, allowing the attacker to connect and take control.
How does it work?
Monitoring And Interception
- Network Connection: The attacker is on the same unsecured public Wi-Fi network as you are.
- Traffic Sniffing: They use packet sniffing tools to observe the network traffic, identify active sessions, and intercept data being transmitted. This includes cookies and session tokens, which can be used to impersonate you.
Session Token Acquisition
- Token Seizure: Attackers capture the session tokens sent with each web server request. These tokens are usually meant to verify your identity, negating the need for repeated login credentials.
- Victim Identification: They may focus on specific individuals or services, particularly those involving valuable or sensitive information.
Taking Over The Session
- Session Cloning: The attacker uses the stolen session token to create a request that appears to come from your device, possibly by manipulating your browser or an automated script.
- Being The Victim: With the session token, the attacker gains access to services or information under your identity, sidestepping any login screens and security measures.
Data Access And Manipulation
- Unauthorized Access: They can now conduct unauthorized actions within your browser’s session, potentially accessing sensitive information, making transactions, or altering data.
- Maintaining Access: Efforts are made to keep the session active or to acquire further credentials for continued access, even after you end your session.
Covering Tracks Concealing The Attack
To avoid detection, the attacker may erase logs, blend their unauthorized actions with your normal activity patterns, or leave your session in a way that doesn’t change visible settings.
Taking over your online accounts
The general steps to the process of taking over your online accounts over public Wi-Fi include:
Targeting and Network Infiltration
- Opportunistic Targeting: The attacker chooses a public location with an unsecured Wi-Fi network and waits for potential victims, typically individuals casually using the network without awareness of the inherent dangers.
- Connection to the Network: The hacker connects to the same Wi-Fi network as the potential victims, enabling them to intercept data transmitted across the network.
Data Interception
- Traffic Monitoring: Using packet sniffing tools, the hacker monitors network traffic, capturing data transmitted over the network, including login credentials and session tokens.
- Eavesdropping: The attacker eavesdrops on communications between your device and the websites or services you access, explicitly looking for sensitive data.
Credential Acquisition
- Capturing Login Details: The hacker searches for unencrypted or weakly encrypted login attempts to capture usernames, passwords, and other authentication data.
- Phishing Tactics: Alternatively, the attacker might create a fake login page, such as a spoofed Wi-Fi login portal, to deceive users into voluntarily entering their credentials.
Account Takeover
- Using Stolen Credentials: Once in possession of your credentials, the hacker uses them to access your online accounts, such as email, social media, banking, or other services.
- Exploiting the Account: The attacker may use the compromised account to extract further information, commit financial fraud, or use your identity for other malicious activities.
Maintaining Access
- Changing Account Details: The attacker may alter your account’s password and recovery options, effectively locking you out and securing ongoing access for themselves.
- Installing Backdoors: In some scenarios, they might install malware or backdoors to retain access to the account, even if the password is changed later.
Targeting you with phishing attacks
Phishing attacks, a prevalent form of social engineering, trick users into divulging sensitive details such as login credentials or credit card numbers. When orchestrated over inadequately secured public Wi-Fi networks, these schemes are particularly menacing, allowing hackers to intercept and manipulate communications undetected.
How the Attack Unfolds
- Setting the Stage
- Network Selection: Attackers pinpoint public Wi-Fi networks bustling with activity. They might erect a rogue Wi-Fi access point, mirroring the name of a genuine one (like “Cafe_wifi_Free”), or leverage an already unsecured network to stage their attack.
- Monitoring: Upon connection by users to the vulnerable or rogue network, attackers scrutinize the data flowing over the network to pinpoint potential victims.
- Monitoring and Intercepting
- Traffic Monitoring: Once users connect to the unsecured or rogue network, the attacker monitors the data transmitted over the network, looking for potential targets.
- Interception: They deploy packet sniffing tools to capture any unencrypted data transmitted by users, scavenging for valuable information to harness in the phishing attack.
- Crafting the Phishing Attack
- Phishing Content Creation: Attackers craft cunning emails, messages, or web pages designed to deceive users into surrendering sensitive information, often mimicking the appearance and tone of authentic institutions such as banks, social networks, or payment services.
- Triggering the Attack: These phishing messages are dispatched to users on the network. In certain instances, users’ web traffic might be rerouted to fraudulent websites under the attacker’s control.
- Collecting Sensitive Information
- User Interaction: Unwittingly, users might engage with a phishing email and proceed to click a link that redirects them to a counterfeit login page.
- Data Harvesting: Any sensitive information users enter, like login credentials, is directly funneled to the attacker.
- Exploiting the Stolen Information
- Immediate Use: The attacker might promptly exploit the stolen credentials to breach the victims’ accounts, paving the way for financial theft, identity theft, or other malicious endeavors.
- Long-term Exploitation: The harvested information often finds its way into the murky realms of resale or serves as fodder for future targeted attacks.
Gaining remote control of your device
Gaining remote control over a device through an unsecured public Wi-Fi network is a formidable attack that enables an attacker to covertly infiltrate and dominate a device. The primary objective is to deploy a Remote Access Trojan (RAT) or comparable malware, granting the attacker dominion over the device.
How the Attack Unfolds:
Target Identification and Network Infiltration
- The attacker selects a public location with an unprotected Wi-Fi network and patiently waits for potential victims, typically individuals using the network without caution.
- The attacker then connects to the network and begins monitoring traffic, scouting for devices susceptible to attack.
Exploitation and Malware Delivery
- The attacker examines the connected devices for known vulnerabilities, like outdated software, inadequate encryption, or neglected security patches.
- Employing various methods, such as phishing emails, malicious downloads, or exploiting network vulnerabilities, the attacker transmits malware to the targeted device. This malware is often a RAT, enabling remote control by the attacker.
Gaining Remote Access
- Execution of Malware: The user, oblivious to the threat, triggers the malicious payload by opening a deceptive email, downloading a tainted file, or the malware itself exploiting a vulnerability for self-installation.
- Establishing Control: The malware forges a link back to the attacker, granting them remote control over the device. The extent of control can vary from executing basic commands to complete authority, depending on the malware’s capabilities.
Conducting Malicious Activities
- Data Theft: The attacker can access, alter, or steal personal data, sensitive corporate information, or intellectual property.
- Surveillance: Activation of microphones or cameras for spying or surveillance might occur.
- Spreading Malware: The compromised device may serve as a springboard to infect other devices on the same network or propagate the malware even further.
- Resource Hijacking: The device’s resources might be exploited for cryptocurrency mining, initiating DDoS attacks, or other evil pursuits.
Maintaining Persistence
- Installing Backdoors: To maintain access, the attacker might embed additional software, ensuring control persists even if the original malware is discovered and removed.
- Concealing the Attack: The attacker typically takes measures to obscure their malevolent activities from both the user and security software, ensuring prolonged access.
As we’ve navigated through the intricate landscape of cybersecurity threats associated with unsecured public Wi-Fi networks, it’s abundantly clear how these vulnerabilities serve as gateways for many sophisticated cyber-attacks.
Different cases of attacks stemming from unsecured Wi-Fi usage
Let’s explore a series of real-world incidents that starkly illustrate the risks and repercussions of using unsecured wireless networks.
Evil twin attack
An evil twin attack is a sophisticated cyber threat, a man-in-the-middle attack, that lets a hacker intercept your data covertly. By setting up a rogue Wi-Fi network, the hacker can reroute your connection and filter your traffic without your knowledge. You might see a network that looks familiar, connect to it, and use it as usual. However, unbeknownst to you, it’s a counterfeit network. Your data then passes through the hacker’s network, where they can harvest your usernames, passwords, and any other transmitted data.
Critical Elements of an Evil Twin Attack:
The Fake Network: Hackers create networks that closely resemble legitimate ones, sometimes with minor differences in name or logo, to deceive users.
Unsuspecting Users: You unknowingly connect to the hacker’s network, believing it genuine.
Man-in-the-Middle: Your device interacts with the hacker’s network, enabling them to intercept your data.
Stolen Information: Hackers can capture a wide range of your data, including login credentials, emails, and banking details.
Man-in-the-Middle Attack (MitM): A man-in-the-middle (MitM) attack is an eavesdropping tactic where a hacker intercepts and potentially alters communications between two parties. It’s a long-standing method, particularly in public Wi-Fi hotspots.
How it unfolds:
- The Hidden Intruder: The hacker discreetly positions themselves between your device and the intended website, effectively becoming a silent intermediary.
- Intercepted Traffic: Your data, whether login details or messages, gets routed through the hacker’s device, allowing them complete visibility.
- Data Theft: The hacker then pilfers your personal information, such as passwords or credit card numbers.
- Possible Manipulation: Sometimes, they might even tweak your data before it reaches its destination, deceiving either you or the intended recipient.
Password Cracking Attack:
Password cracking in unsecured Wi-Fi scenarios involves an attacker capturing and deciphering passwords that’re transmitted over networks lacking adequate security. Particularly in public Wi-Fi hotspots, where security is often minimal, these vulnerabilities are exploited to seize sensitive information, notably passwords.
Here’s the breakdown:
- Data Sniffing: Hackers employ software to capture data in transit, including unencrypted login attempts, whether for email, social media, or the Wi-Fi itself.
- Cracking Tools: With the captured password, hackers use sophisticated software to try various letter, number, and symbol combinations until they crack your account.
- Rainbow Tables are pre-calculated lists containing millions of password combinations, expediting the cracking process for commonly used passwords.
- Brute-Force Attacks: This method systematically attempts every possible password combination until the correct one is found. While slower, it’s a surefire way to crack weak passwords.
Packet Sniffing Attack:
Packet sniffing is an attack where eavesdropping software captures data traveling over a network. On public Wi-Fi networks that lack encryption, conducting packet sniffing attacks is incredibly simple. Data transmitted over these unsecured networks can be intercepted, making them a hacker’s playground.
What happens:
- The Eavesdropping Software: A packet sniffer acts like a virtual wiretap, capturing unencrypted data packets as they travel across the network, akin to catching fragments of conversations.
- Unsecured Wi-Fi as the Accomplice: Most public Wi-Fi networks don’t use encryption, broadcasting your data packets like unsealed letters, making them easily accessible to hackers.
- What Information Gets Captured: Anything sent unencrypted is at risk. Everything from website addresses to private messages, login credentials, and browsing history can be intercepted. It’s as if the hacker is sifting through your open letters or listening to your phone calls.
Security vulnerabilities and/or misconfigurations
Most public Wi-Fi networks’ open and unregulated nature provides a perfect breeding ground for hackers to exploit vulnerabilities and configuration weaknesses, often allowing them effortless entry. Without solid security measures, both hotspot users and hosting networks might unknowingly present attack surfaces, which are easily pinpointed and exploited by cyber thieves lurking in the shadows.
For instance, attackers can methodically scan devices connected to these networks for unpatched operating systems or outdated embedded software. Discovering these vulnerabilities essentially hands hackers predefined pathways, needing nothing more than readily available exploit code to hijack devices and broaden their attack to encompass entire networks.
Moreover, network administrators’ occasional oversight can leave backend systems and cloud management platforms exposed on these unsecured Wi-Fi networks. Recognizing these blunders, cybercriminals can effortlessly access control panel functions, redirect user traffic toward malicious sites, disseminate malware, or orchestrate sophisticated man-in-the-middle attacks.
Encryption HTTPS vs HTTP
It’s important to understand that while phishing websites can use encryption certificates, these certificates don’t inherently make the website legitimate or trustworthy.
- Encryption certificates primarily verify the website owner’s identity, not its legitimacy. They ensure the data you send to the website is encrypted during transit, protecting it from eavesdroppers.
- Phishing websites can obtain valid encryption certificates from various certificate authorities (CAs). Some CAs have stricter vetting processes than others, but even then, malicious actors can exploit loopholes or provide misleading information to obtain certificates.
- Seeing a padlock icon or “https” in the address bar doesn’t guarantee a safe website. It simply indicates that the connection is encrypted, not that the website itself is trustworthy.
Evolution of Wifi security protocol
WEP (Wired Equivalent Privacy): When it was first introduced as part of the original 802.11 standard in the late 1990s, WEP was the first encryption protocol to be widely used in Wi-Fi networks. While this early standard was intended to give wireless networks comparable security to that of wired networks, it had a number of design flaws — such as the use of static encryption keys and predictable algorithms — that made it vulnerable to a variety of different attacks. WEP was eventually deprecated as it was determined to be insufficient for protecting any data of importance.
WPA (Wi-Fi Protected Access): Designed as an intermediate solution to the weaknesses of WEP, WPA was designed to provide greater security without the need for new hardware. It incorporated Temporal Key Integrity Protocol (TKIP), which automatically generated new encryption keys and included a message integrity check to prevent the types of attacks that plagued WEP. Though this protocol was a significant improvement, it was still built on the back of WEP and was not impervious to all attacks.
WPA2 (Wi-Fi Protected Access 2): In 2004, the Wi-Fi Alliance rolled out WPA2, which represented a significant step forward. Among other differences, WPA2 replaced WPA’s use of TKIP with the much more secure Advanced Encryption Standard (AES) for the encryption/decryption of transmitted data. Roxane Suau, the marketing and communication manager for the Wi-Fi Alliance, told Digital Trends that WPA2 offered “modern, strong security” to Wi-Fi networks and essentially made it much harder for hackers to breach a network.
WPA3 (Wi-Fi Protected Access 3): The third and most current version of the Wi-Fi Protected Access protocol, WPA3 was announced in 2018. WPA3 builds on the limitations of its predecessors by offering additional protection against offline password-guessing attacks, more robust encryption for open/public networks, and simplified security for devices that have limited display/user interface capabilities. The adoption of this standard heralds a significant step forward in Wi-Fi security in that it aims to provide strong protections even as the range of cyber threats continues to evolve.
11 Essential Cybersecurity Practices for Safe Public Wi-Fi Usage
Navigating the digital world safely, especially on public Wi-Fi, requires some key preventative measures. These 11 critical tips will allow you to put up a comprehensive shield that will fortify your online presence against a variety of cyber threats. From deploying robust encryption, to being vigilant about your network interactions, you’ll find everything you need in this guide to be certain that your online experience is worry-free and fully protected, even in a public setting.
Tip #1: Steer Clear of Sensitive Data on Public Networks: Given that public Wi-Fi networks are typically unsecured, it’s important to avoid accessing sensitive information on them. This includes bank accounts, and even confidential work emails.
Tip #2: Use VPNs on Public Wi-Fi: A VPN (Virtual Private Network) encrypts your internet connection, meaning that any data you send and receive is unreadable to anyone who may intercept it. This provides protection for your sensitive data even while you are connected to public Wi-Fi, and is therefore an important tool for online privacy and security.
Tip 3# Visit Only SSL-secured Sites: A quick and easy way to tell if a website has an SSL (Secure Socket Layer) certificate is to look at the address bar. Sites with an SSL certificate have URLs that begin with ‘HTTPS’, and often have a padlock icon appear in the address bar as well. SSL certificates ensure that data transferred between your web browser and the website’s server is encrypted, adding security against eavesdroppers and data thieves who may be lurking on an unsecured network.
Tip #4: Use browser security extensions: Look for browser extensions that offer security features, such as ad-blocking, anti-tracking, and HTTPS enforcement. These tools can fend off malicious ads, stop websites from tracking our online activity, and make sure we are always using a secure, encrypted connection.
Tip #5: Disable Auto-Connect to Wi-Fi hotspots: Disabling auto-connect for Wi-Fi reduces the chance of unknowingly connecting to a potentially insecure or malicious network. Being selective about our connections helps to secure our data and ensures we are only joining networks deemed trustworthy.
Tip #6: Install Device Privacy Screens: Privacy screens restrict the viewing angle so that only the person directly in front of the screen can see a display clearly. This prevents “shoulder surfing,” where someone may look over our shoulder to steal sensitive information or passwords. It’s a simple but effective physical barrier to protect our data from prying eyes.
Tip #7: Deactivate File Sharing: Before you go on public Wi-Fi, turn off file sharing on your computer. That way, unauthorized people won’t be able to access your files and it reduces the chance of a cybercriminal to hack into your system and grab your personal information. This is essential to maintaining your privacy while connected to a network that is potentially unsecured and accessible by unknown users.
Tip #8: Enable two-factor authentication (2FA) for your passwords: Turn on two-factor authentication (2FA), which is an extra step to secure your account — especially when using public Wi-Fi — because it requires two forms of identification to log in: your password and a second contact method, such as a type-in code sent to your phone or a thumbprint. Even if someone does get your password through hacking on public Wi-Fi, they can’t access your account without the second form of identification.
Tip #9: Regularly Update OS: OS updates often include critical security patches to address vulnerabilities that attackers could potentially exploit on an unsecured network, reducing the likelihood that your device will be compromised. Keeping your software up to date gives you the latest defenses against potential attacks, providing a solid foundation for securing your device.
Tip #10: Log Out After Use: Always log out of any services used after connecting to public Wi-Fi. This ensures that your device will “forget” the network, so it will not reconnect automatically to that network again if you’re within range, without your permission. Logging out from any services used while connected to public Wi-Fi is also important to help make sure your device does “forget” the network, preventing it from automatically reconnecting to potentially insecure or malicious networks in the future without requiring permission.
Tip #11: Install Robust Antivirus: Antivirus software provides real-time protection against malware and other cyber threats, actively scanning and removing any malicious content that could compromise your device.
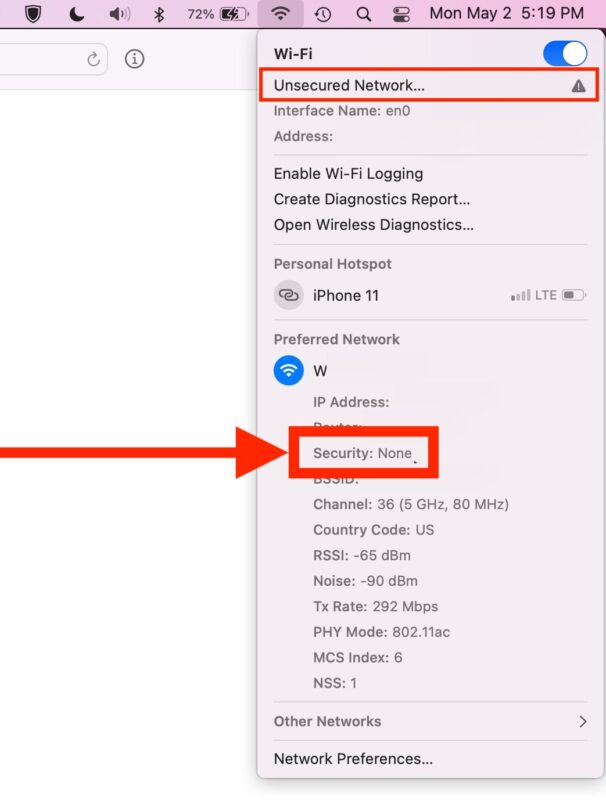
The best way of protecting ourselves from these attacks is to stay alert or completely stop the usage of unsecured wifi. AppSealing offers a robust Wi-Fi security feature designed to identify unsecured networks promptly. Through proactive alerts, users are promptly notified, ensuring comprehensive awareness of potential network vulnerabilities. This empowers users to make informed decisions regarding the utilization of unsecured Wi-Fi, thereby enhancing overall network security and user safety.