Mobile devices have become more popular than desktops and laptops. Not only are they easy to carry, but technological advancements have also enabled them to perform nearly similar functions as desktops do. According to Techjury.net, over the course of the last one year, mobile users have increased by over 10 percent and nearly 51 percent of the time spent by users online in the USA is on mobile devices.
Users engage in nearly all activities on mobile devices, right from watching the news to checking emails, instant messaging, purchasing items online, and doing bank transactions. Through these apps, businesses can gather usable information, such as the location, usage statistics, phone number, likes, dislikes, and other meaningful metrics about users, which can help businesses make precise decisions to improve their services. If the data in these mobile devices go in the wrong hands, it can be harmful to the user.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.

What is Application Security?
Application security is a measure to secure applications from external threats like malware and other digital frauds that risk critical personal and financial information from hackers.
Mobile application security has become equally important in today’s world. A breach in application security can not only give hackers access to the user’s personal life in real-time but also disclose data like their current location, banking information, personal information, and much more.
Application Security Based on Functions
Authentication:
Maintaining the security of sensitive data and mission-critical components of an application is paramount to prevent data breaches. Unfortunately, unauthorized access poses a significant security risk related to user identities, caused by weak authentication mechanisms, compromised credentials or session hijacking. To ensure that only authorized users can access your application’s important aspects, you must implement robust authentication measures. Authentication plays a crucial role in establishing secure session management and verifying the identity of users attempting access. By implementing strong verification methods for all identities involved with your application, developers can significantly reduce the threat posed by unauthorized access attempts
Here are some ways to achieve this:
- Implementing secure authentication mechanisms, such as multi-factor authentication (MFA), helps ensure that only legitimate users can access the application. MFA requires users to provide at least two forms of verification, such as a password and a one-time code sent to a registered device, making it more difficult for attackers to gain unauthorized access.
- Enforcing strong password policies, including minimum length, complexity requirements, and regular password changes, helps minimize the risk of compromised credentials. Additionally, implementing a secure password storage mechanism, such as hashing and salting, prevents attackers from easily obtaining plaintext passwords in case of a data breach.
- Proper session management is critical for maintaining user security throughout their interaction with the application. Developers should use secure cookies with the HttpOnly and Secure flags, implement session timeouts, and generate unique session IDs to prevent session hijacking and fixation attacks.
- Implementing role-based access control (RBAC) or attribute-based access control (ABAC) ensures that users can only access resources and perform actions based on their assigned roles or attributes. This helps in limiting access to sensitive data and mission-critical components of the application.
- Validating and sanitizing user input is essential to prevent security vulnerabilities like SQL injection or cross-site scripting (XSS) attacks, which could potentially bypass authentication mechanisms or expose sensitive data.
- Encrypting data in transit using protocols like HTTPS (with TLS) protects sensitive information from being intercepted or tampered with by attackers.
- Implementing a comprehensive logging and monitoring system allows developers to detect and respond to potential security incidents promptly. Monitoring failed login attempts, unauthorized access attempts, and unusual user behaviour can help identify potential threats and mitigate risks.
Authorization:
Securing applications and resources through proper authorization procedures is crucial to ensure that users only have access to the appropriate level of functions, such as files, databases, locations, funds, or administrative tasks.
However, one major security issue related to user authorization is insufficient or improper access control. This can result in unauthorized individuals gaining access to sensitive information and resources beyond their intended level of permission or even escalating their privileges within the system. Therefore, it’s essential always to implement thorough and effective authorization protocols for your application – this will provide peace of mind knowing that data remains safe and secure while also helping you build trust with your clients by demonstrating a commitment towards securing their confidential information at all times.
To address these security issues, application developers can implement the following three authorization approaches for application security:
Token-based Authorization:
In token-based authorization, access tokens are used to grant permissions to users. When a user successfully authenticates, the system issues an access token (e.g., JSON Web Token or JWT) containing user information and the scope of their allowed actions. The user then presents this token with each subsequent request, allowing the server to verify the user’s identity and permissions without repeatedly checking their credentials.
Role-Based Access Control (RBAC):
RBAC involves assigning roles to users, with each role having a predefined set of permissions that determine what actions they can perform within the application. Users can only access resources and perform actions based on their assigned roles. RBAC simplifies the management of access control by allowing developers to define roles with specific permissions rather than assigning permissions to individual users.
Access Control Lists (ACL):
ACLs are a more granular approach to authorization, where permissions are explicitly defined for each user or group of users on specific resources. An ACL is a list of rules that define which users or groups can perform certain actions (e.g., read, write, delete) on specific resources (e.g., files, databases).
Encryption
Developers can build robust data encryption into their applications, ensuring that sensitive data remains secure during transmission between end users and the cloud. This approach significantly reduces the risk of unauthorized access, tampering, or MitM attacks, ultimately maintaining the confidentiality, integrity, and availability of the data.
One of the most widely used security protocols for this purpose is HTTPS (Hypertext Transfer Protocol Secure), which relies on the Transport Layer Security (TLS) protocol or its predecessor, Secure Sockets Layer (SSL). HTTPS ensures that data transmitted between the end user’s device and the cloud server is encrypted, preventing eavesdropping or interception by malicious actors.
Here are some essential steps to build encryption procedures into an application and protect data in transit:
Use HTTPS for all Communication:
Implement HTTPS across the entire application to encrypt data transmitted between the end user and the cloud server. This provides confidentiality, integrity, and authentication, ensuring that sensitive data remains secure during transmission.
Obtain and Install a Valid SSL/TLS Certificate:
Obtain an SSL/TLS certificate from a trusted certificate authority (CA) and install it on the server hosting the application. This certificate validates the server’s identity, ensuring that users connect to the legitimate server and not an impostor.
Enable HTTP Strict Transport Security (HSTS):
HSTS is a security policy mechanism that enforces the use of HTTPS for all connections, preventing unencrypted HTTP connections and reducing the risk of MitM attacks. Configure the server to send an HSTS header with a suitable max-age value to enforce HTTPS.
Configure SSL/TLS Settings:
Properly configure SSL/TLS settings on the server to ensure secure connections. Disable outdated and vulnerable protocols (e.g., SSL 2.0, SSL 3.0) and weak cipher suites. Use only strong cipher suites and enable features like Perfect Forward Secrecy (PFS) for enhanced security.
Encrypt Data Payloads:
In addition to encrypting data in transit, consider encrypting sensitive data payloads at the application level. This adds an extra layer of security, making it more difficult for attackers to access or manipulate the data, even if they manage to intercept the encrypted communication.
Implement Certificate Pinning:
Certificate pinning is a technique that ensures the application only trusts a specific SSL/TLS certificate or public key for a particular domain, reducing the risk of MitM attacks using fraudulent certificates. Implement certificate pinning in the client application to verify the server’s certificate against a known, trusted version.
Challenges of Application Security
Inherited Vulnerabilities:
These are security flaws that arise from using pre-existing code, frameworks, or libraries in a new application. Inherited vulnerabilities can be introduced if the dependencies being used have not been properly vetted, or if they are not regularly updated to include the latest security patches. This can lead to potential security risks, as attackers can exploit these known vulnerabilities to gain unauthorized access or compromise the application.
Third-party and Open-source Vulnerabilities:
Many applications today rely on third-party and open-source components to speed up development and leverage existing solutions. However, these components may contain security vulnerabilities that can be exploited by attackers. It is crucial to monitor and manage these dependencies, ensuring that they are up-to-date and free from known vulnerabilities.
Adopting a DevSecOps Approach:
DevSecOps is a philosophy that aims to integrate security practices into the entire development lifecycle. It requires close collaboration between development, security, and operations teams, which can be a challenge for organizations that are not accustomed to this level of collaboration. Additionally, adopting DevSecOps requires a cultural shift and investment in training, tools, and processes, which can be time-consuming and costly.
Finding Qualified Experts:
The field of application security is complex and constantly evolving, making it difficult to find and retain qualified experts who can effectively address security challenges. This skill shortage can lead to inadequate security measures and increased risk of vulnerabilities being introduced into applications.
Lack of a Centralized Management Tool:
Many organizations struggle to manage application security effectively due to the lack of a centralized tool that provides visibility and control over their entire application portfolio. Without a centralized management tool, it becomes challenging to identify vulnerabilities, track remediation efforts, and ensure compliance with security policies and standards. This can lead to a fragmented security posture, where some applications may be well-protected while others remain vulnerable to attacks.
Mobile App Security Best Practices
The best practices of mobile app security ensure that the app is risk-free and does not disclose the personal information of the user. It is important for the developer to ensure that all security checks are performed before the app is uploaded on an app store for public consumption. Public-facing applications that are often the sole communication bridge between customers and the organization are the primary targets of hackers. Most public-facing applications are designed keeping in mind that they have to be compatible with almost any device in the market. But, this approach makes the application vulnerable to attacks and manipulation. Developers must maintain the most stringent filter mechanisms while building a watertight application that is capable of thwarting any possible attacks.
Risk Analysis
To zero in on the specific warnings, developers can run a threat-modeling exercise. The most common risks that organizations which bank on mobile applications for conducting their business face are as follows:
- Data leaks: Applications with porous firewalls are at constant risk of being breached by miscreants who can obtain confidential data, such as payment credentials, system passwords, and PINs. Once the firewall is penetrated, malware can also be injected into the device.
- Infrastructure exposure: For communication between mobile applications and the organization’s backend services, sharing of resources, such as a third-party API, may be required. If the process of API integration is not monitored carefully, it can compromise not just the user data that lies in the device but also compromise the server-level security.
- Scams: Any mobile application developed to carry out financial transactions will always be under the radar of fraudsters. There is always some risk involved when the application utilizes sensitive data, like payment credentials, PINs, and passwords associated with apps and credit cards, etc. Miscreants, armed with various attack methods, like SMS grabbing via malware, script injection, and repackaging, are always on the prowl.
- Regulations and guidelines: All applications have to function within a legal and social framework, and breaching them can invite legal action. For example, the General Data Protection Regulation and the Revised Payment Services Directive are a few of the regulations that apply for operating in European nations, while there are several other guidelines apply in the global context.
Right Architecture
The first thing to consider is whether the application is released on a commercial store or disseminated through the organization’s distribution channel. It is no secret that applications distributed through private carriers are less likely to face threats like reverse engineering. There are several mechanisms, like application management through UEM and stand-alone solutions, that can be employed to keep the application secure. Currently, there are three kinds of architectural options available for mobile application development: Native, hybrid, and pure web-based. All the options have their pros and cons where one has to either compromise security or performance. For example, converting an organization’s web application to a mobile application is not a tough ask, but encrypting the cached content of the application becomes a time-consuming and costly affair. If the cached content is reduced and discarded more often to boost the security front, it could adversely affect the performance of the application. These factors should be kept in mind before taking the architectural call. Another point that developers need to deliberate over is choosing device- or server-side checks. Hackers often tend to breach device security walls by tinkering with the application or device.
A jailbroken device, for instance, can make a mockery of native check mechanisms. The one-size-fits-all approach may not work in application development. Some applications might need server-side controls while for others, device check may work out better.
Native application development opens the door to all native security potentialities of the operating software platforms. They tend to work more smoothly since they rely on the API from the operating software. Both popular operating software Android and iOS have already best practices guidelines in place that developers can follow. These native environments are capable of fulfilling both basic and advanced requirements. However, in the native development process, two unique versions of the applications need to be sustained. From simple functions such as authentication and encryption to complex like device attestation and storage of credentials are supported by these native environments. While for competitive applications native route seems ideal, but for others, hybrid architectures may prove to be a more viable option. The hybrid architecture allows the usage of cross-platform frameworks like Xamarin and Flutter. Sensitive activities in hybrid applications can be carried out using native tools.
Most principles of secure software development apply to mobile applications as well. However, when it comes to mobile applications, developers have certain key areas they need to focus on to get the best results. Here are a few practices endorsed by industry experts:
Minimal Application Permissions
Permissions give applications the freedom and power to operate more effectively. But, at the same time, they make apps vulnerable to hackers’ attacks. No application should seek permission requests beyond its functional area. Developers should avoid recycling their existing libraries but build new ones that selectively seek permission.
Guarding sensitive information
Confidential data stored within the application without a proper guarding mechanism in place is prone to attacks. Miscreants can extract vital information by reverse-engineering codes. If possible, the volume of data stored on the device should be cut down to minimize the risk.
Certificate Pinning
Certificate pinning is an operating procedure that helps applications defend against man-in-the-middle attacks while connected on unsecured networks. The technique, however, has its own limitations. In some cases, it may not support network detection and response tools as traffic inspection becomes a more arduous task. There are compatibility issues that can pop up as well. Certain browsers do not aid certificate pinning, making life tougher for hybrid applications to work.
Enhance Data Security
Data security policy and guidelines should be established to ensure users can easily avoid getting caught in the trap of hackers. This can include having well-implemented data encryption when the information is transferred between devices and using firewalls and security tools whenever necessary. You can refer to the guidelines laid down for Android and iOS.
Not Saving Passwords
Many apps request users to save passwords in order to prevent them from repeatedly entering the login credentials. In an event of mobile theft, these passwords can be harvested to gain access to personal information. Similarly, if the password is saved in an unencrypted format, the chances of them being harvested are very high. To prevent this from happening, developers should refrain from saving passwords on mobile devices. Instead, they should be saved on the app server, so that the affected users can change them by logging on to the server even if the mobile device is missing.
Enforce Session Logout
It is often seen that users forget to log out of the website or app they are using. If it is a banking app or any other payment app, this can be harmful. For this reason, payment apps tend to end the session of a user after a certain period of inactivity or on every logout for increased safety. Developers must enforce a session logout on all business and consumer-centric apps, even if they expect their users to be highly literate.
Consult Security Experts
No matter how experienced an internal security team is, an external point of view on the apps can give a different perspective. There are several security companies and apps which can be deployed in identifying the loopholes and reduce the chances of getting compromised. Companies should encourage their development teams to get the security features of their apps assessed by third-party service providers.
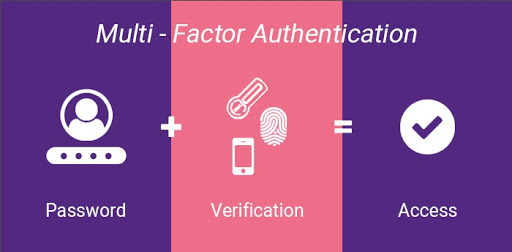
Apply Multi-Factor Authentication
Multi-Factor Authentication adds an extra layer of security when a user logs into an app. The multifactor authentication method also covers up for weak passwords which can be easily guessed by hackers and compromise the security of an app. The multifactor authentication provides a secret code that must be entered along with the password to log into a device or app. This code is either sent through SMS, email, Google Authenticator, or biometric methods. Not enforcing multi-factor authentication on the app can allow hackers to guess weak passwords.
Source: Avatier
Penetration Testing
Penetration testing is done to check known vulnerabilities in an app. It aims to find potential weaknesses that an attacker might use and compromise the security of the final application. It involves checking weak password policy, unencrypted data, permissions to third-party apps, no password expiry protocol, etc. By recreating the acts of a potential hacker, the security team determines if there is any weakness in the app. It is recommended that penetration testing is performed regularly to keep the app secure. White box testing and black box testing are other types of penetration testing measures that can be undertaken to check for security issues.
Source: SecureOps
Prevent Usage of Personal Devices
To prevent the overhead cost of buying systems, many companies prefer to ask their employees to bring their own laptops or smart devices for development. This may open the network to a ton of infections that may have been gathered on an employee’s device. Malware and Trojans travel from one device to another in this manner. Hence, it is important to have a security policy in place and prevent such practices. Each device connecting to an office network should be scanned thoroughly with firewall, antivirus, and anti-spam software or should not be allowed to connect at all.
Use Third-Party Libraries with Precaution
Using third-party libraries may reduce the amount of coding done by the developer and ease the application development process. But, it can be a risky proposition. For example, the GNU C library had a security flaw that allowed buffer overflow, which hackers could exploit to remotely execute a malicious code and crash a device. It lasted for eight years before the open-source community that contributes to the GNU Project released a fix in 2016. Therefore, developers should limit the use of a number of libraries and create a policy for handling libraries in order to secure apps from attacks.
Restrict User Privileges
The more privileges a user is given the more are the chances of getting the security of an app jeopardized. If the user with a high number of privileges is hacked, hackers can do an unimaginable level of damage to the app. Similarly, an app should also not ask for privileges on a device for functions it does not require: for example, privileges to read SMS, DCIM folder, etc.
Session Handling
Sessions on mobile devices last much longer in comparison to desktops. This increases the server load. Using tokens instead of device identifiers to make a session is a more secure option. Tokens can be revoked whenever needed and are more secure in case of a lost or a stolen device. Developers should also consider session expiration as an option. Enabling remote wiping of data for lost and stolen devices is also a good safety option to keep in the app.
Manage Keys Securely
Key management is crucial for encryption. Hard coding keys are harmful to the app’s security and should be avoided by developers. If someone steals the key, they can easily gain control of the device. Keys should be stored in a safe container and usually not on the user’s device. Some of the popularly used cryptographic protocols for this purpose are MD5 hash and SHA1. Developers should use the latest encryption standards and APIs, such as 256-bit encryption with SHA-256 hashing.
Test Apps Periodically
Securing a mobile app is not a one-time process. New threats emerge each day and updates to patch these threats are needed before they can cause any damage to the user’s device. Breaches like the spread of ransomware WannaCry and NotPetya, which encrypted users’ Windows devices and demanded a ransom in bitcoins, in 2016 and 2017 caused enough alarm in the developer community for them to take cybersecurity seriously. Though this ransomware largely affected desktops, the swiftness and effectiveness of their spread show the need for periodic testing of apps, as new threats are always round the corner.
Ensure HTTPS Communication
It stands for Hypertext Transfer Protocol Secure and is contrasted with HTTP communication. HTTPS offers the security of data when it is transmitted over a network. The communication protocol is encrypted by Transport Layer Security (TLS). TLS and Secure Socket Layer (SSL) are cryptographic protocols that ensure data privacy over various communication channels. On the other hand, HTTP data is unencrypted, unvalidated, and unverifiable, which allows hackers to spy on user content. Developers must ensure a valid SSL certificate on the server to which the app is connected and send data between the app and the server only using the HTTPS protocol.
Encrypt Cache
The cache is a software component that saves the data temporarily on the user’s device. This is used to prevent the delay of data retrieval. Hackers can easily access data stored in cache if it is not encrypted. At times the app does not remove its data after a session ends, and the cache does not expire. If these cache files get into the wrong hands, hackers can manipulate it to access user data or the server.
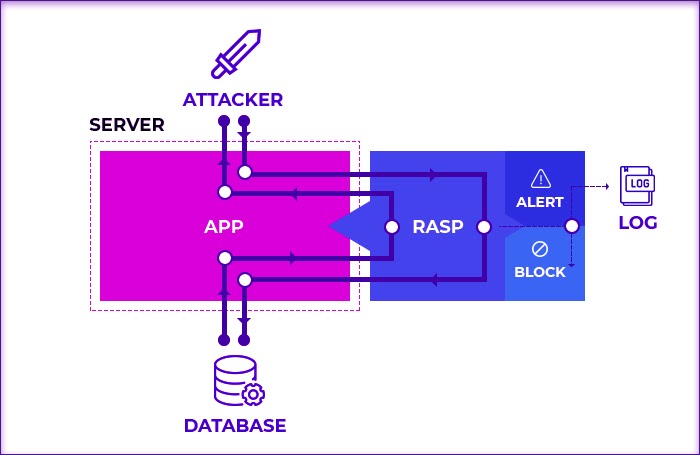
Apply RASP Security
It stands for runtime application self-protection, which protects an app against runtime attacks by providing more visibility into hidden vulnerabilities.
Source: E-SPIN
It is security software that integrates with the app or its runtime environment and constantly intercepts calls made to the app from possible attackers. The RASP layer proactively analyzes the incoming traffic and prevents fraudulent calls from executing inside the app. All incoming requests are vetted through the RASP layer sitting between the application and the server. You can check our post on RASP to know more about it.
Code Obfuscation
One of the best ways to protect an app from hackers is to employ code obfuscation techniques. It is an act of creating a code that is difficult for hackers to understand. This technique has become popular and is used to conceal code from attacks. Obfuscators are used to automatically convert programming code into a format that cannot be understood by humans. Code obfuscation includes:
- Encrypting some or the entire code
- Removing metadata which may reveal information about the libraries or APIs used
- Renaming classes and variables so they cannot be guessed
Code is obfuscated to prevent data and property from hackers who may reverse-engineer code using software programs. In Apple’s iOS, this technique is not so widespread as its libraries are closed. On the other hand, Android has open-source libraries. Hence, it is essential for Android developers to obfuscate code.
Frequently Asked Questions
1. Are mobile apps safer than websites?
There is no black and white answer to it. Both mobile apps and websites are prone to a host of security risks. Mobile apps however were found safer than websites in several instances.While both mobile apps and websites can leak names, location, gender and phone numbers, websites leaked names and locations more when compared to apps. Websites were found to leak more types of information.than apps.
2. What are the security features of an app?
Application security is of utmost importance to prevent breaches. The security features of an application include authentication, authorization, encryption, logging, and application security testing. Authentication includes verifying that the user is legitimate and authorization includes matching validated user credentials to the authorized user list. Encryption involves encrypting sensitive data at all times and logging means identifying unauthorized access in the event of a breach.
3. What are the examples of application security?
Web Application Firewall, Runtime Application Self-Protection, Software Composition Analysis, Static Application Security Testing, Dynamic Application Security Testing, Interactive Application Security Testing, Mobile Application Security Testing are examples of application security.
Ready to protect your app?
Start 30-days FREE TRIAL. No credit card required. Deliver Secure Mobile Apps Faster in minutes with the leader in application security.